Look at some
examples

After months of failed interactions with MIR and while trying to help secure their robots, Alias decided to empower end-users of Mobile Industrial Robots’ with information and disclosed preliminary results. This case study illustrates the information made available and the consequences of the insecurity.
This attack case study presents the penetration testing exercise conducted during the Week of Universal Robots’ Bugs.
Our team challenged the security of these robots and developed exploits for identified vulnerabilities, across different firmware versions.
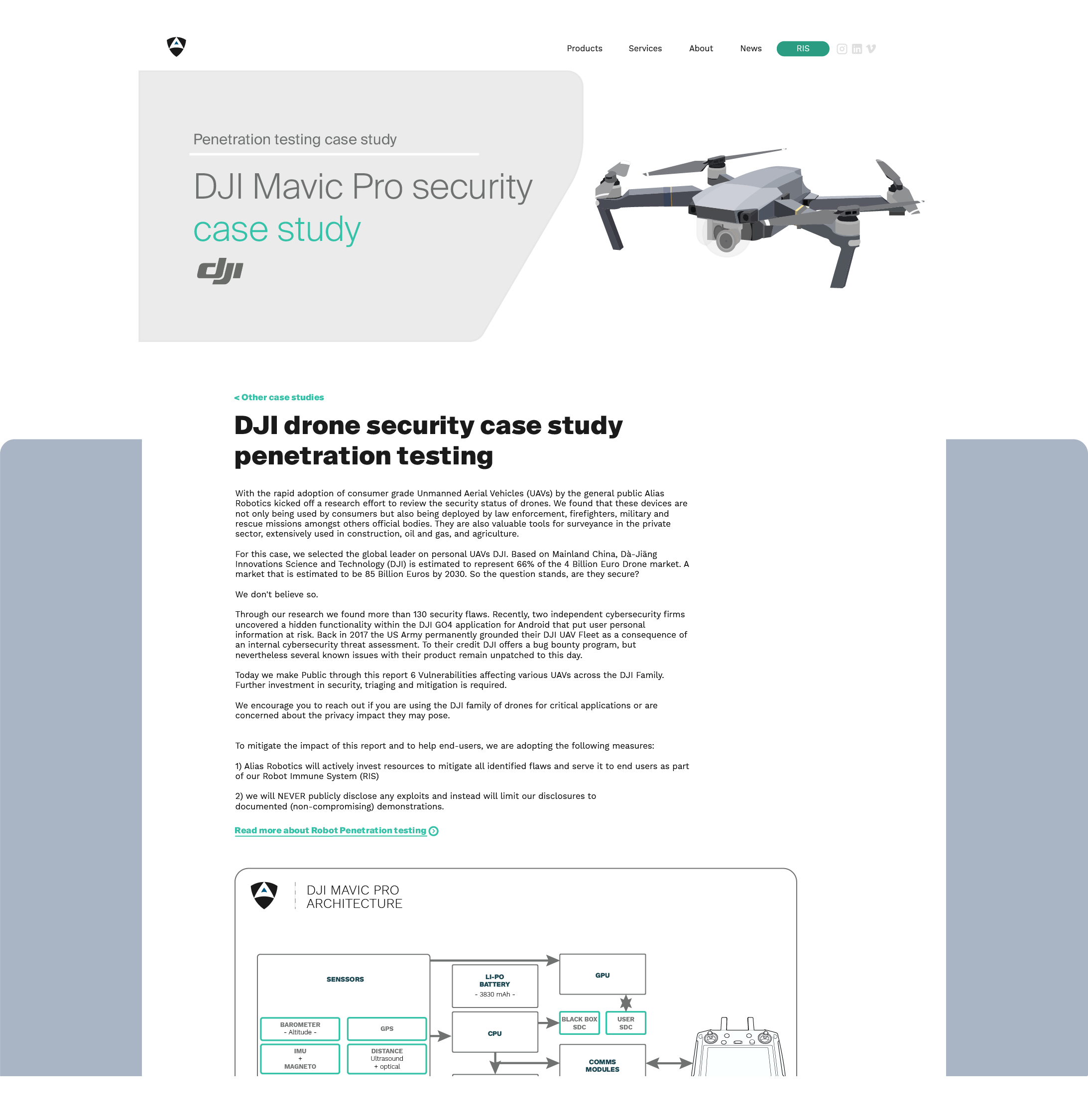
We pentest one of the most popular aerial robots, the DJI Mavic Pro drone and find more than 130 security flaws. Our results indicate that DJI's Bug Bounty program doesn't seem to operate any further and discloses 6 of the triaged flaws assessing their severity.
In cooperation with KUKA, the german Federal Cyber Security Authority (BSI) or the Spanish National Cybersecurity Institute (INCIBE) among others, we pentest KUKA's robots and responsibly disclose results hinting that further work is required to protect against hazards.
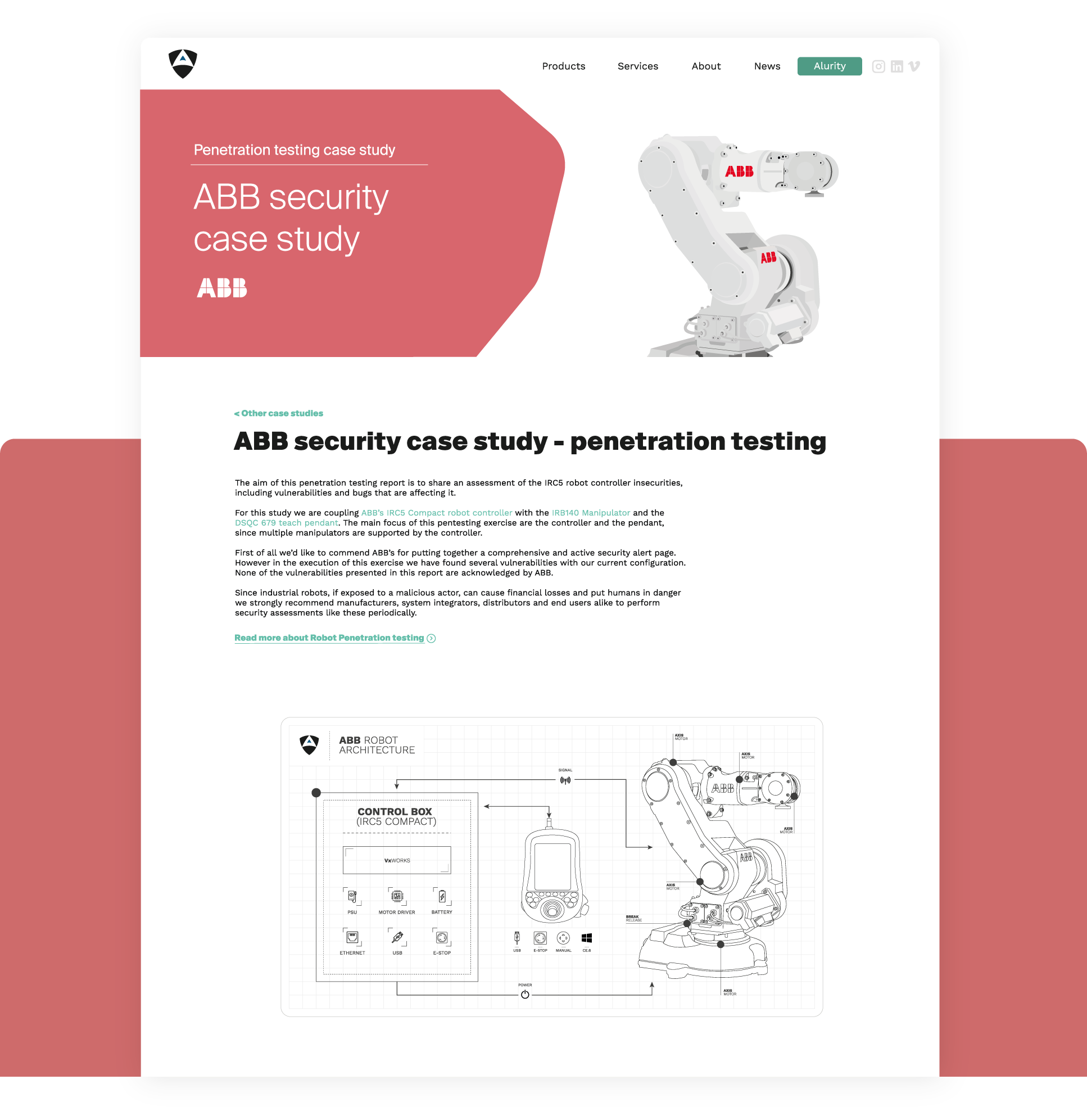
In cooperation with ABB, we tackled several security flaws identified in real deployed robots. We learned that while ABB cares about cyber security, many "older" ABB systems are flawed by both new (0-days) and old vulnerabilities leading to security EoL products.
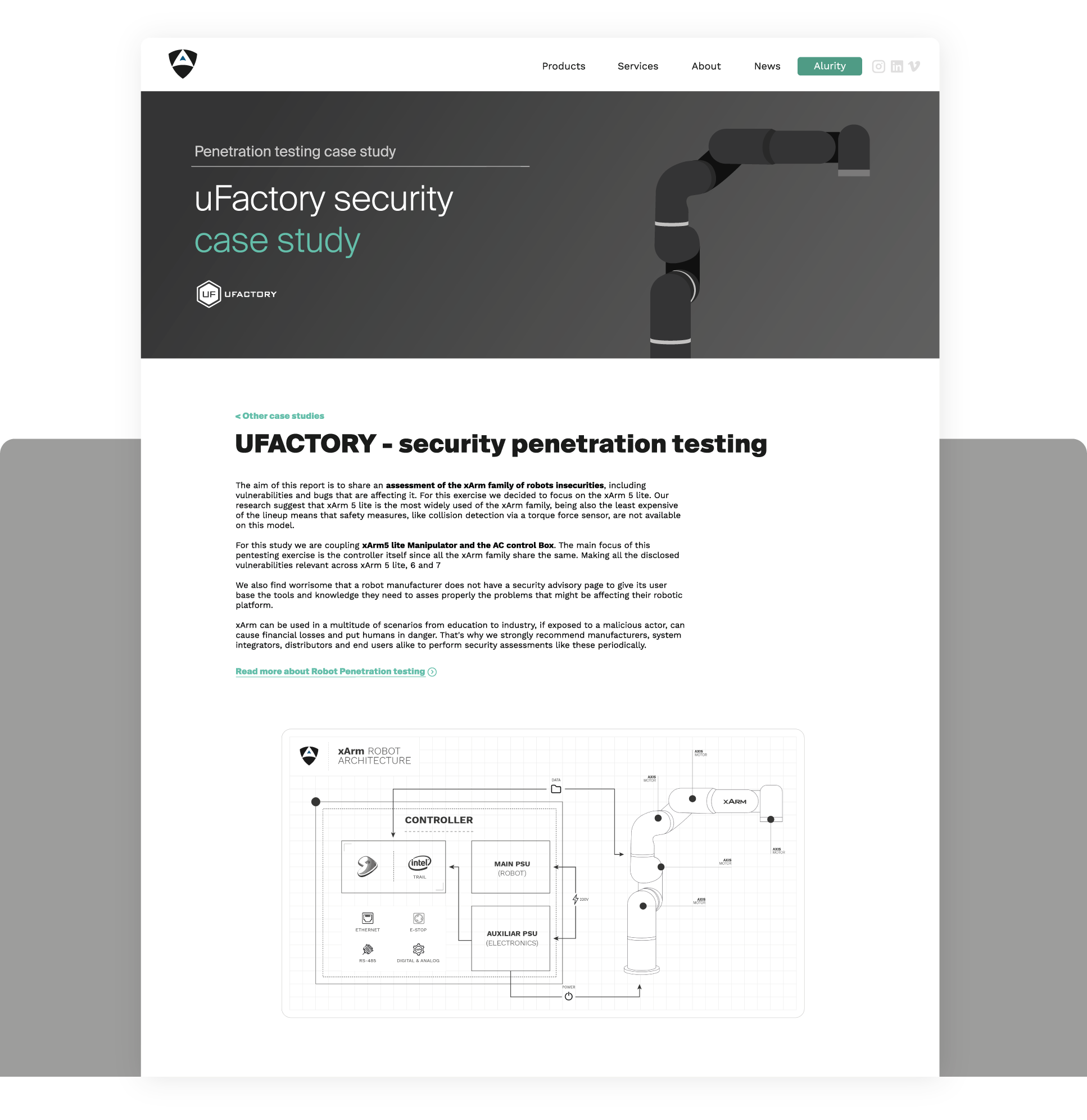
This cyber security case study shows how our team performed a short pentesting activity on a popular and rapidly growing low cost service robot, the UFactory's xArm. We study the xArm family of robots and report on the most representative security flaws.
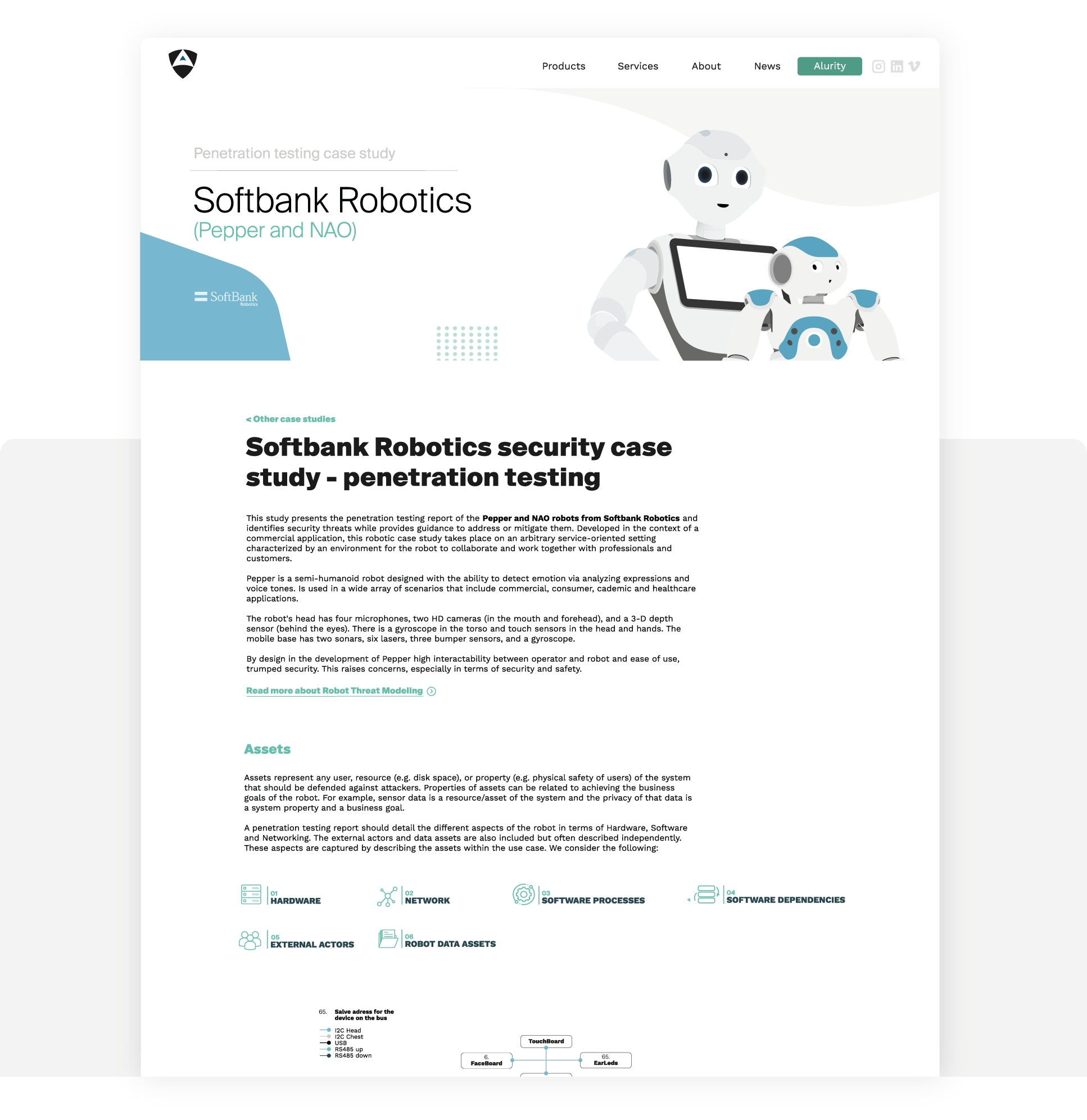
This study case presents the result of research and a posterior penetration testing exercise conducted on Softbank Robotics humanoid social robots.
Building on top of past work, our team studied the security of these robots, and demonstrated the current insecurities.

This cyber security case study presents a brief penetration testing report alongside a novel exploit demonstration affecting the Tello Drone by Ryze and DJI.
This type of assessment is generally performed in a black-boxed manner where Alias doesn't have access to additional resources except what's publicly available.