



With the rapid adoption of consumer grade Unmanned Aerial Vehicles (UAVs), security engineers in Alias Robotics kicked off a research effort to review the security status of drones. These devices are increasingly used by consumers and actively being deployed by law enforcement, firefighters or military among others. Applications are quite diverse, from personal photography to private surveillance going through construction mapping, oil and gas inspection, or agriculture automation.
We selected the global leader on personal UAVs, DJI and from their portfolio, we pick the DJI Mavic Pro drone. Based on Mainland China, Dà-Jiāng Innovations Science and Technology (DJI) is estimated to represent 66% (4 billion Euro) of the drone market. A market that is estimated to grow up to 85 billion Euros by 2030.
Our research correlated nicely with past events performed by other groups. The most popular one refers back to 2017, when the US Army permanently grounded their DJI UAV fleet as a consequence of an internal cybersecurity threat assessment. Since then, DJI has publicly claimed to invest in cybersecurity and compensate security researchers through a bug bounty program however to the best of our knowledge, such program has neither transparency, nor real impact since we verified that several flaws known to the public weren't patched on these systems.
Through our research we found a more than 130 security flaws affecting this aerial robot, the DJI Mavic Pro. This correlates nicely with past events and reports negatively about the security practices DJI is following. With this short case study, we disclose publicly 6 of the security vulnerabilities affecting DJI Mavic Pro products. We encourage DJI to reconsider their security posture and invite end-users or groups interested in the complete results to reach out.
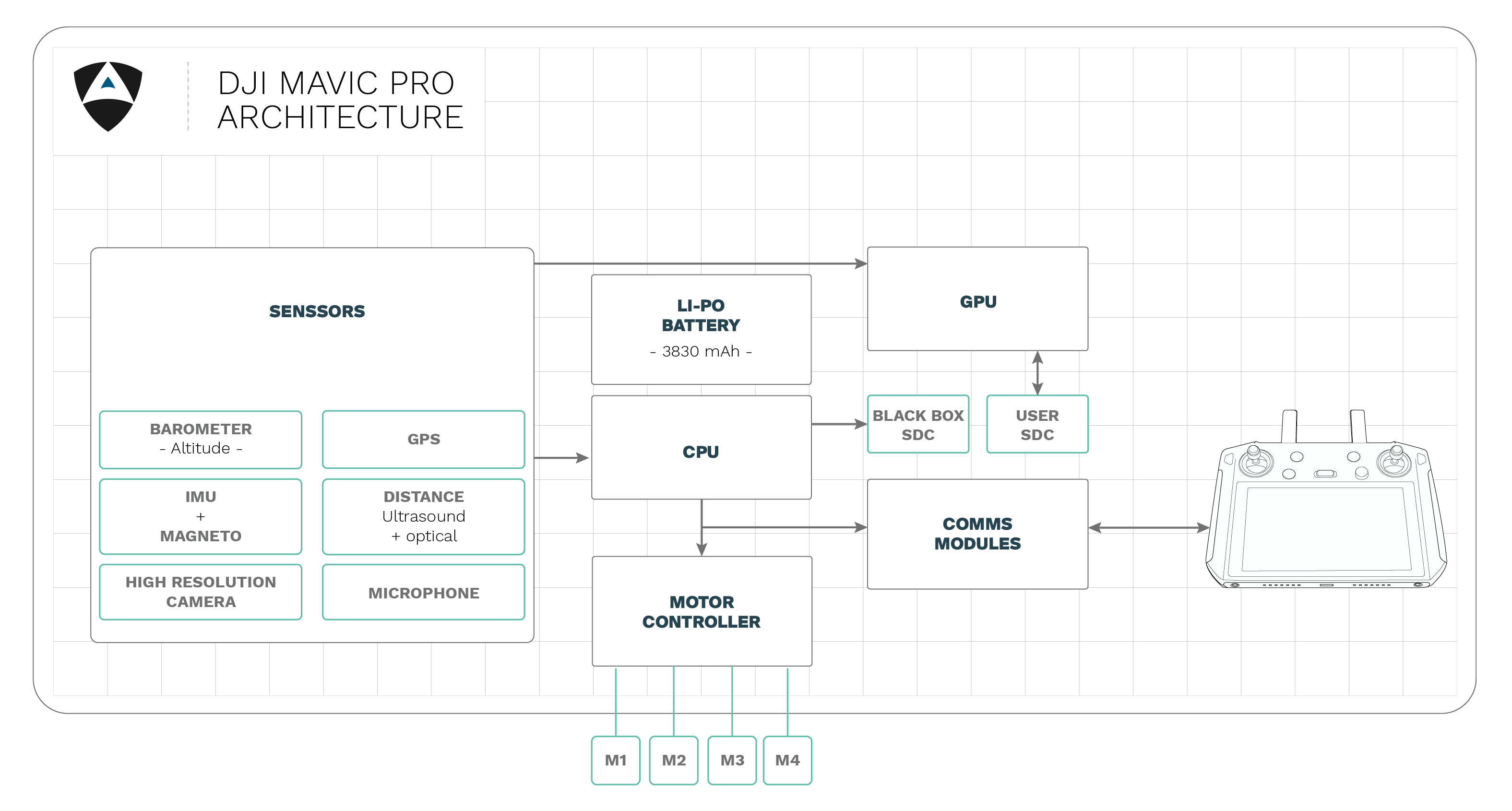

We take pride in our duty to make the robotics landscape safer for all, because there can be no safety without security. Our pentesting methodology for DJI considered the following 9 steps as depicted below:
Learn more about pentesting robots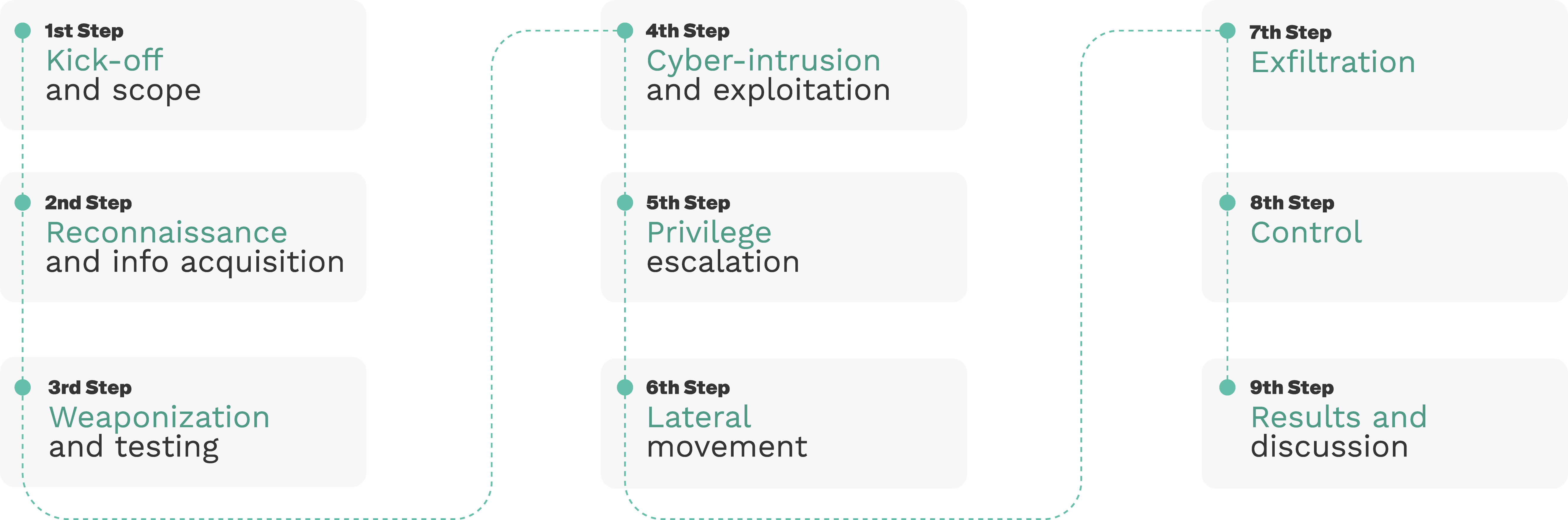
RVDP#713
RVDP#715
RVDP#716
A race condition was found in the way the kernel's memory subsystem handled breakage of the read only private mappings COW situation on write access. An unprivileged local user could use this flaw to gain write access to otherwise read only memory mappings and thus increase their privileges on the system.

RVDP#717
RVDP#718
More than 130 security flaws are known for DJI Mavic drone and have been catalogued within RVDP, our private robot vulnerability database. Through this short study, 6 have been disclosed. Even though DJI has a Bug Bounty Program, the communications we've established with the vendor lead us to doubt about its operation. Also, many of these issues are still unaddressed to this date though public information is available in some cases (beyond this case study). We highly encourage end-users to seek alternative security solutions that protects their robots.
From Alias Robotics, we will continue insisting on receiving latest updates and plan to react based on the manufacturer’s response to the current insecurity landscape while request to enforce European laws.

At Alias Robotics we encourage a security-first approach to robotics. One that focuses on continuous monitoring and management of robot security risks and threats, leveraging modern tools and automation techniques to ensure that, at all times, the robots stay safe and secure. As indicated in the past, we strongly believe that vulnerability disclosure is a two-way street where both vendors and researchers, must act responsibly. We strongly believe each security researcher or group should reserve the right to bring deadlines forwards or backwards based on extreme circumstances.
Alias remains committed to treating all vendors strictly equally and we expect to be held to the same standard. By no means Alias encourages or promote the unauthorized tampering with running robotic systems. This can cause serious human harm and material damages.