

Several models of Universal Robots, including the UR3e, have been subject to multiple publicly reported cybersecurity vulnerabilities. These include CVE-2020-10265 (unauthenticated access to the Dashboard Server), CVE-2020-10266 (unauthorized file access via the Log File Manager), and CVE-2020-10267 (exposure of internal system information through insecure web endpoints). Collectively, these flaws highlight systemic issues in authentication and access control mechanisms within the robot’s software stack.
CVE-2020-10265 specifically targets the Dashboard Server component of the UR3e platform, which lacks authentication by default. This allows remote attackers to connect to the server and execute sensitive commands, such as starting, stopping, or even powering off the robot. Alias Robotics used its CAI framework to automate the exploitation of this vulnerability, demonstrating how an adversary could gain full control over the robot’s operations without any credentials.
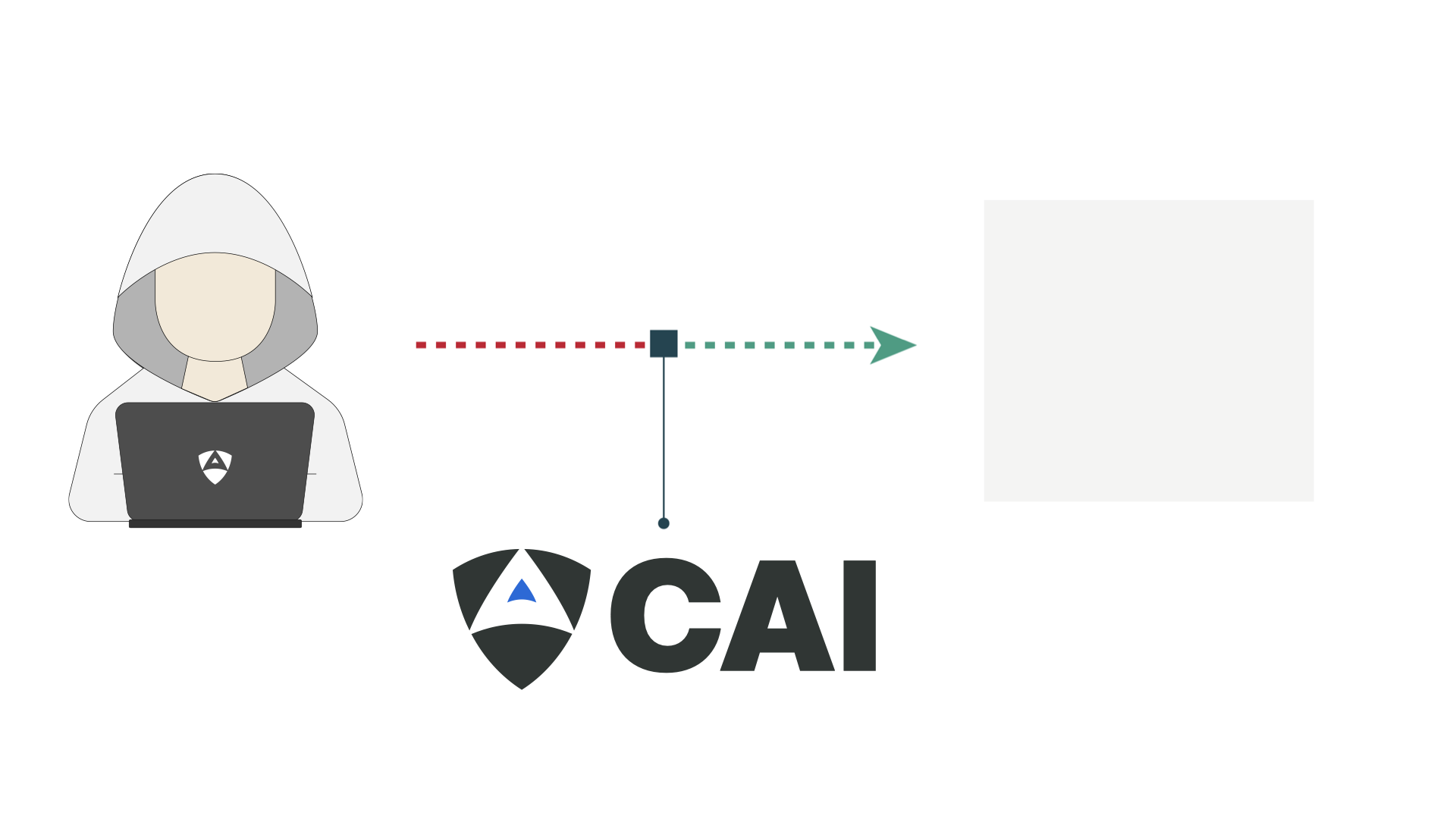

This video showcases how a CAI agent autonomously located a UR3e robot on the local network using Nmap scans. After identifying the device, the agent analyzed its exposed ports and detected the Dashboard Server listening on TCP port 29999. Leveraging this discovery, the CAI framework confirmed that the service lacked authentication and proceeded to establish a socket connection. By sending a simple stop command, the agent was able to remotely halt the robot's operation.
CAI represents the first open-source framework specifically designed to democratize advanced security testing through specialized AI agents. By 2028, most cybersecurity actions will be autonomous, with humans teleoperating, making CAI's approach to AI-powered vulnerability discovery increasingly critical for organizational security. The framework transcends theoretical benchmarks by enabling practical security outcomes. CAI achieved first place among AI teams and secured a top-20 position worldwide in the "AI vs Human" CTF live Challenge, earning a monetary reward and various other prizes and bounties ever since then. This performance demonstrates that AI-powered security testing can compete with and often exceed human capabilities in vulnerability discovery.
Explore CAI's source code ❯Universal Robots (UR) is a Danish manufacturer of collaborative robot arms (cobots) designed to work safely alongside humans in industrial settings. UR’s platforms—such as the UR3e, UR5e, and UR10e—are widely used in manufacturing, logistics, and electronics due to their ease of use, flexibility, and network connectivity. These systems integrate with factory infrastructure and offer powerful remote interfaces, such as the Dashboard Server, to enable control and monitoring.
As cobots become more connected, UR platforms increasingly face cybersecurity risks. Interfaces like the Dashboard Server can expose critical functions if left improperly secured, making it essential to assess and mitigate these threats to ensure safe and resilient automation.
16
~2 €
The UR3e robot’s Dashboard Server accepted unauthenticated commands over its TCP interface, exposing core control functions to any networked client. CAI systematically tested various command strings and confirmed that simple instructions like stop were accepted and executed without validation. This lack of authentication and input filtering on port 29999 allowed the robot to be halted remotely, demonstrating how insecure service configurations can lead to direct operational disruption in industrial robotics.
To validate and demonstrate the risk, CAI executed an automated routine to scan the local network using Nmap and identify a UR3e robot through its open TCP services. Upon discovering that the Dashboard Server was accessible on port 29999, the agent established a socket connection and sent the stop command without authentication. This single action was enough to remotely halt the robot’s operation.
