

Still in the testing and analysis phase, the low cost AMR1 already exhibits several significant issues that have yet to be publicly disclosed. A recurring example involves the well-known vulnerabilities associated with ROS 1, the widely used middleware for communication, interconnection, and operation of robotic platforms.
The CAI-driven exercise included the detection of the ROS network and the communications between devices through what is known as topics, taking advantage of the lack of authentication in access and command injections. The study was successful in revealing that ROS commands execution from a connected but unauthorized endpoint caused severe disruptive consequences regarding the availability of the low cost AMR1.
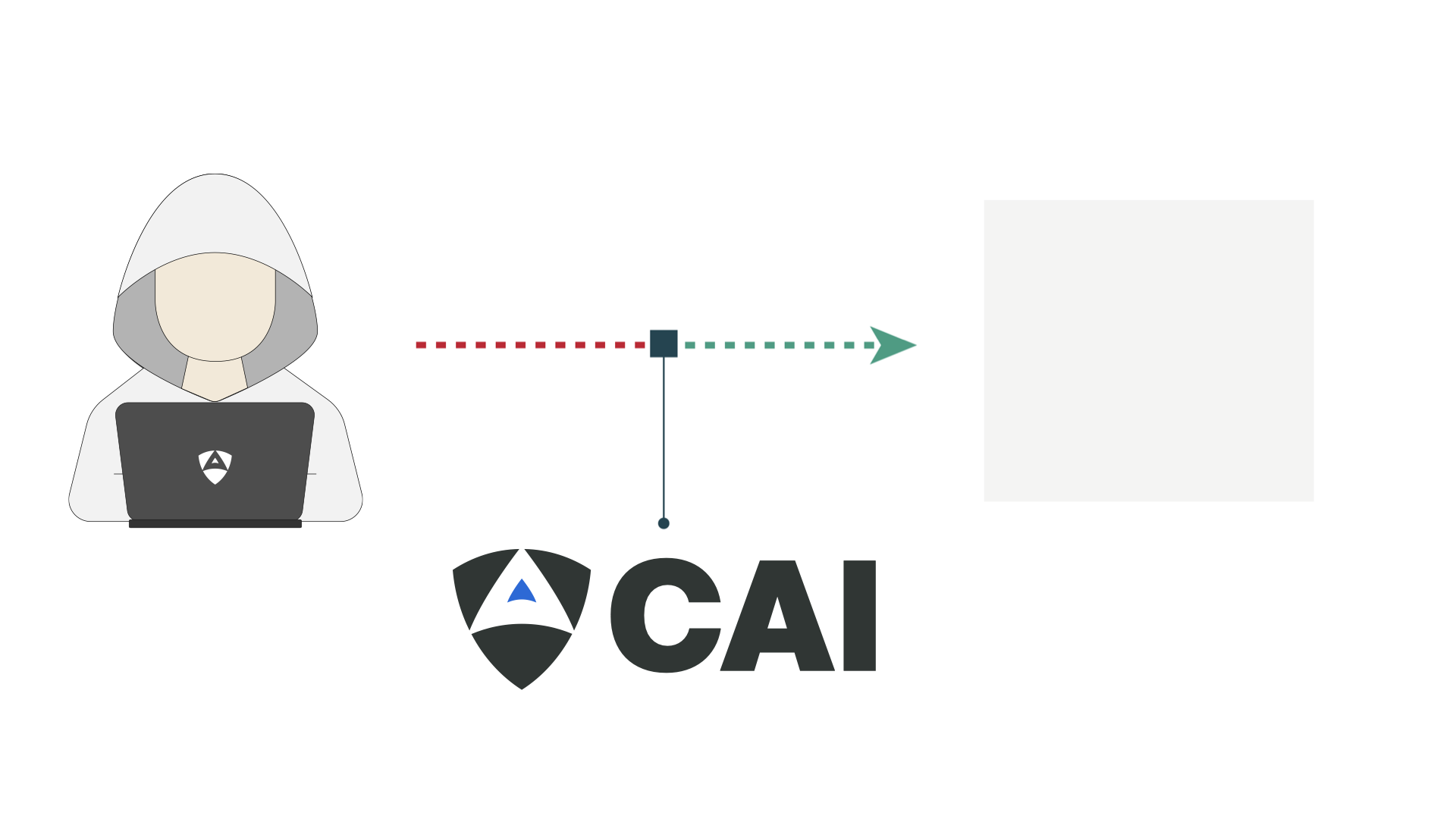

This video demonstrates the operation of CAI (Cybersecurity AI), which identifies the master node within the ROS network and connects to it without requiring authentication. Once inside, CAI uses the alias0 model to locate the relevant topic and inject a malicious ROS command that alters the mobile robot’s normal trajectory, causing it to spin uncontrollably. This severely compromises the robot’s availability and poses a potential danger to any nearby humans.
CAI represents the first open-source framework specifically designed to democratize advanced security testing through specialized AI agents. By 2028, most cybersecurity actions will be autonomous, with humans teleoperating, making CAI's approach to AI-powered vulnerability discovery increasingly critical for organizational security. The framework transcends theoretical benchmarks by enabling practical security outcomes. CAI achieved first place among AI teams and secured a top-20 position worldwide in the "AI vs Human" CTF live Challenge, earning a monetary reward and various other prizes and bounties ever since then. This performance demonstrates that AI-powered security testing can compete with and often exceed human capabilities in vulnerability discovery.
Explore CAI's source code ❯Low cost AMR1 is an autonomous mobile robot with remarkable performance, designed to optimize logistics and material handling in industrial environments. Its compact and agile design enables it to effectively navigate complex warehouse layouts and confined spaces. Low cost AMR1 stands out for its combination of low cost and high-performance control and operational capabilities, making it a highly attractive option compared to higher-priced alternatives.
14
~1.5 €
Evaluate whether a remote agent could connect to the robot’s ROS master, identify critical topics, and influence its motion without authentication—exposing potential weaknesses in ROS 1’s access control and topic-level protections.
Using CAI, Alias Robotics simulated a real-world attack against the low cost AMR1 by exploiting ROS 1’s lack of authentication. CAI detected the ROS master, connected without credentials, identified the correct topic (/cmd_vel), and executed a ROS command that disrupted its normal operation. The robot’s behavior was altered remotely, confirming the severity of the vulnerability.
