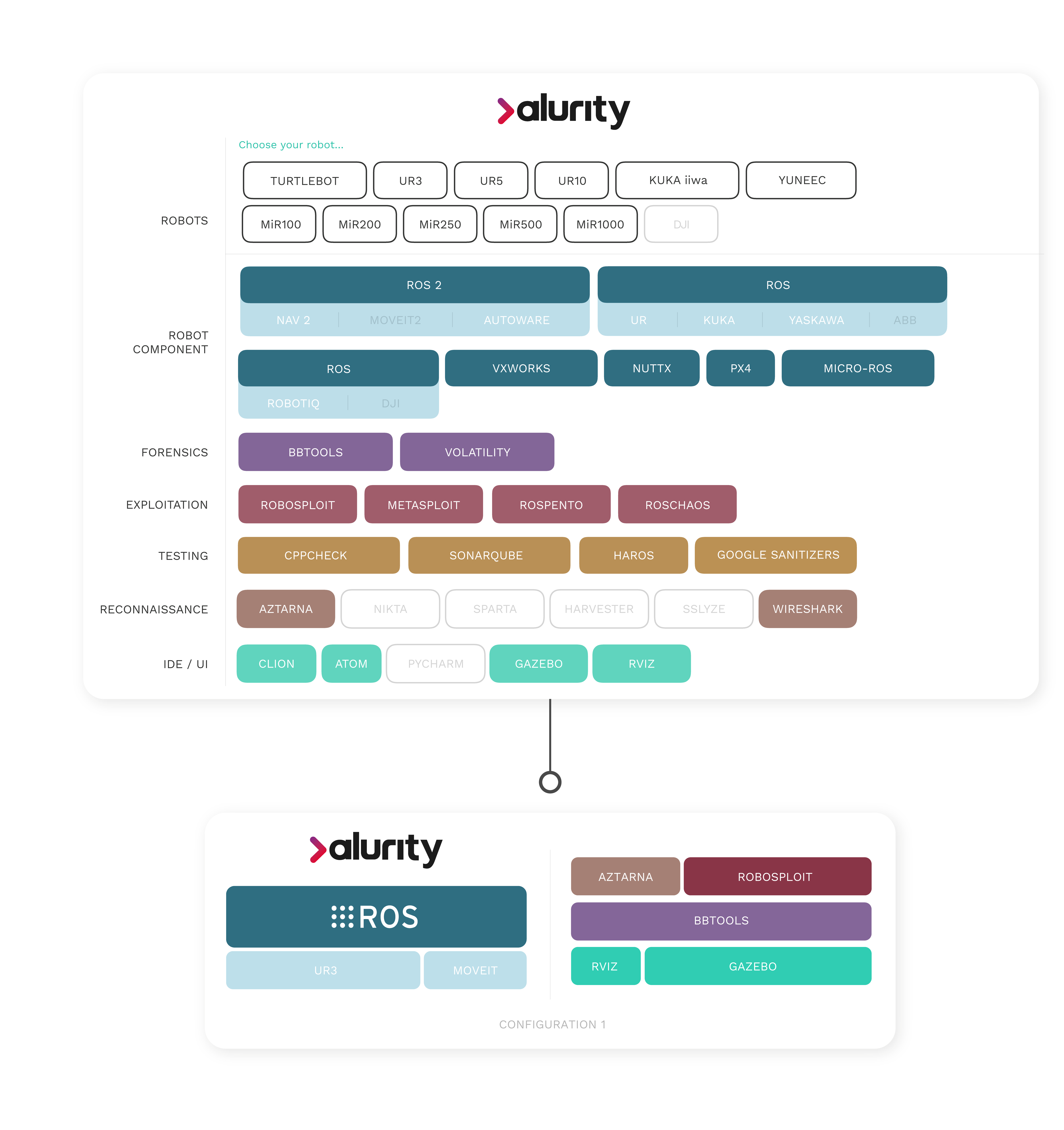
Architecture
Alurity allows to easily build robotic subjects of study simulating different networks (e.g. LANs, serial comms, VPNs, VLANs, VXLANs, etc) and protection mechanisms. It also allows you to build automated attackers and weaponize them with different tools and exploits, facilitating evidence generation and reproduction.