



While serving customers, we decided to walk an extra mile, ask for permission and cooperate with ABB's cyber security team on the disclosure and triage of a few of the flaws identified on our customer's robots. In total we identified about 25 security flaws, many of critical severity and reported to ABB a subset of them in a responsible disclosure manner. From our experience with manufacturers, cooperating on security with ABB's team was quite an interesting endeavour. They responded promptly and provided insights on every ticket. They were helpful pointing out patches we missed or misassumptions we made (based on our customer's setup) while at the same time, they acknowledged a few mistakes on their end as well that required security attention. While we disagreed on several of the mitigation actions, they offered rationale on their approach and will to serve best their customers. Overall, we'd like to thank ABB's cyber security response team for their cooperation and look forward to find future opportunities to do it again.
From this experience, we learned that while ABB cares about cyber security and has a long history investing in this area, many "older" ABB systems are very flawed by both new (0-days) and old vulnerabilities. Also, we understood that many of these robotic systems rely on third party components which don't get updated any further (EoL). Particularly, we further dived into one of the ABB suppliers and requested patches for several of the flaws found receiving answers indicating that such patches were not available nor were planned due to product EoL. Altogether, this led us to reckon that likely, beyond ourselves, other security researchers may have a significantly different viewpoint when compared to ABB's and will find themselves troubled since there's clear vulnerability evidence.
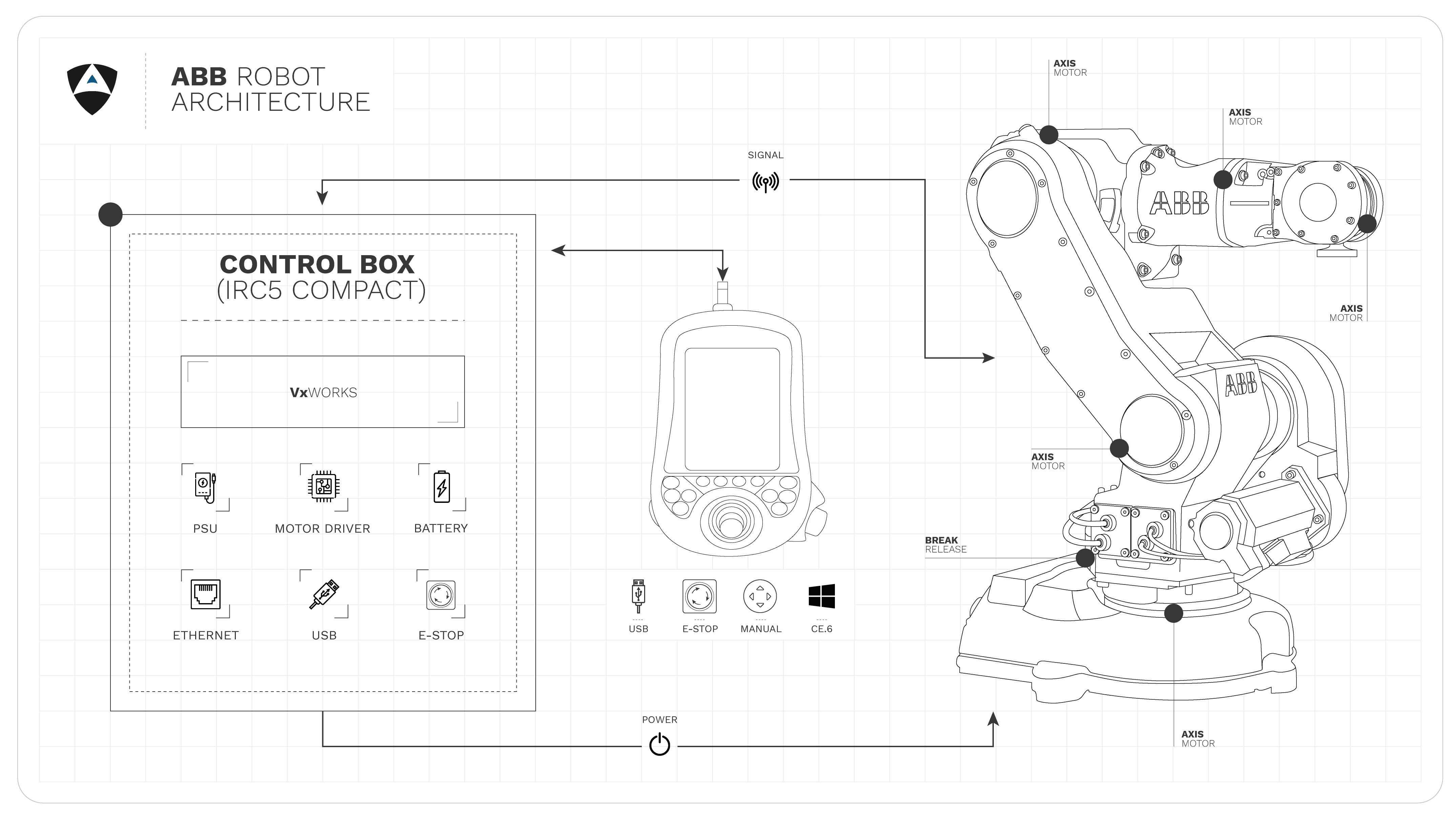
Our disclosures below are restricted to ABB’s IRC5 Compact robot controller with the IRB140 Manipulator and the DSQC 679 teach pendant. We hope to have resources in the future to expand on this case study and complement it with other ones where we treat some of the more sentitive issues identified.

We take pride in our duty to make the robotics landscape safer for all, because there can be no safety without security.
Manufacturer, systems integrators but above all end users, we make the results of our investigation openly available to you through the Robot Vulnerability Database (RVD) to empower all with the information needed for a responsible use of this technology.
Also we invite the community as a whole to review our work, submit improvements and contribute filing tickets with new bugs.
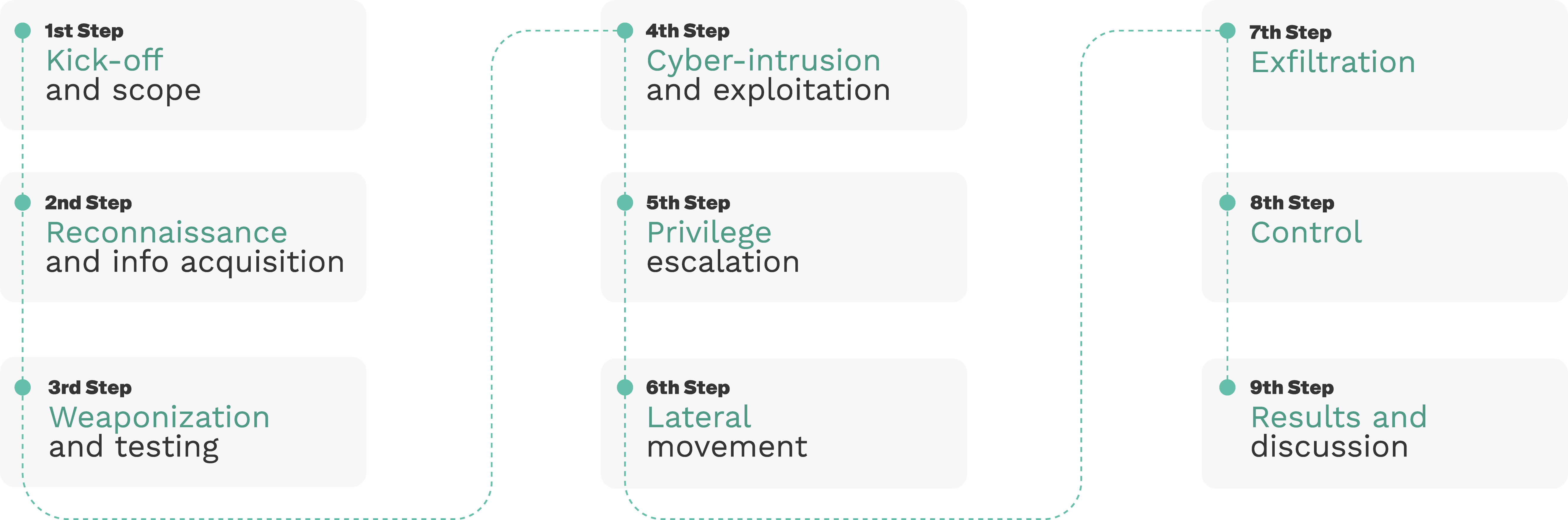
Our pentesting methodology for robots consists of 9 steps as depicted below:
RVD#3327
RVD#3326
The IRC5 family with UAS service enabled comes by default with credentials that can be found on publicly available manuals. ABB considers this a well documented functionality that helps customer set up however, out of our research, we found multiple production systems running these exact default credentials and consider thereby this an exposure that should be mitigated. Moreover, future deployments should consider that these defaults should be forbidden (user should be forced to change them).


ABB’ is one of the most prominent robot manufacturers in the current landscape and the mechanical reliability of their platform is one of the main reasons for that. The unintended consequence is that currently a good portion of ABB robots out in the field are outdated in terms of robotic cybersecurity and that make those robots a liability. Even though a well-made machine can last for a long time given proper care and maintenance, when it comes to cyber security, over shorter periods of time a relevant number of flaws could be identified leading to the security End-of-Life (EoL) of a product and then be vulnerable to attacks that may compromise environments and humans. Prevention is the only way to be one step ahead.
Assess your robot insecurities❯