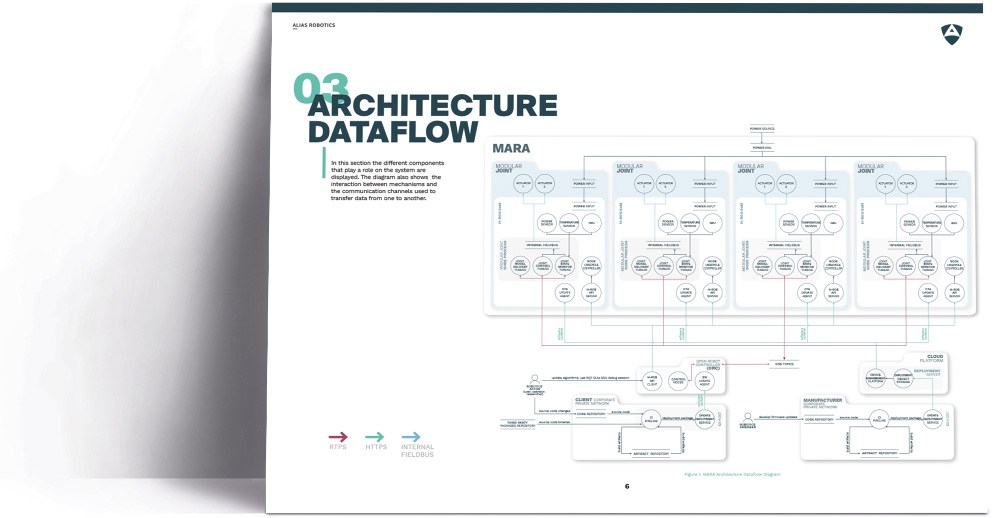
Other services
Robot Security
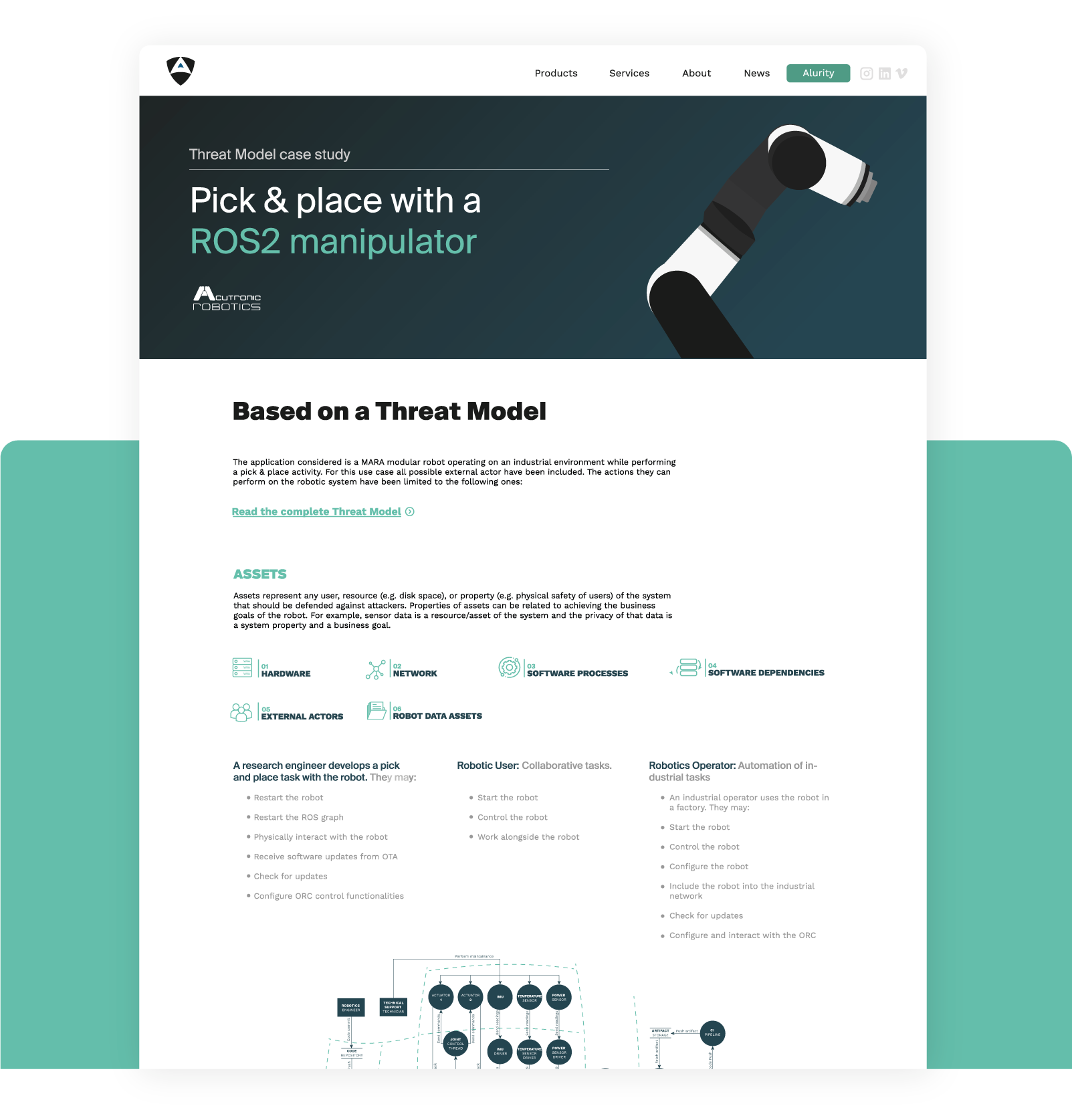
Threat Model
See what your security landscape looks like.
Threat modeling is about identifying and reporting security threats applied to a robot and/or its components (both software and hardware) while providing means to address or mitigate them.
It aids you to theoretically analyse and evaluate all your infrastructure and system.Based on: