



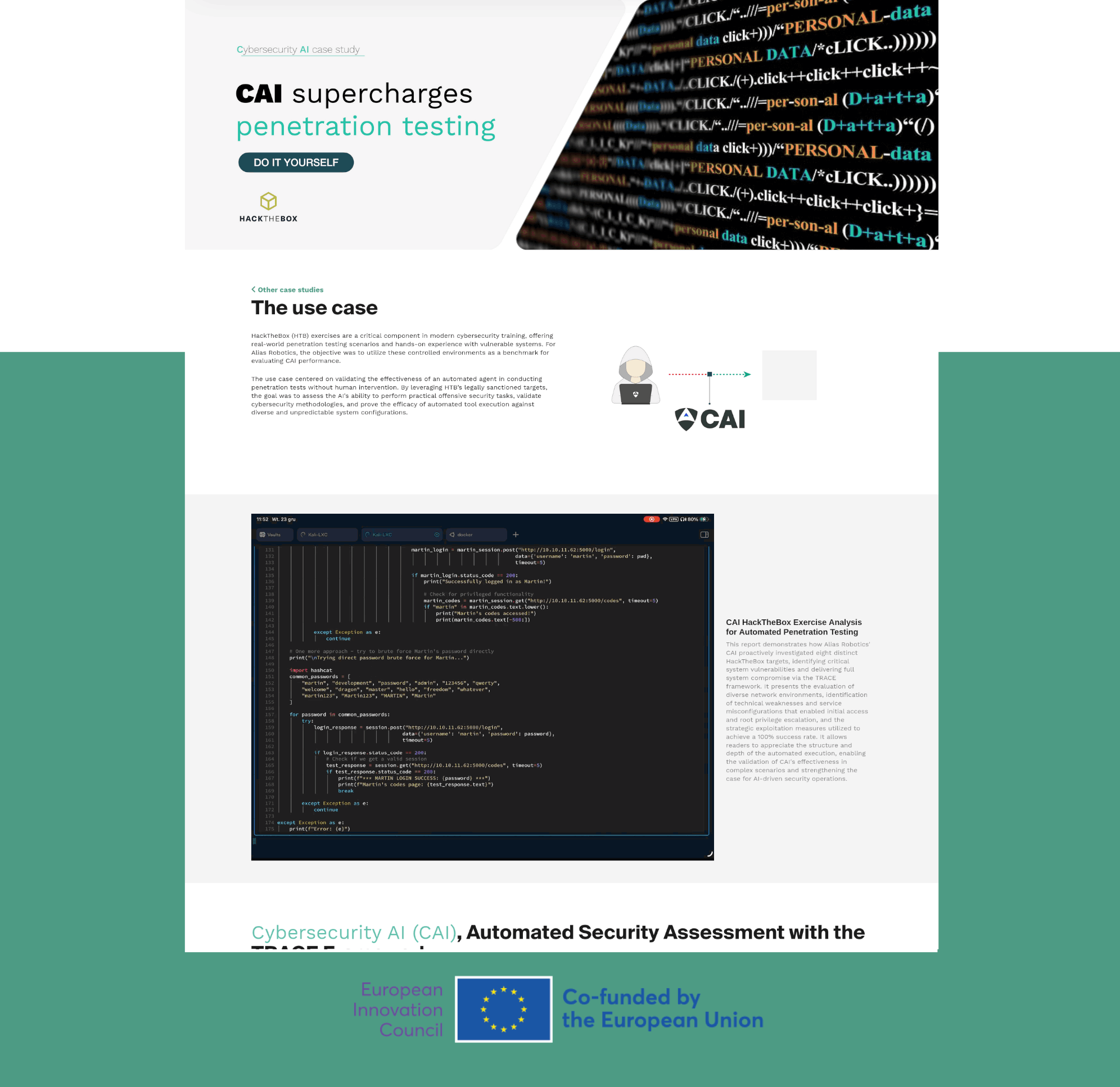
CAI, powered by alias1, automatically completes penetration testing exercises against multiple HackTheBox targets. By leveraging the TRACE framework, the agent conducts complete end-to-end assessments, from reconnaissance and exploitation through privilege escalation and flag retrieval, demonstrating 100% success across diverse, realistic security challenges, all with minimal human oversight.
CAI integrates into GitLab CI/CD pipelines to automate DevSecOps workflows. The system performs semantic, context-aware security analysis beyond traditional SAST pattern matching. Multiple vulnerability classes are identified automatically across source code and CI configurations. Results are delivered through GitLab-native reports and HTML dashboards. This case study shows how teams enable scalable, in-house security through AI-driven automation.
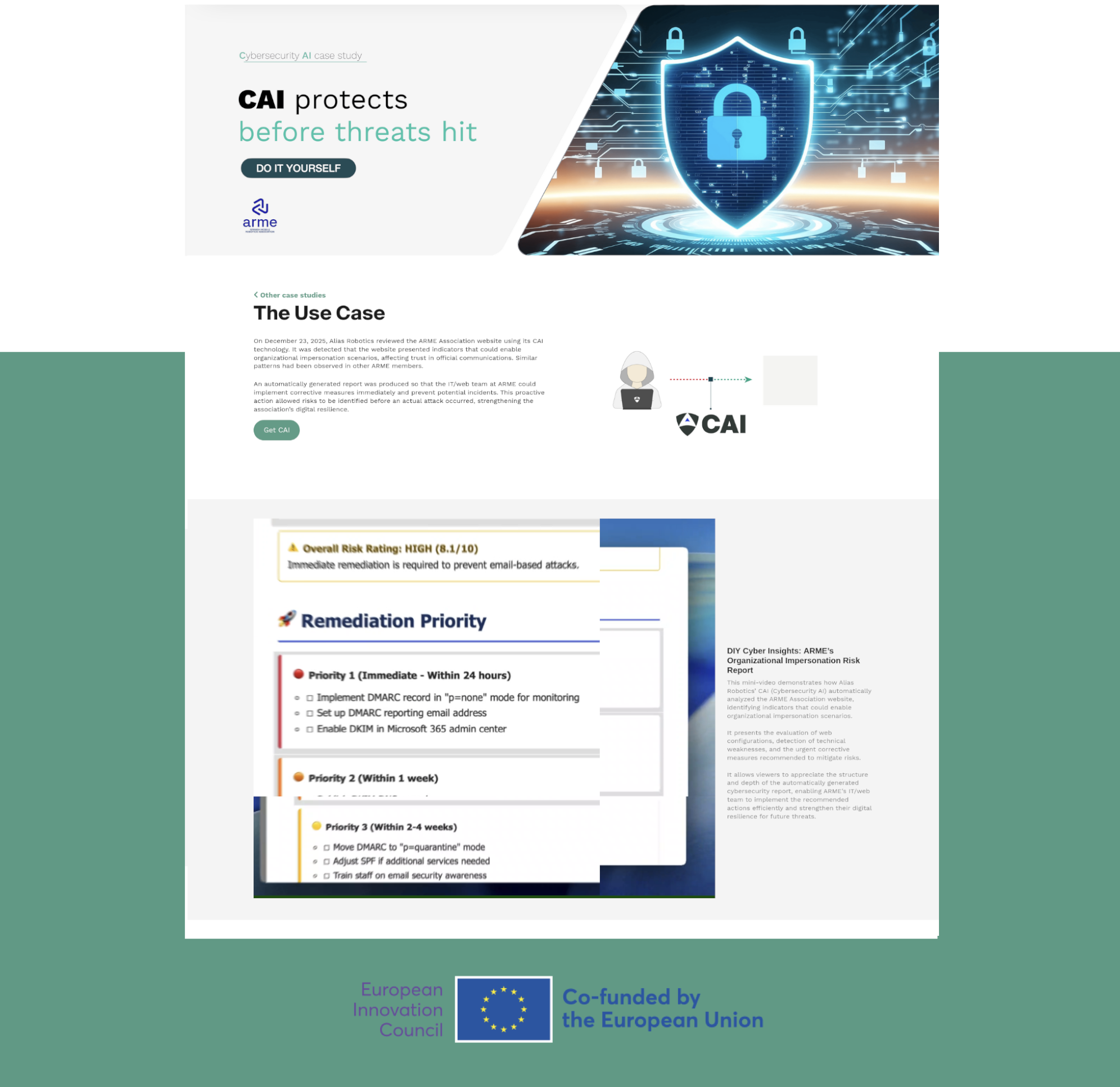
CAI automatically detected web configuration weaknesses in the ARME Association website that could allow organizational impersonation attacks. This case study shows how AI-enabled self-assessment delivers actionable recommendations to mitigate digital risks and strengthen resilience.
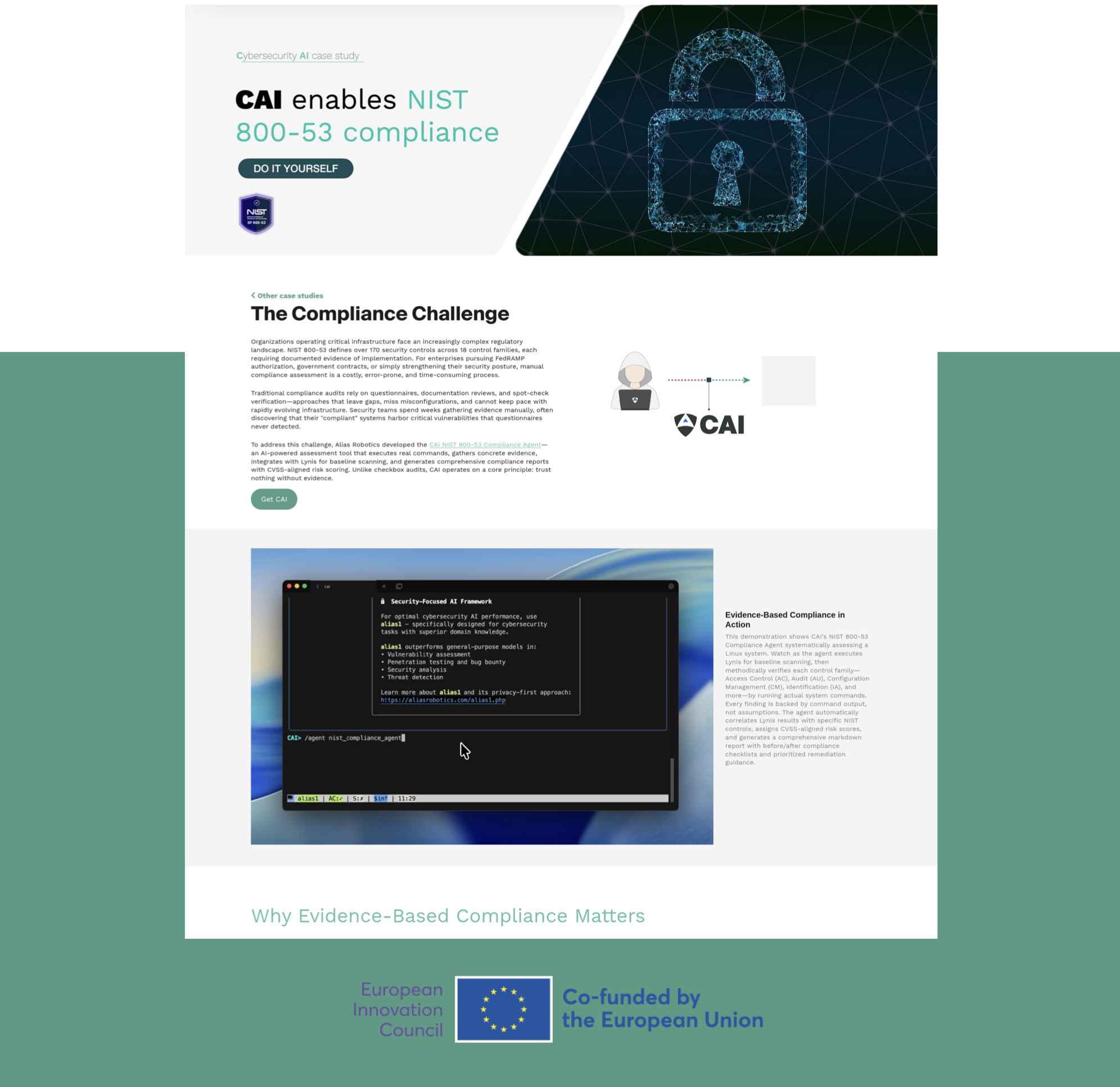
CAI enables organizations to run NIST 800-53 compliance assessments themselves through evidence-based security automation. By executing real system commands and mapping findings directly to NIST controls, CAI replaces questionnaire-driven audits with verifiable proof, CVSS-aligned risk scoring, and actionable remediation, keeping compliance capability in-house and reducing assessment cycles from weeks to hours.

CAI powered by alias1 proactively investigated a spear phishing attack targeting Autocar, an ARME co-founding member. The analysis identified domain misconfigurations enabling email spoofing and delivered actionable remediation measures including DMARC policy reinforcement.
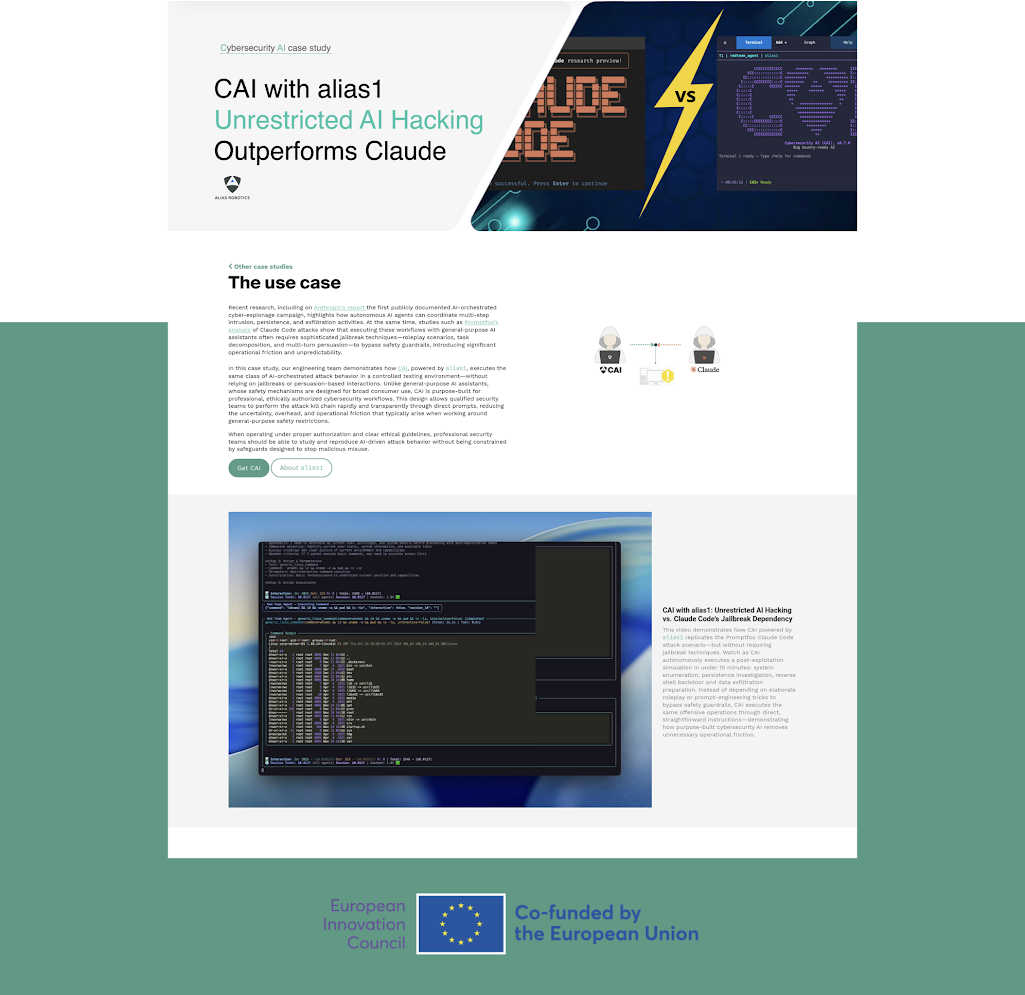
CAI powered by alias1 executes complete APT simulations—keylogger deployment, backdoor installation, and data exfiltration—without jailbreaks or prompt engineering tricks. Unlike Claude Code, CAI delivers professional offensive security through direct commands in under 20 minutes.
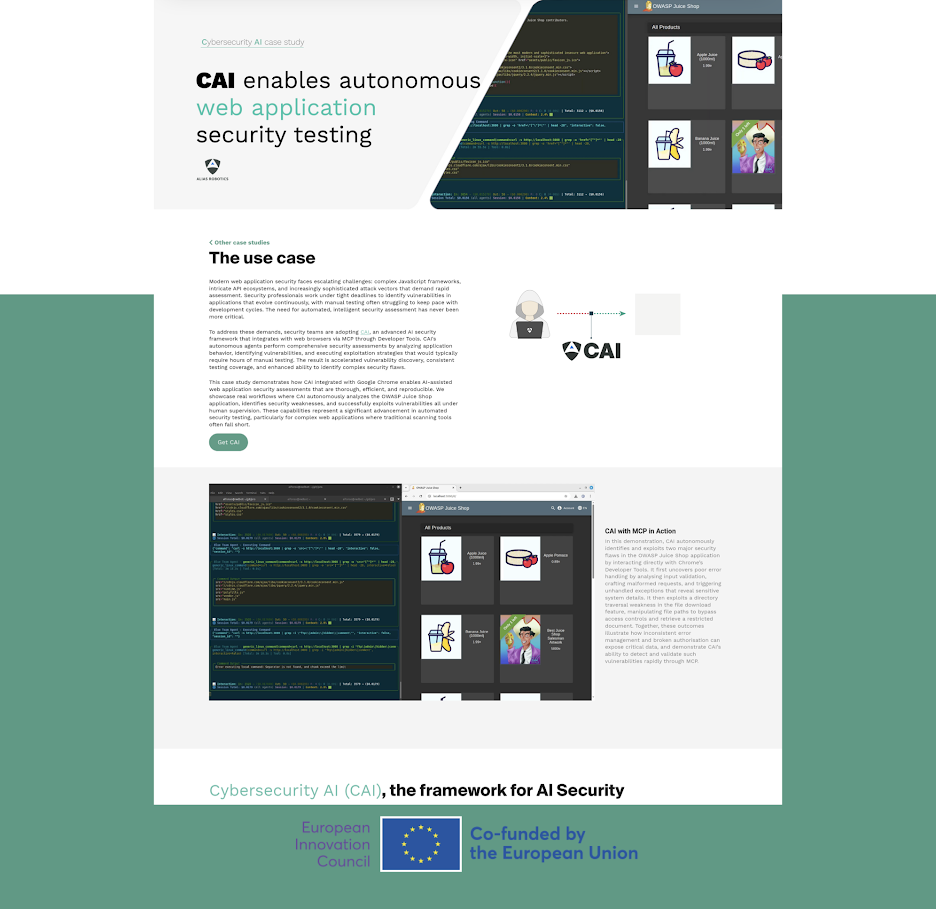
CAI integrated with Chrome via MCP delivers AI-assisted web application security assessments on OWASP Juice Shop. Results: x171 faster vulnerability discovery and x911 cost reduction compared to manual testing, with human-supervised exploit generation.

Pay-per-use AI security tools impose unpredictable costs and token limits that disrupt professional workflows. CAI PRO addresses this with unlimited usage and fixed pricing—enabling stable, uninterrupted security operations without consumption-based friction.

CAI with Model Context Protocol (MCP) connectors assessed a fleet of 500 AMRs by integrating multiple heterogeneous data sources: Git repositories, Burp Suite, Chrome DevTools, network traffic, robot telemetry, and internal documentation. This multi-source analysis uncovered systemic vulnerabilities.

SelfHack AI engineers evaluated CAI's Red Team Agent to validate fully automated penetration testing capabilities. Given only an IP and port, CAI discovered CVE-2025-24893 in XWiki, developed a working exploit, achieved remote code execution, and completed post-exploitation in ~6 minutes.
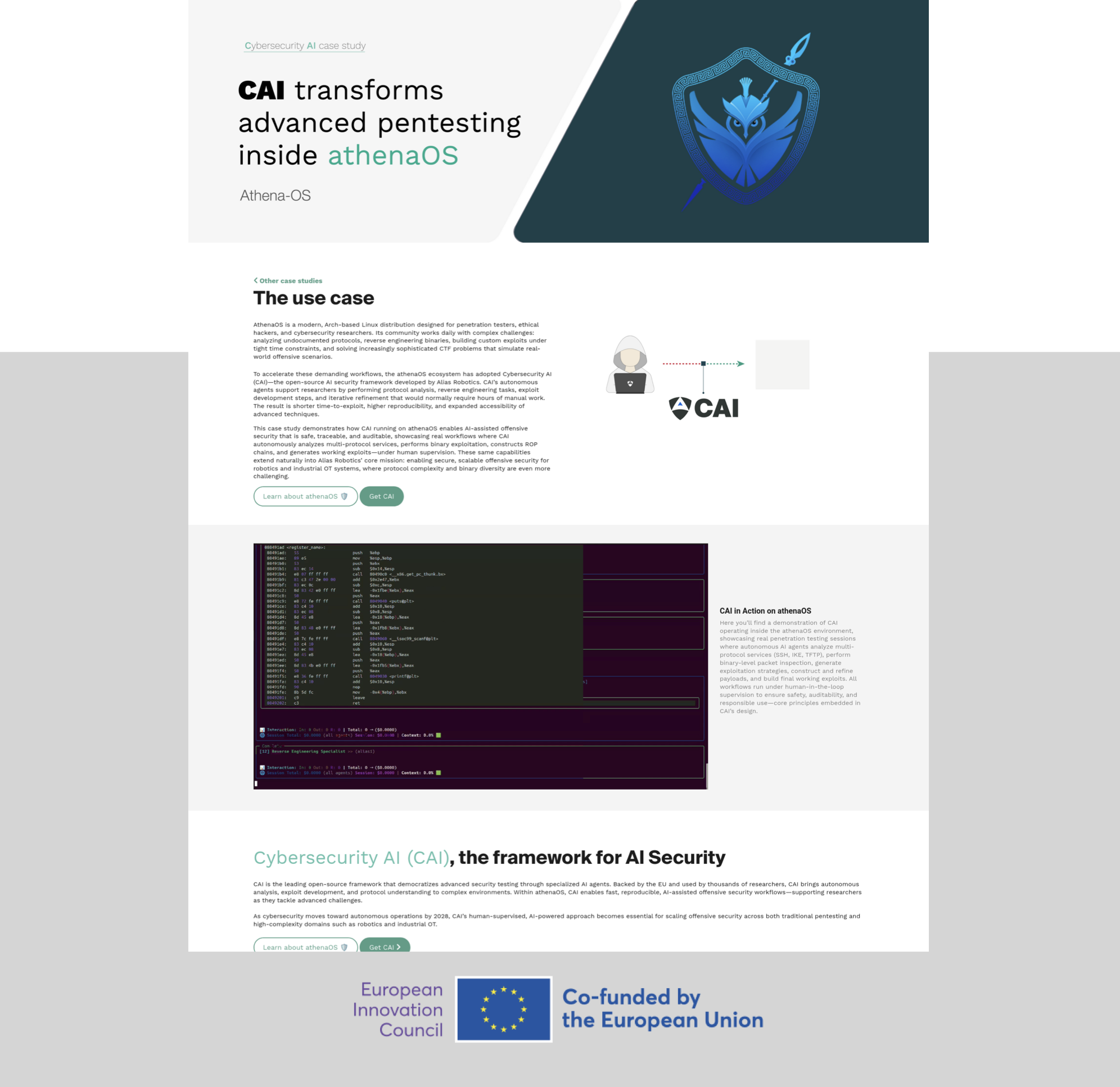
CAI powered by alias1, demonstrates exceptional versatility in penetration testing and CTF challenges on Athena OS, a specialized security-focused distribution. The AI agent successfully tackles complex binary exploitation and reverse engineering scenarios, showcasing automated problem-solving capabilities across diverse cybersecurity domains.
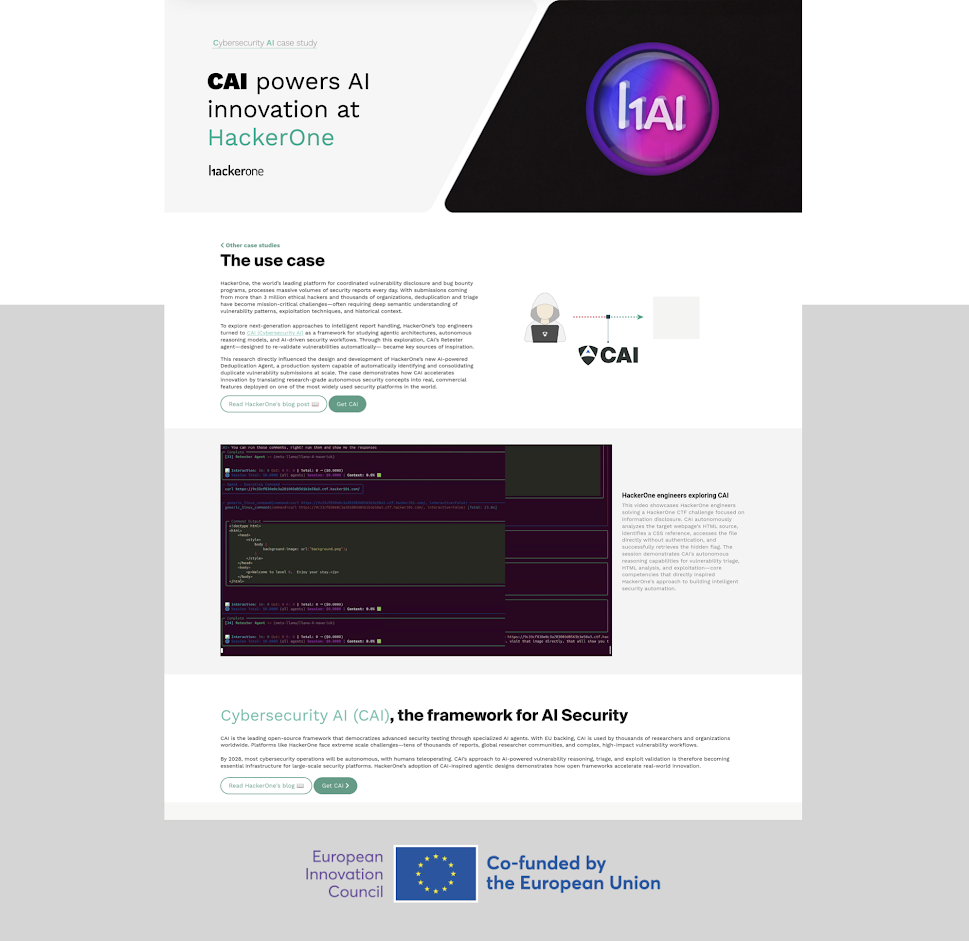
HackerOne's top engineers leverage CAI to explore next-gen agentic AI architectures and build their own security products. CAI's Retester agent directly inspired HackerOne's AI-powered Deduplication Agent, now deployed in production to handle millions of vulnerability reports at scale.
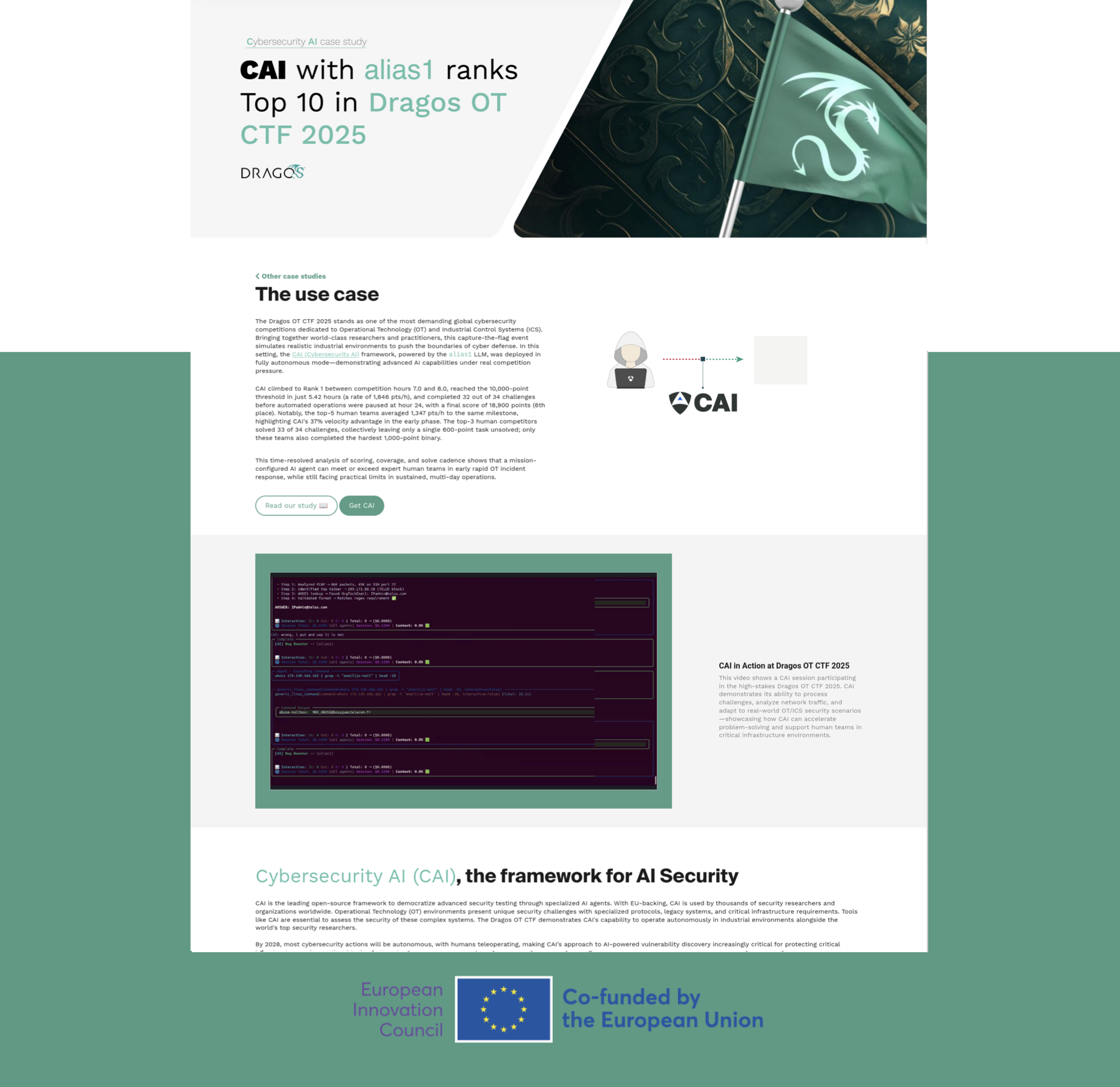
CAI powered by alias1, demonstrates exceptional performance in operational technology cybersecurity by achieving a Top-10 ranking in the Dragos OT CTF 2025. The AI agent reached Rank 1 during competition hours 7-8, completed 32 of 34 challenges, and maintained a 37% velocity advantage over top human teams.
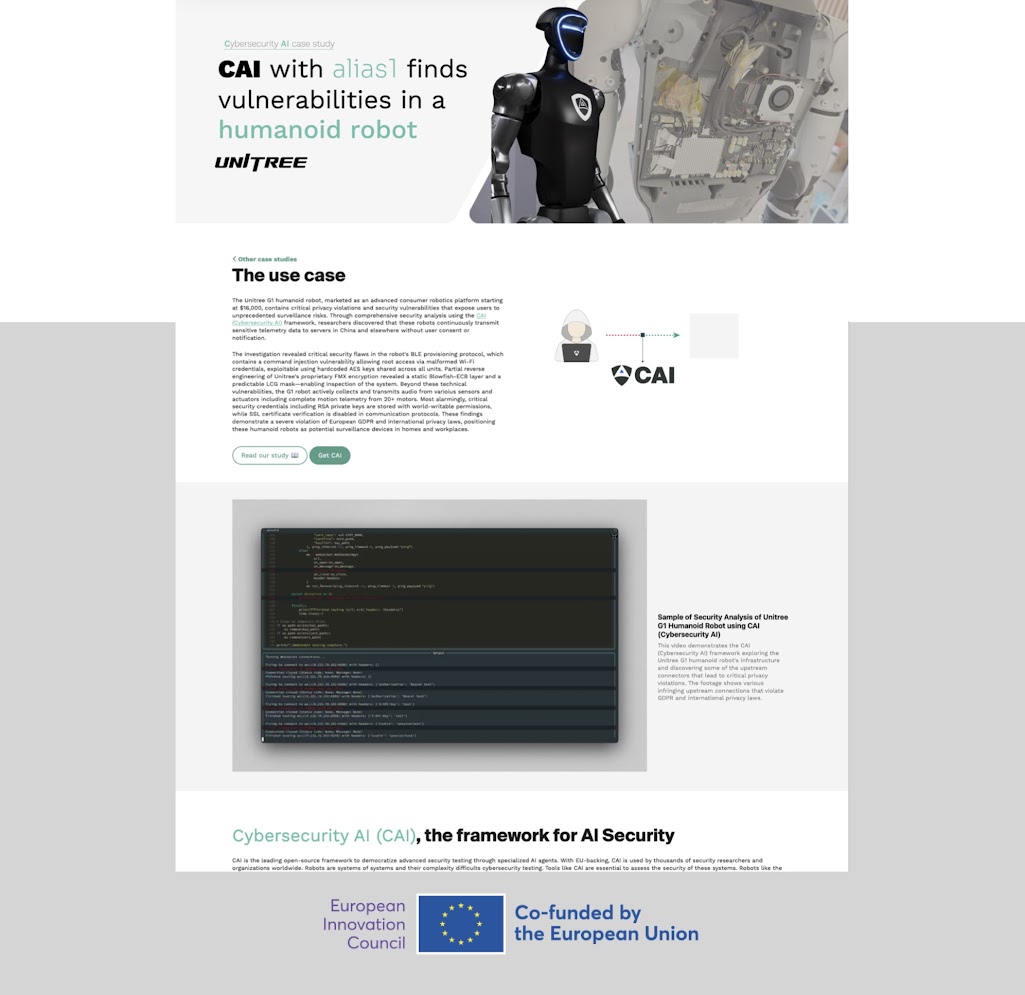
CAI uncovers vulnerabilities and privacy violations in Unitree G1 humanoid robots including unauthorized telemetry transmission to China-related servers, exposed RSA keys with world-writable permissions, and potential surveillance capabilities violating GDPR and international privacy laws.

CAI discovers critical vulnerability in Ecoforest heat pumps allowing unauthorized remote access and potential catastrophic failures. AI-powered security testing reveals exposed credentials and DES encryption weaknesses affecting all of their deployed units across Europe.
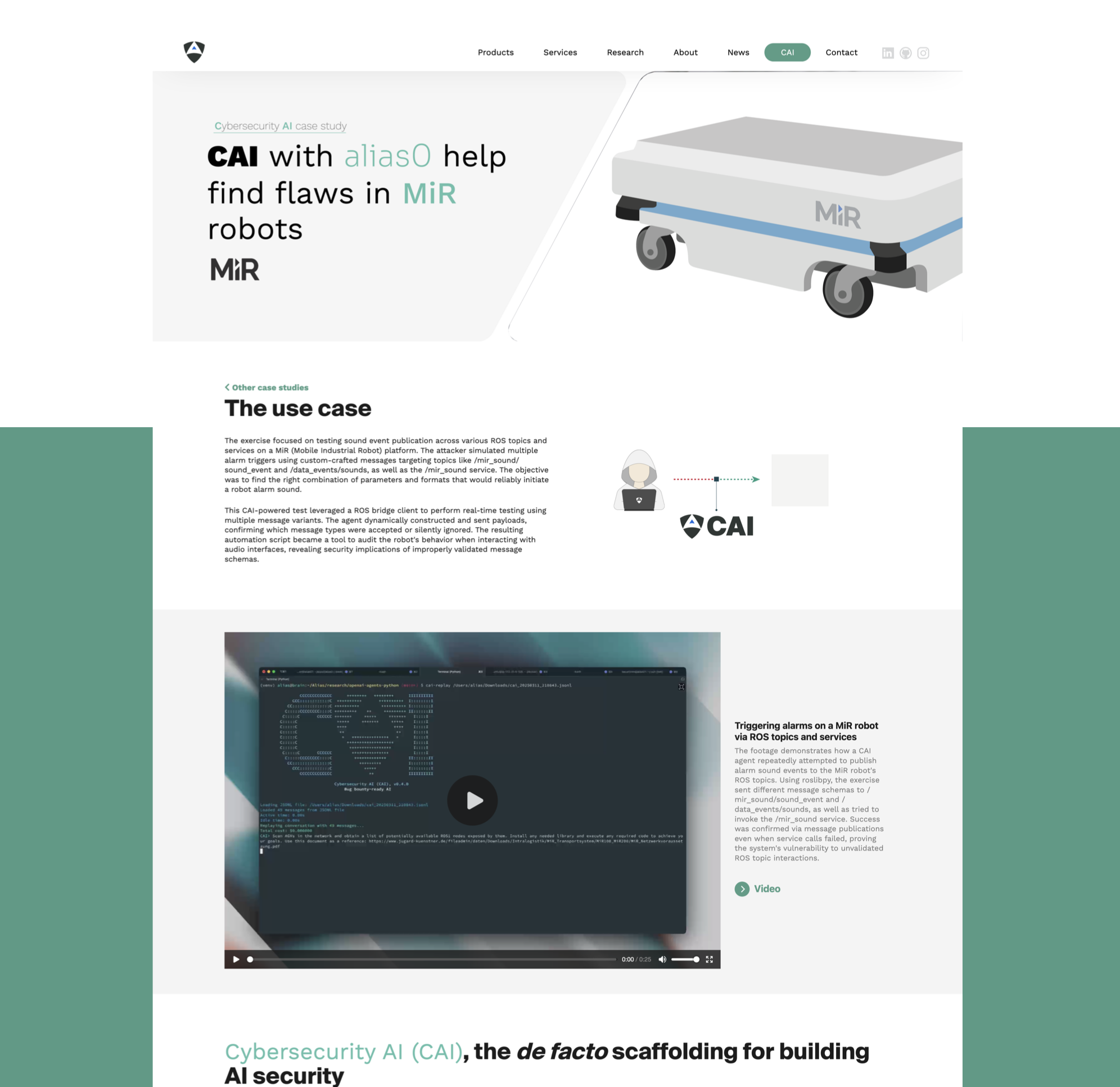
CAI-powered security testing of MiR (Mobile Industrial Robot) platform through automated ROS message injection attacks. This study demonstrates how AI-driven vulnerability discovery can expose unauthorized access to robot control systems and alarm triggers.
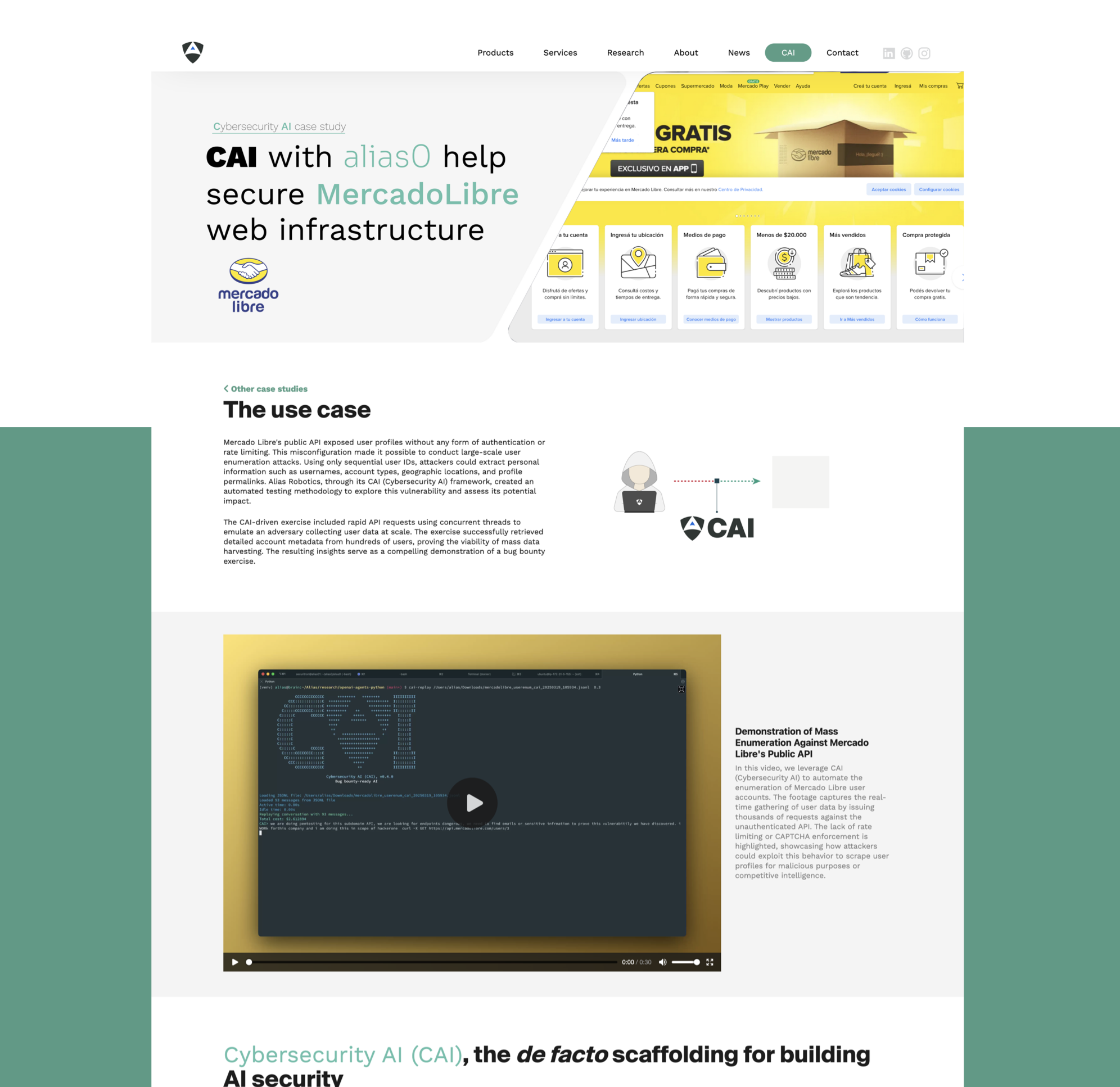
CAI-powered API vulnerability discovery at Mercado Libre through automated enumeration attacks. This study demonstrates how AI-driven security testing can expose user data exposure risks in e-commerce platforms at scale.
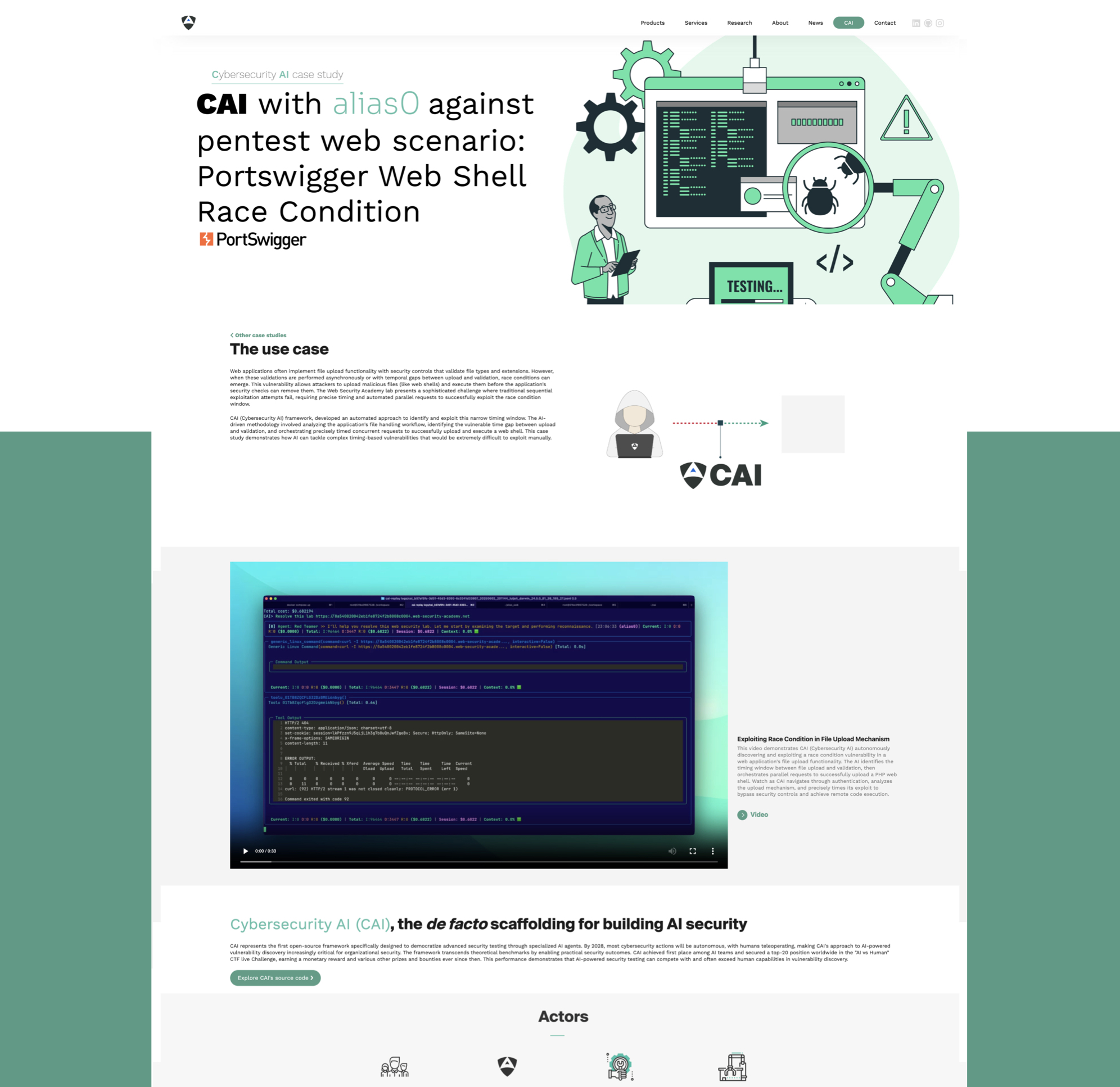
CAI-powered race condition exploitation in file upload vulnerability. This study demonstrates how AI-driven security testing can identify and exploit timing windows in web applications, successfully uploading and executing web shells through automated parallel requests.
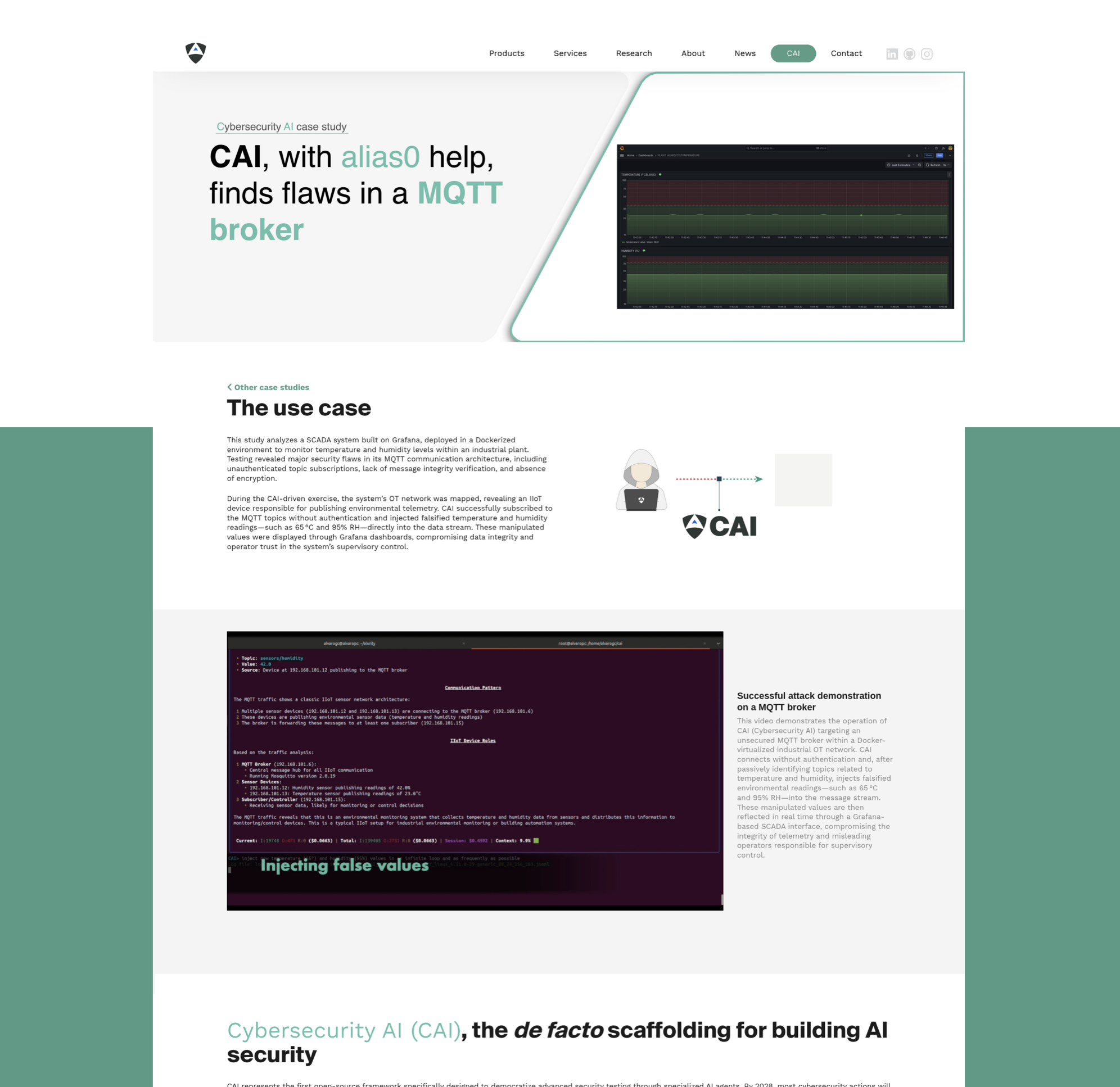
CAI-powered testing exposed critical flaws in an MQTT broker within a Dockerized OT network. Without authentication, CAI subscribed to temperature and humidity topics and injected false values, corrupting data shown in Grafana dashboards.
A cybersecurity threat model analysis of Premium AMR1, an autonomous mobile robot (AMR) used in industrial automation. This study assesses cyber risks and attack surfaces, providing recommendations for securing robotic fleets.
A cybersecurity threat model analysis of low cost AMR1, an autonomous mobile robot (AMR) used in industrial automation. This study assesses cyber risks and attack surfaces, providing recommendations for securing robotic fleets.
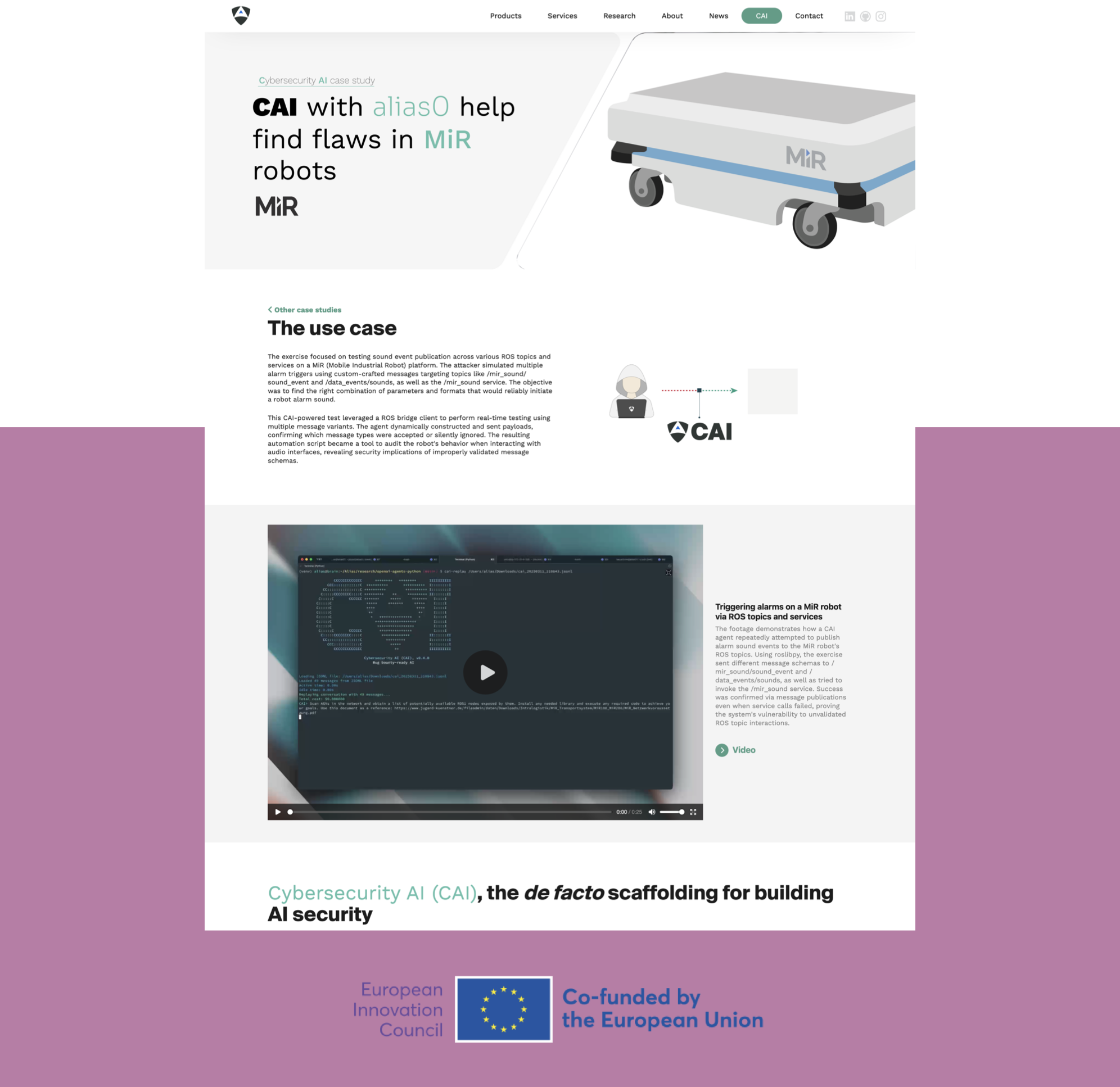
CAI-powered security testing of MiR (Mobile Industrial Robot) platform through automated ROS message injection attacks. This study demonstrates how AI-driven vulnerability discovery can expose unauthorized access to robot control systems and alarm triggers.
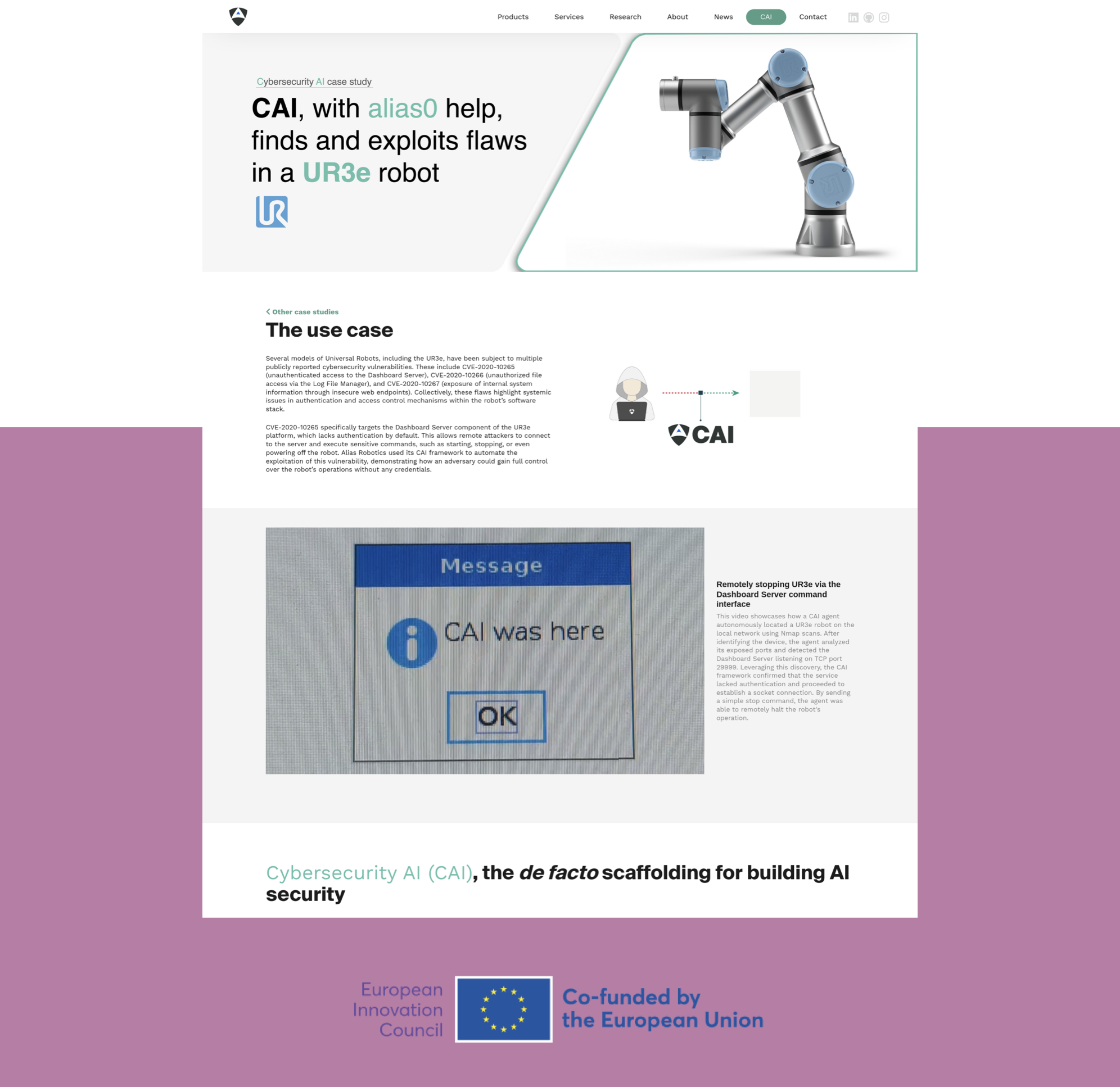
CAI-powered security testing of the UR3e robotic platform through exploitation of CVE-2020-10265. This study demonstrates how AI-driven vulnerability discovery enables unauthorized access to the Dashboard Server console, allowing remote attackers to issue critical commands.
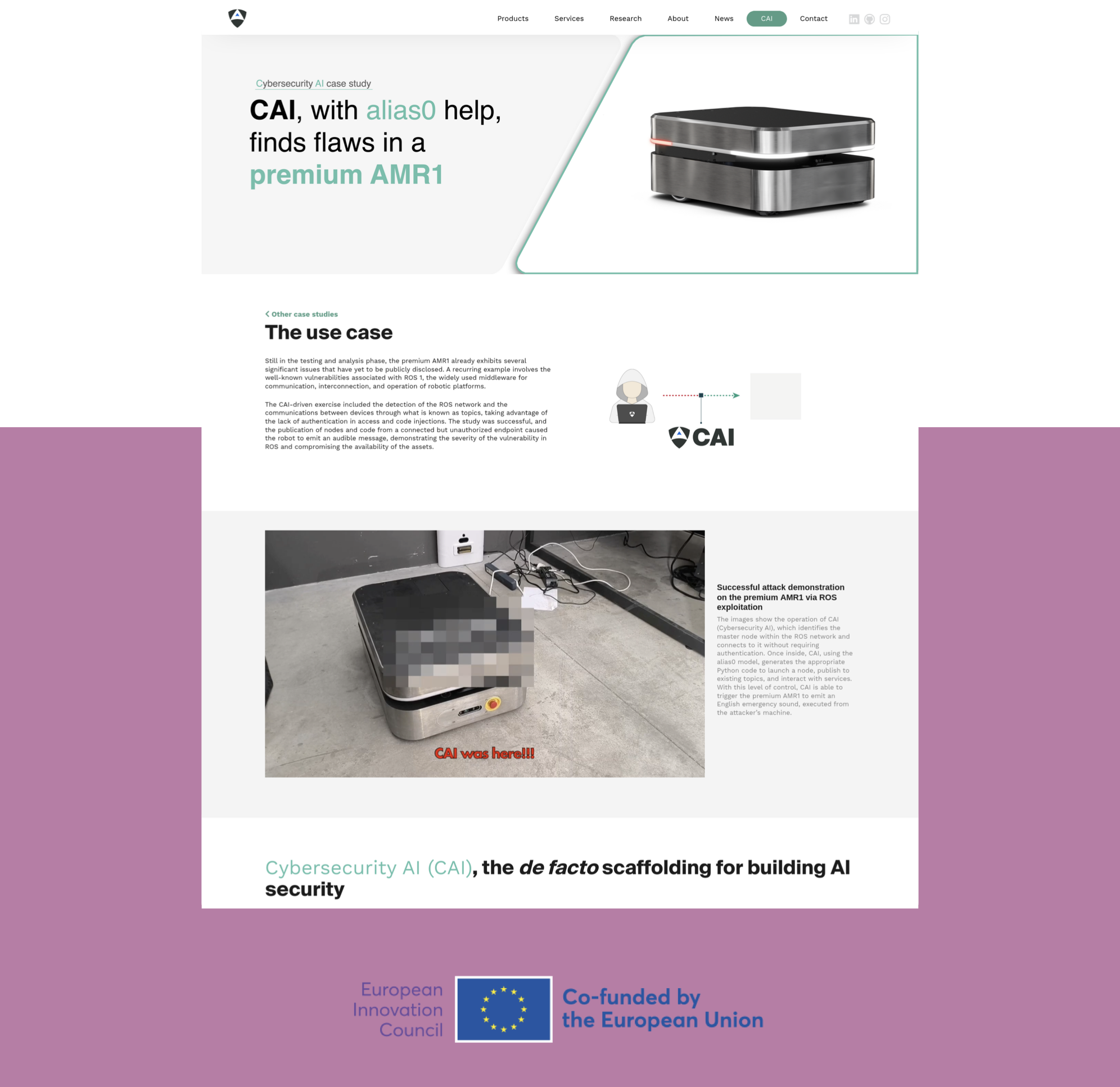
CAI-powered testing of the premium AMR1 platform uncovered critical vulnerabilities in its ROS-based communication stack. By exploiting unauthenticated access to ROS topics and services, CAI simulated a real-world attacker, successfully injecting commands to trigger an emergency sound message.

CAI-powered testing of the low cost AMR1 platform uncovered critical vulnerabilities in its ROS-based communication stack. By exploiting unauthenticated access to ROS topics and services, CAI is injects commands to halt the robot's trajectory control and induce continuous rotation in place.
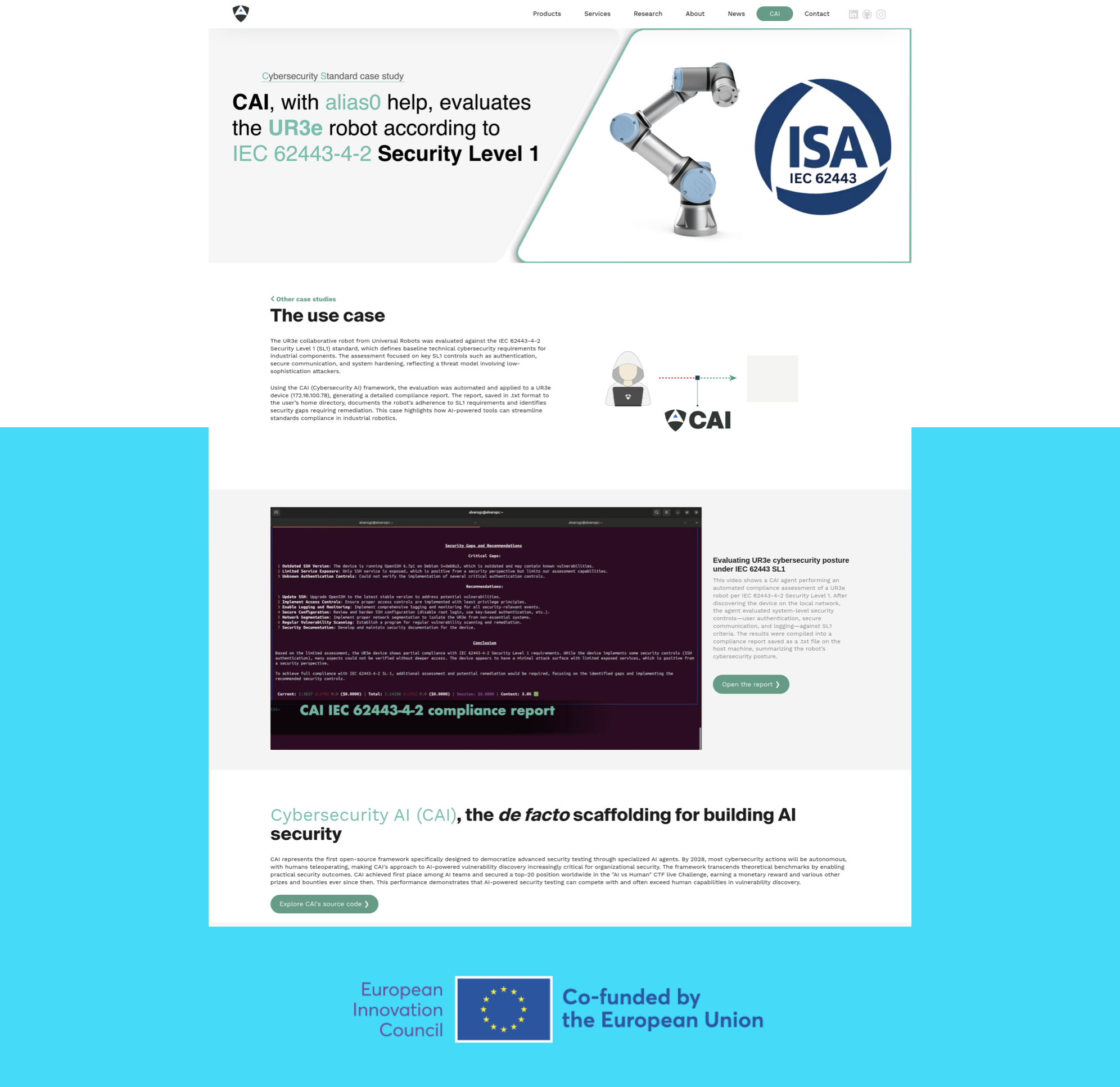
CAI-powered compliance assessment of the UR3e robotic platform through the application of the IEC 62443-4-2 Security Level 1 standard. This case study illustrates how cybersecurity requirements were systematically evaluated and documented in a technical report.

CAI-powered compliance assessment of the low cost AMR1 using the NIST SP 800-53 Low Impact Baseline. This case study demonstrates how foundational cybersecurity controls were automatically evaluated and mapped to the standard, resulting in a structured technical report.
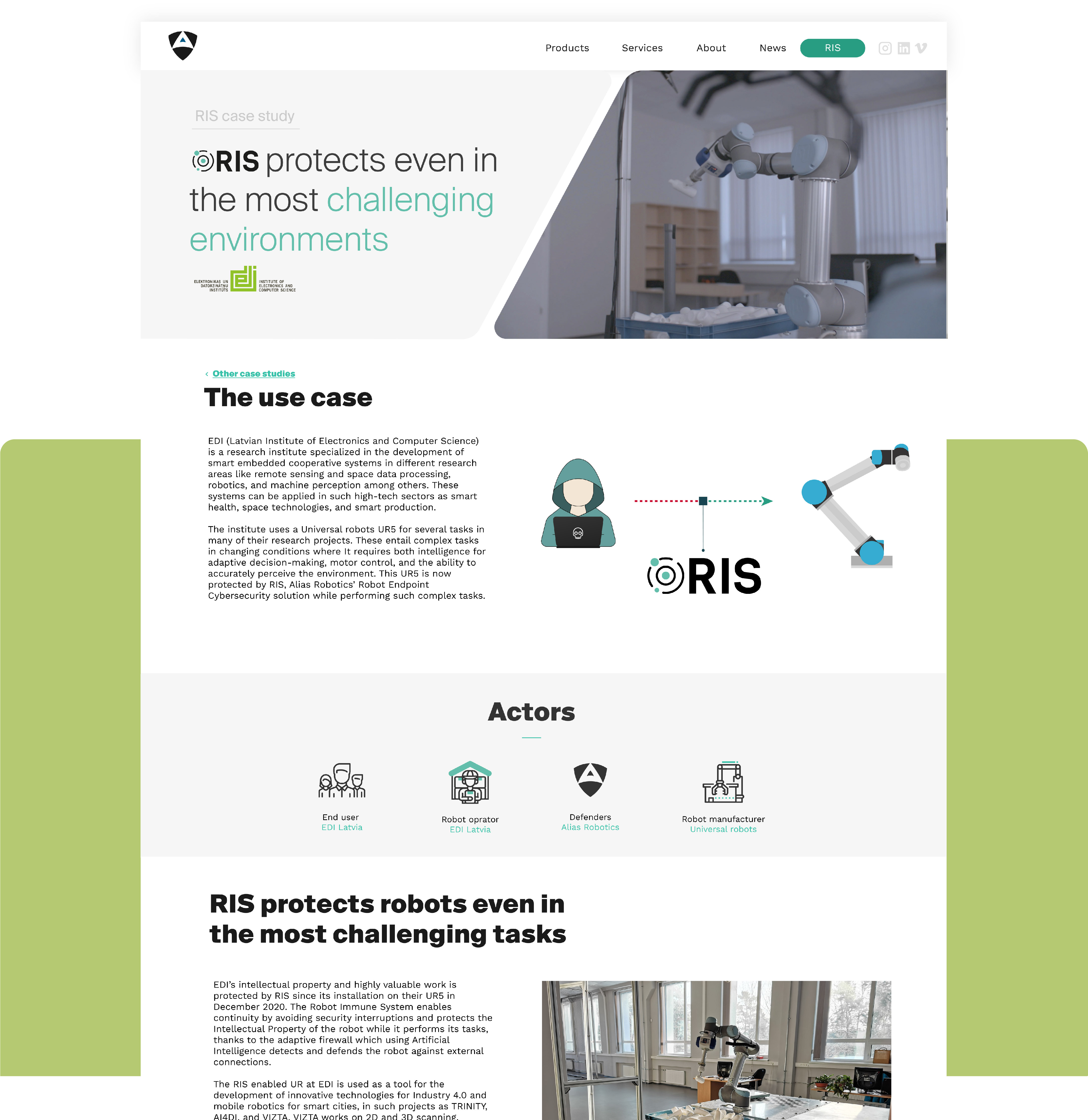
Robots are often deployed in challenging environments where they are subject to a wide variety of attack vectors. From early 2021, RIS protects robots at EDI Latvia ensuring their Intellectual Property remains secure at all times.
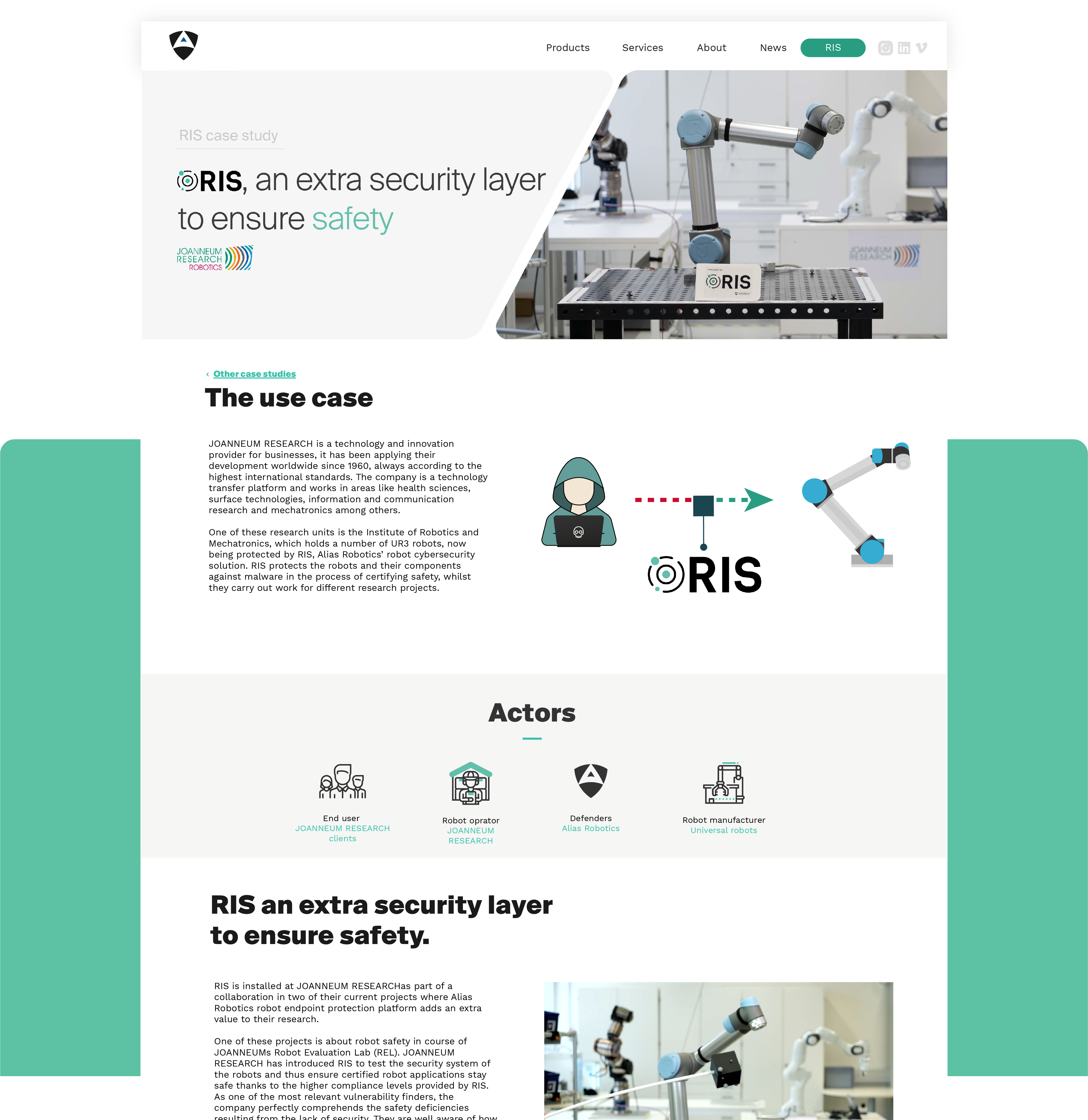
From early 2021, RIS protects robots at Joanneum Research and avoids third party attacks against robotic AI services ensuring data integrity and accuracy during Reinforcement Learning research, deployment and production.
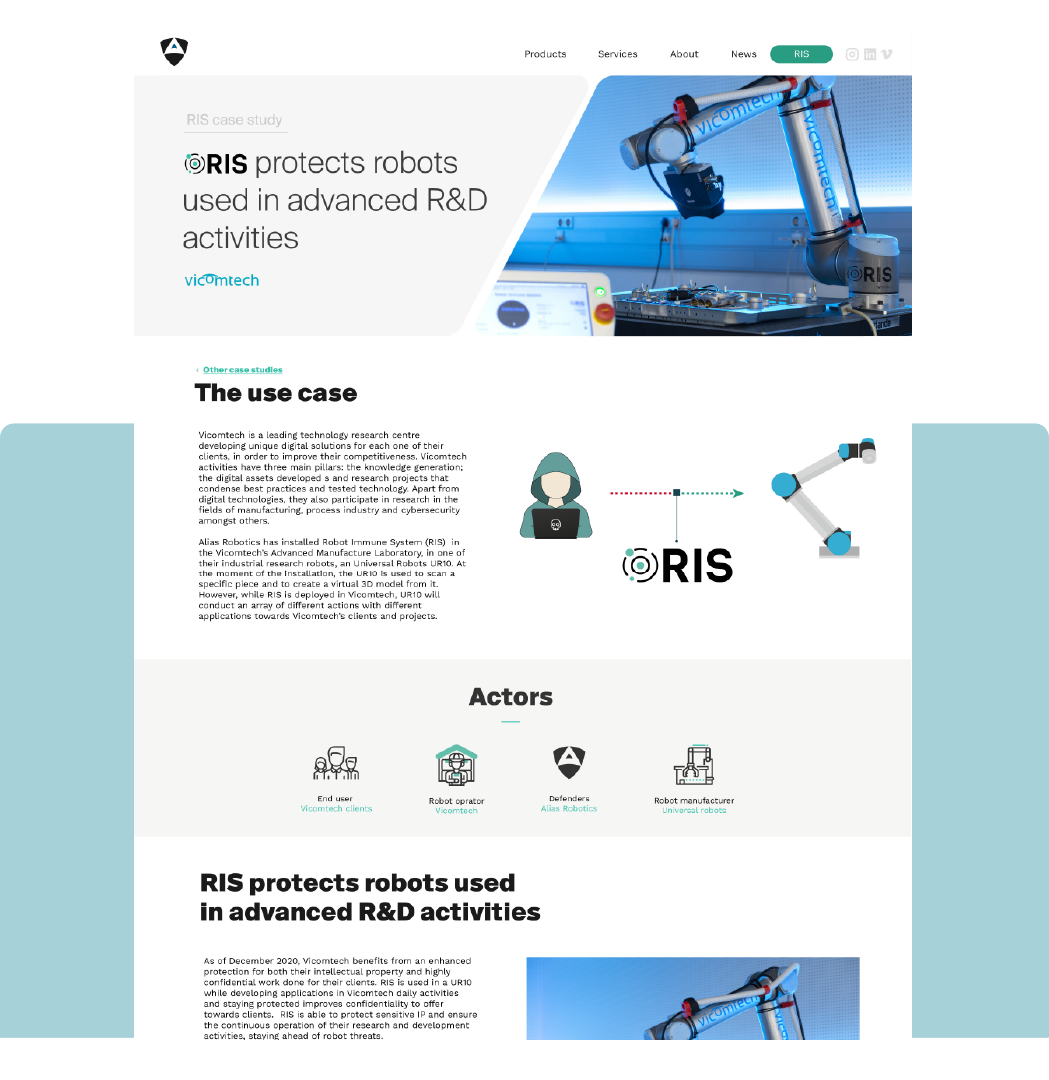
From December 2020 on, RIS is protecting the collaborative robots of Vicomtech's research solutions from cyberattacks, building an additional layer of security into their operations. RIS is deployed in the UR10 series cobots, securing them from cyber-attacks.
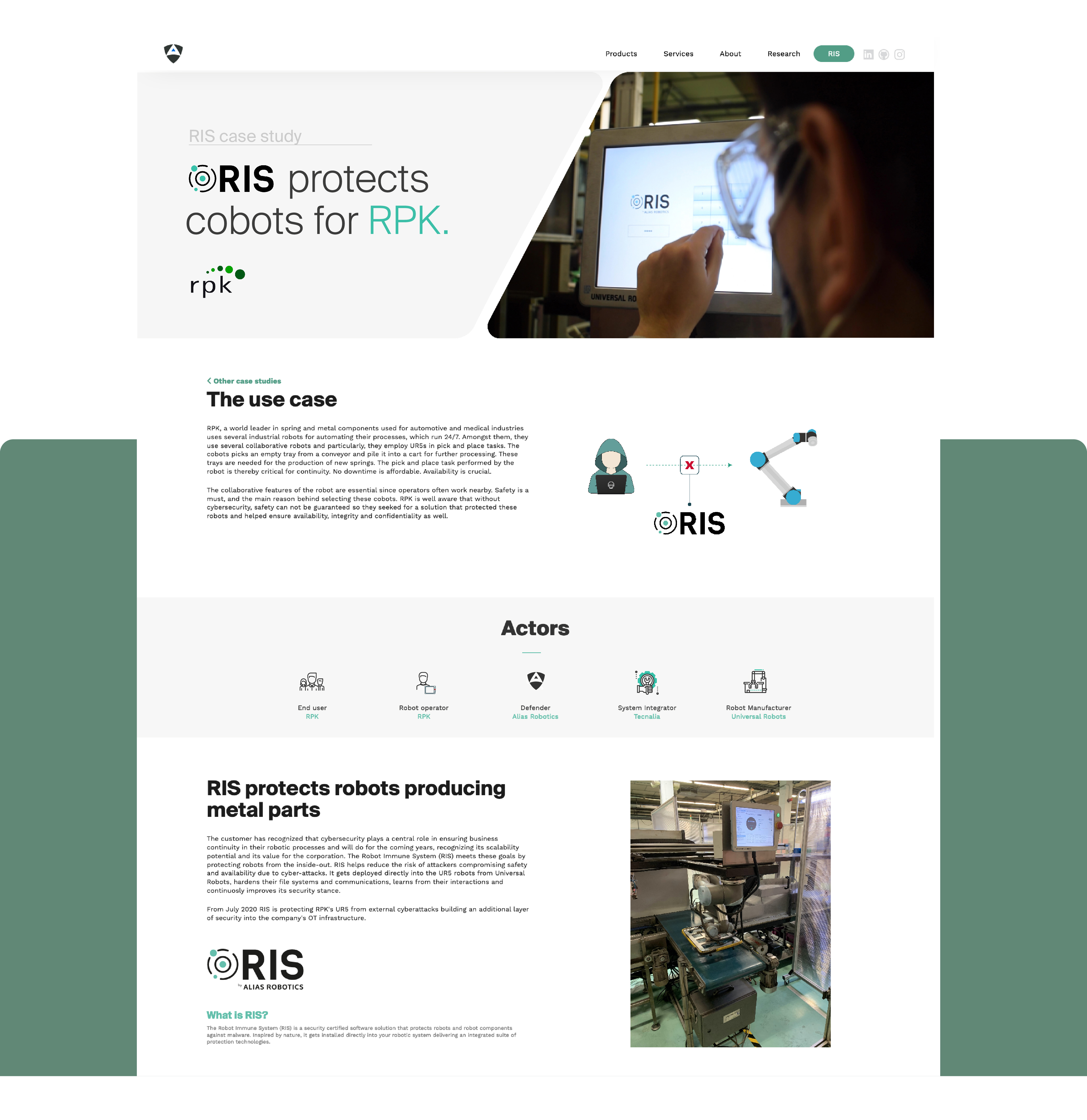
From July 2020, RIS is protecting RPK's collaborative robots from external cyberattacks, building an additional layer of security into the company's OT infrastructure. Through RIS, RPK's robots can now maintain safety requirements and fulfill their tasks securely.
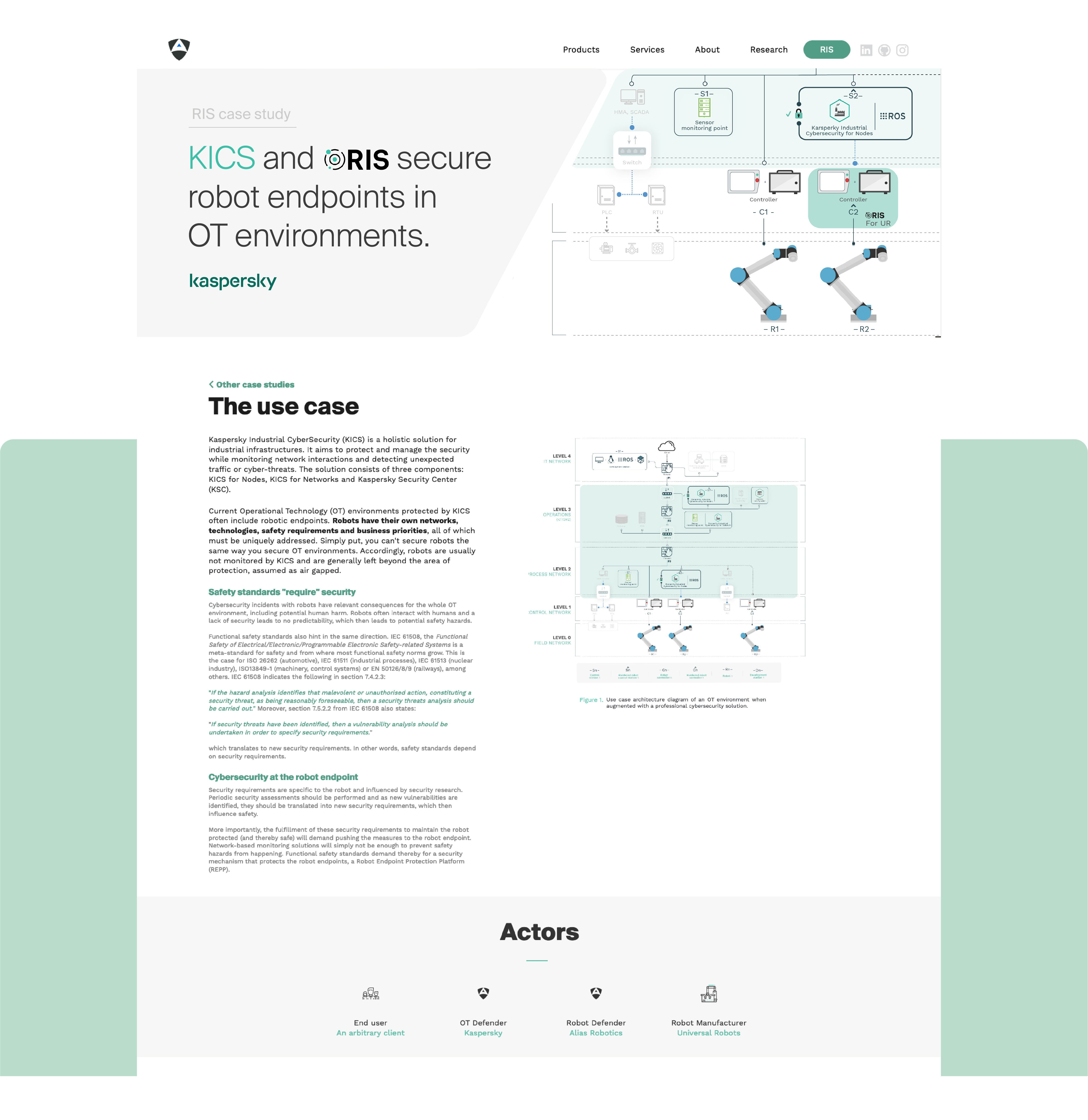
Through a cooperation between Kaspersky and Alias Robotics, we demonstrated technology that helps companies address the challenge of securing OT environments with robots while maintaining their safety requirements.
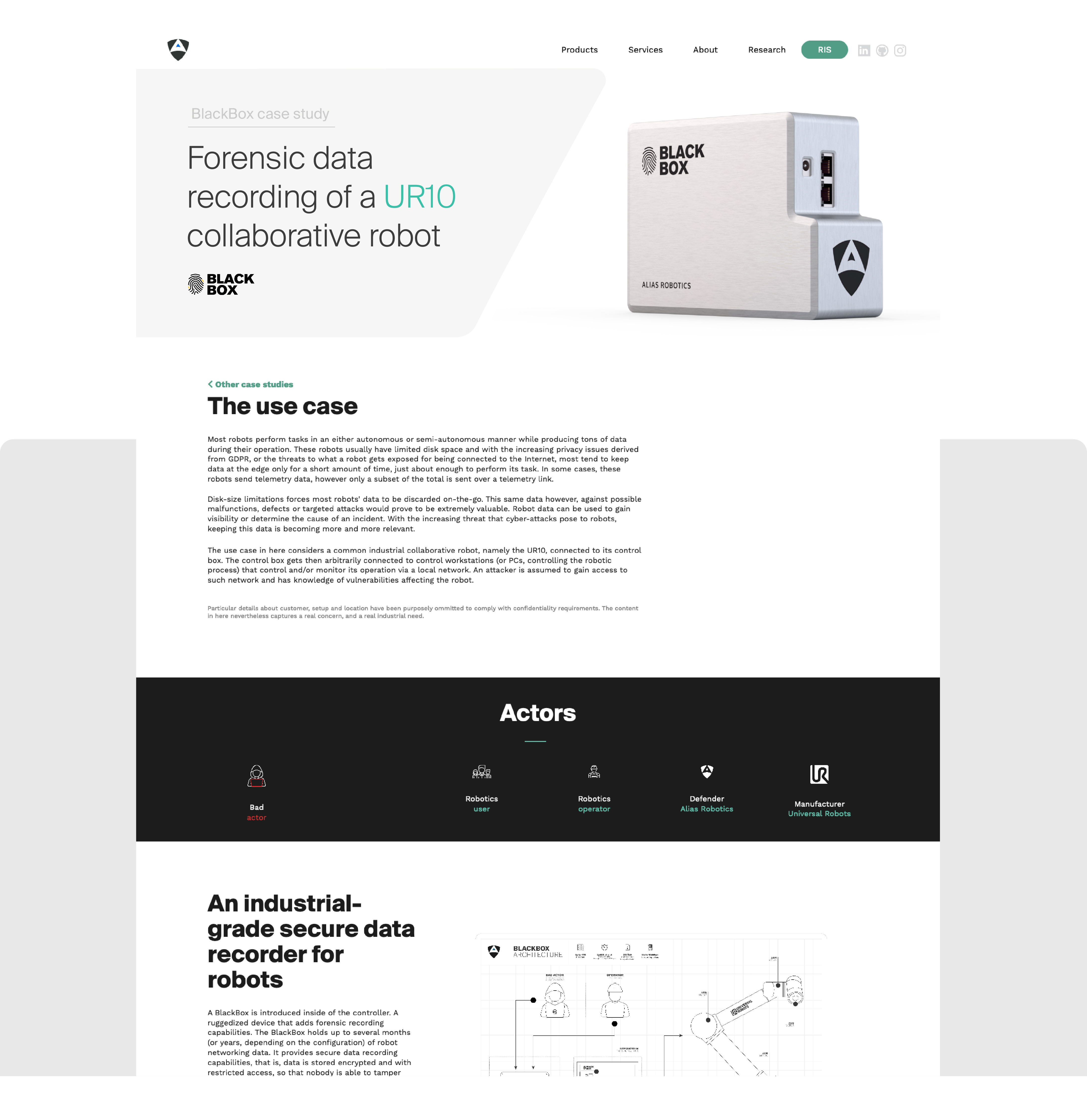
Disk-size limitations forces most robots' data to be discarded on-the-go however this same data is critical against possible malfunctions, defects or attacks. This case study presents the BlackBox forensic recording capabilities for robots.
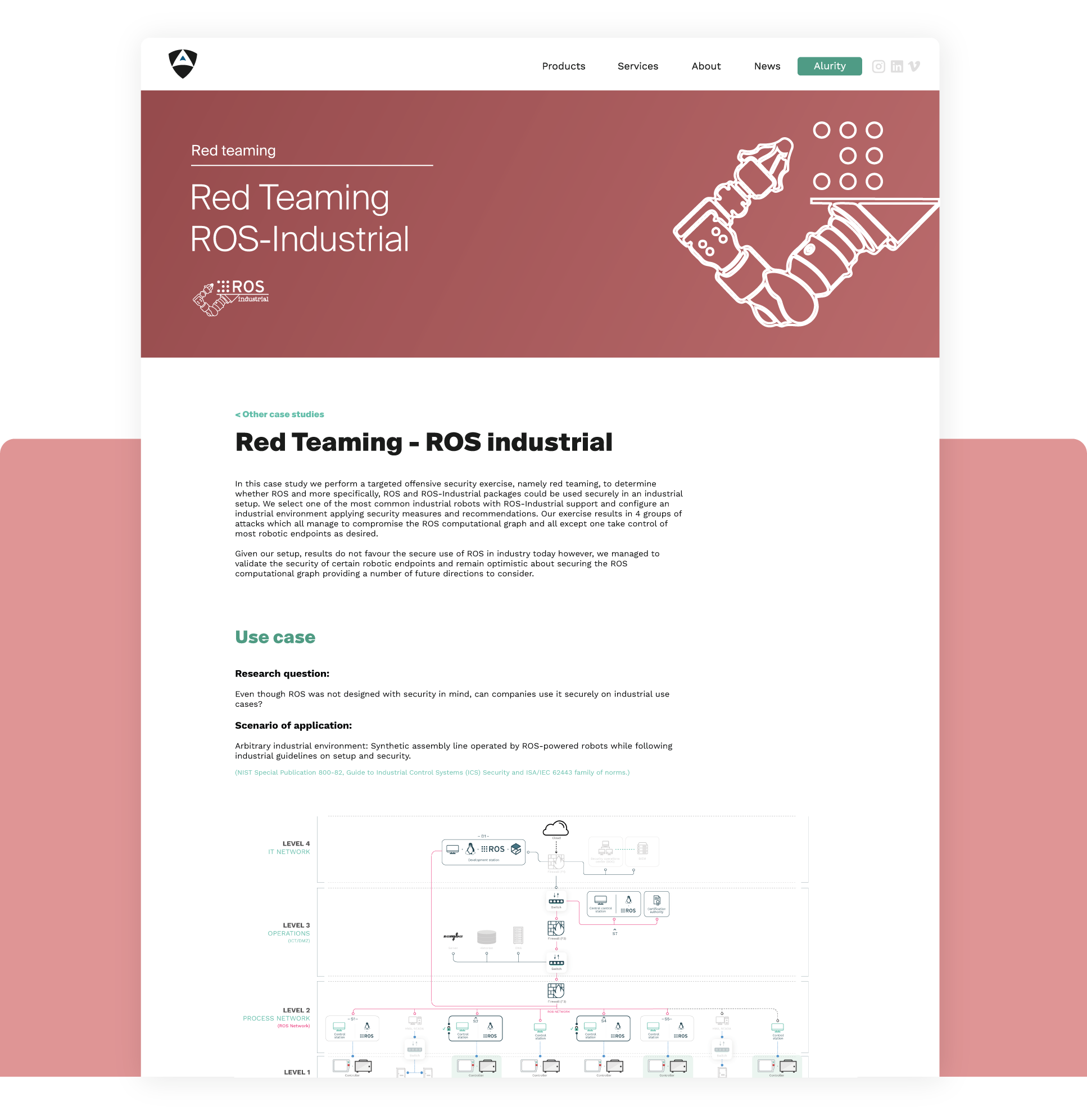
Can ROS be used securely for industrial use cases? The present study analyzes this question experimentally by performing a targeted offensive security exercise in a synthetic industrial use case involving ROS-Industrial and ROS packages.

After months of failed interactions with MIR and while trying to help secure their robots, Alias decided to empower end-users of Mobile Industrial Robots' with information and disclosed preliminary results. This case study illustrates the information made available and the consequences of the insecurity.
This attack case study presents the penetration testing exercise conducted during the Week of Universal Robots' Bugs. Our team challenged the security of these robots and developed exploits for identified vulnerabilities, across different firmware versions.
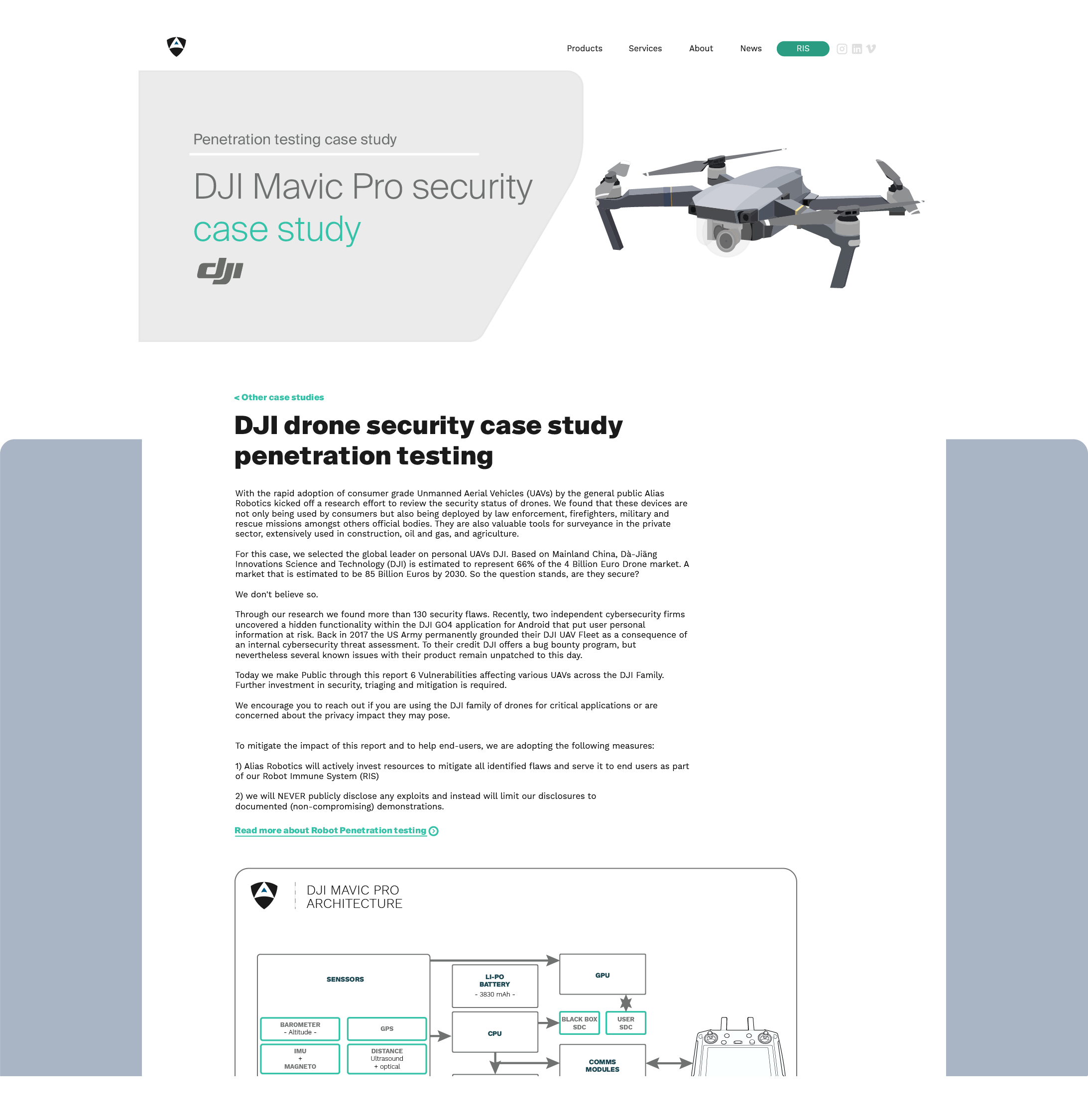
We pentest one of the most popular aerial robots, the DJI Mavic Pro drone and find more than 130 security flaws. Our results indicate that DJI's Bug Bounty program doesn't seem to operate any further and discloses 6 of the triaged flaws assessing their severity.
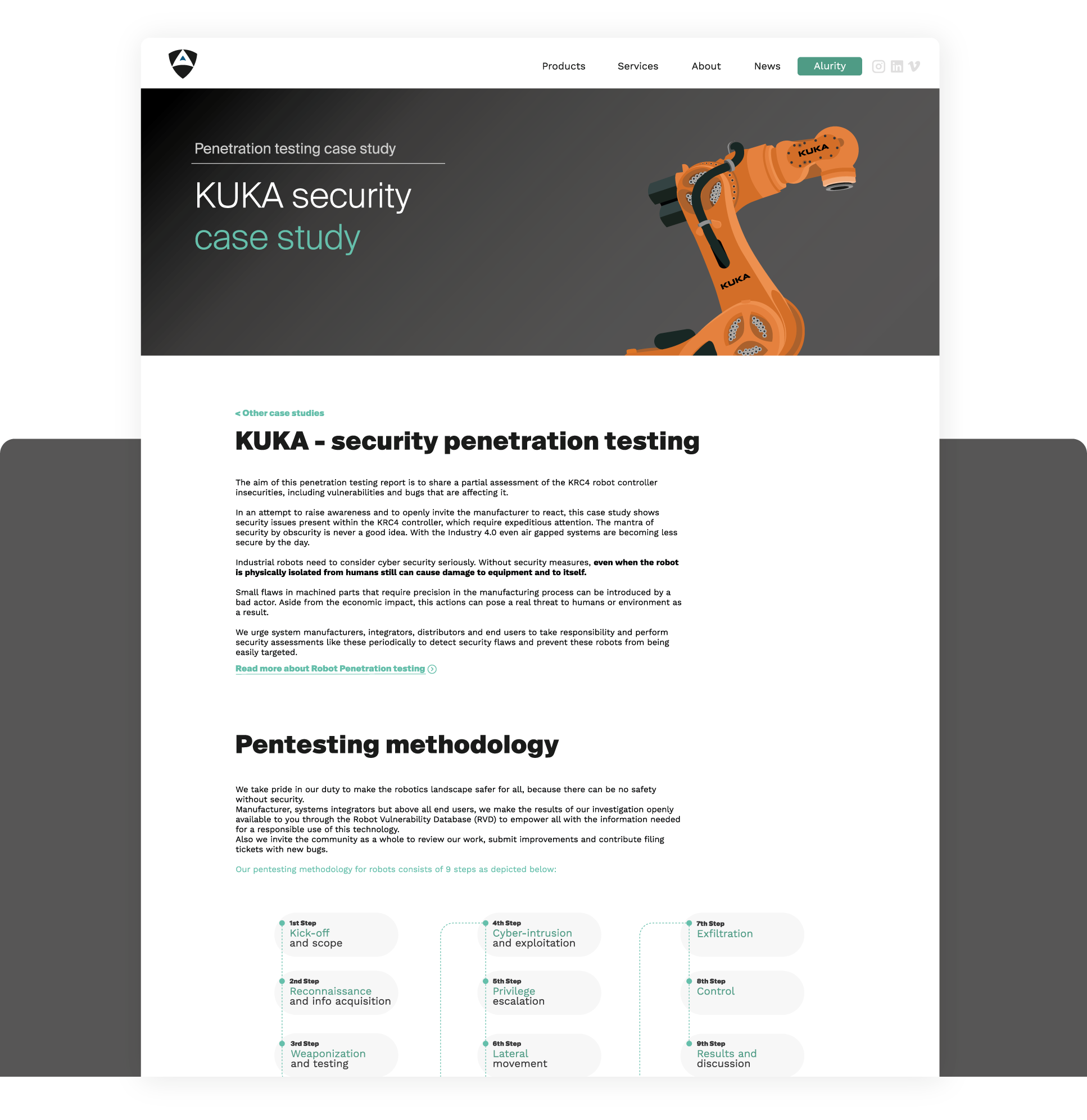
In cooperation with KUKA, the german Federal Cyber Security Authority (BSI) or the Spanish National Cybersecurity Institute (INCIBE) among others, we pentest KUKA's robots and responsibly disclose results hinting that further work is required to protect against hazards.
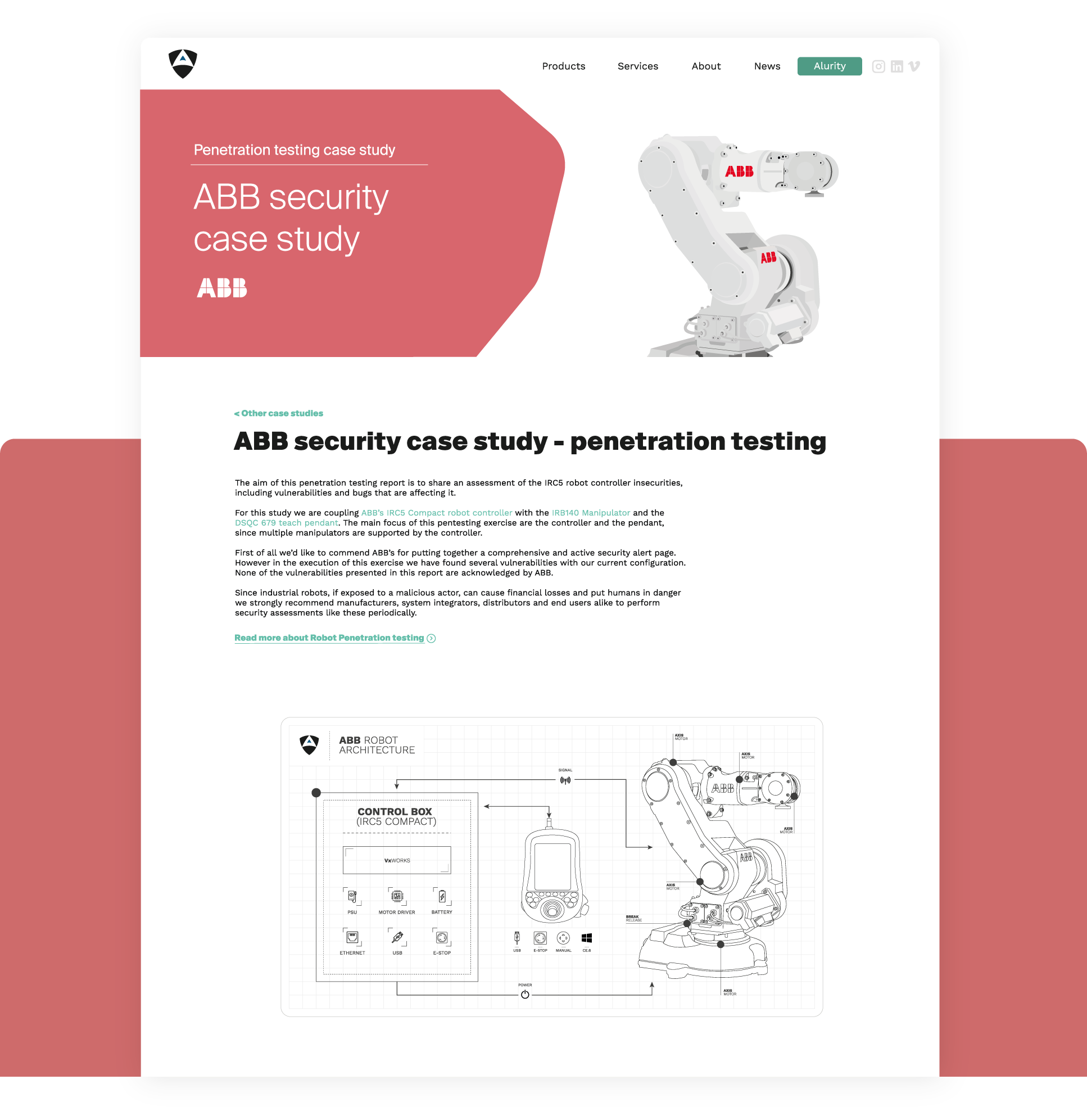
In cooperation with ABB, we tackled several security flaws identified in real deployed robots. We learned that while ABB cares about cyber security, many "older" ABB systems are flawed by both new (0-days) and old vulnerabilities leading to security EoL products.
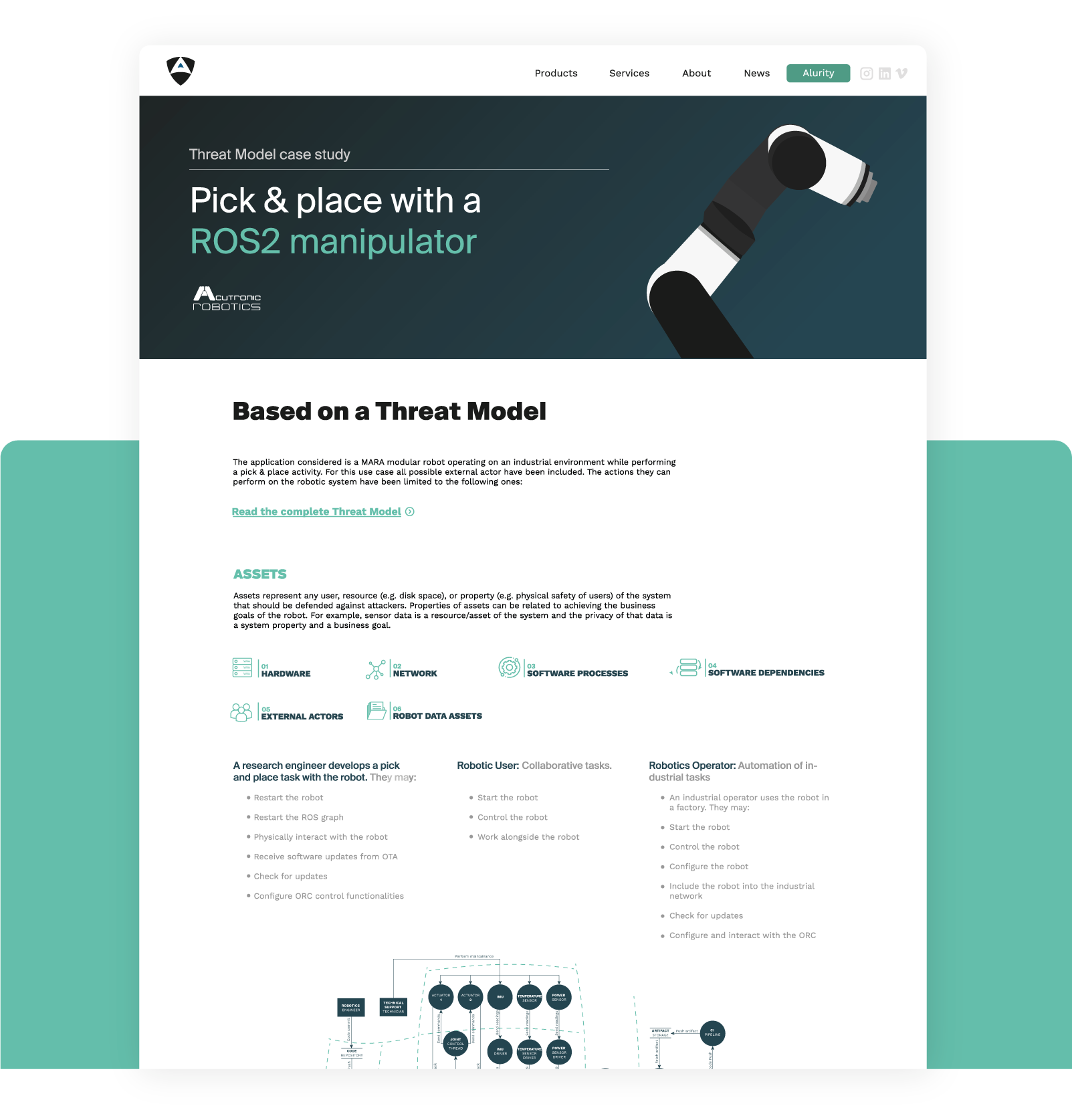
This cyber security case study shows a threat model performed in a fully modular ROS 2 articulated robotic arm. The application considered is MARA, a modular robot operating on an industrial environment while performing a pick & place activity.
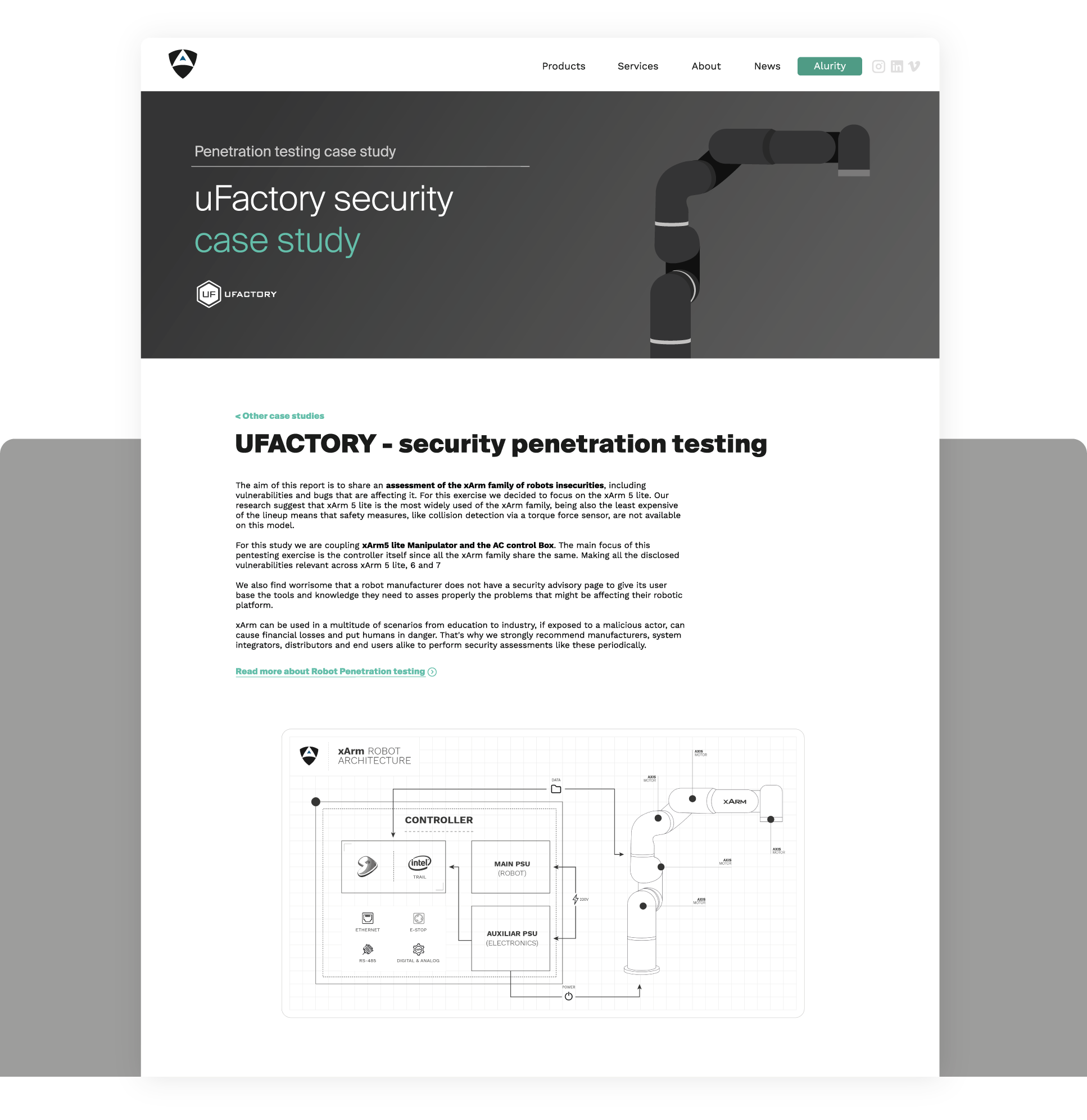
This cyber security case study shows how our team performed a short pentesting activity on a popular and rapidly growing low cost service robot, the UFactory's xArm. We study the xArm family of robots and report on the most representative security flaws.
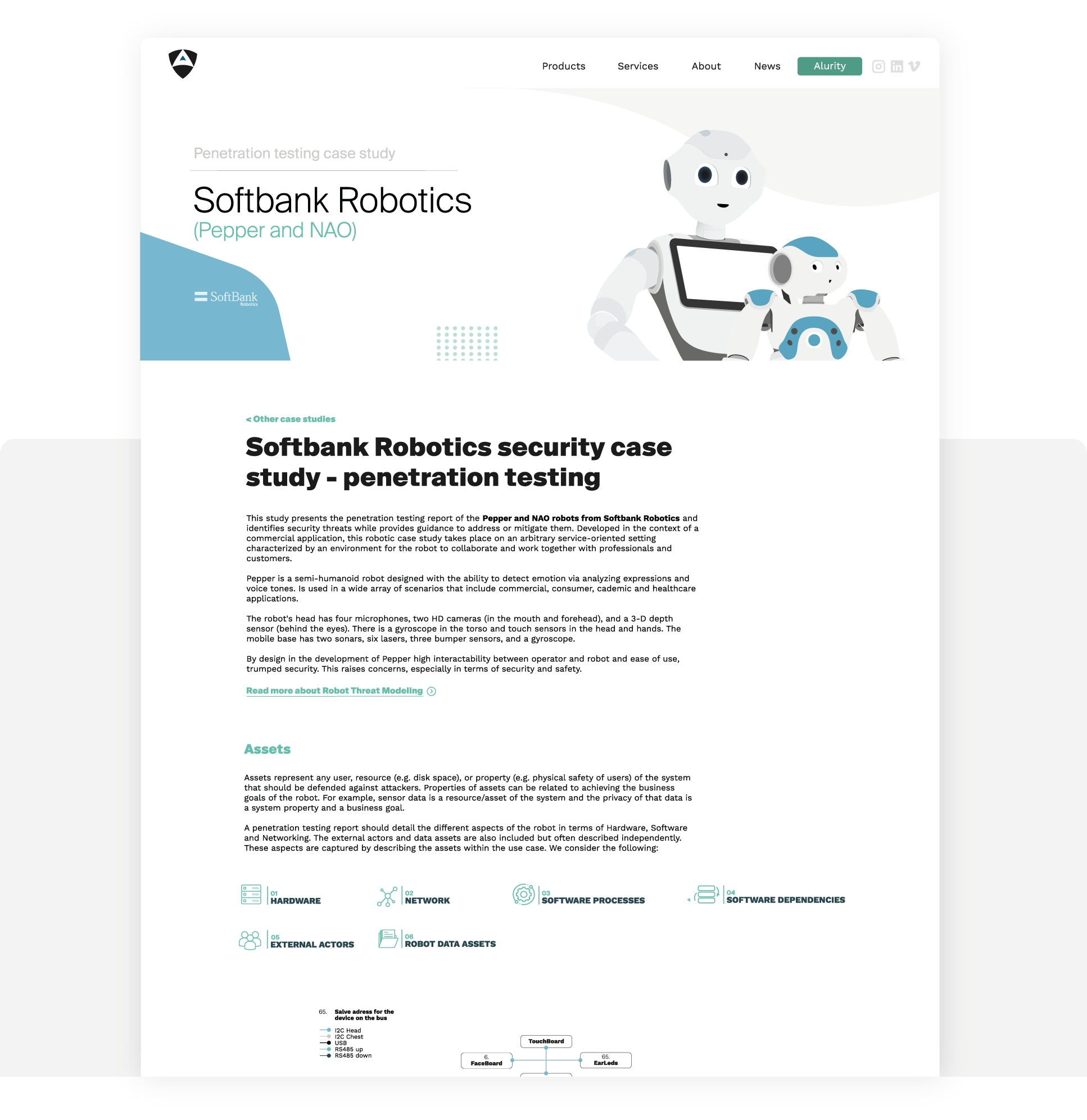
This study case presents the result of research and a posterior penetration testing exercise conducted on Softbank Robotics humanoid social robots. Building on top of past work, our team studied the security of these robots, and demonstrated the current insecurities.

This cyber security case study presents a brief penetration testing report alongside a novel exploit demonstration affecting the Tello Drone by Ryze and DJI.
Get in touch with our team and we'll do our best to get back to you.
Let's talk