
Threat modeling is a structured exercise that leverages abstractions and real-world data to detect potential risks. This process identifies potential attackers, their capabilities, resources, and intended objectives. In this study, threat modeling is applied to analyze each platform's implementation, detect security vulnerabilities, and offer practical solutions or workarounds based on real-world usage scenarios.
Threat modeling is crucial for developing robust security defenses and generally answers the following key questions:
This case study aims to conduct a preliminary analysis and provide practical recommendations to strengthen the cybersecurity of connected autonomous mobile robots (AMRs). The goal is to protect AMR systems, ensure user safety, and encourage a proactive approach toward cybersecurity. This approach is critical to addressing emerging threats and ensuring the reliable performance of AMRs in an evolving environment. The study also aligns with forthcoming regulations such as the Cyber Resilience Act for manufacturers and NIS2 for end users.
Low cost AMR1 is a state-of-the-art autonomous mobile robot designed to optimize logistics and material handling in commercial environments. Its compact, agile design allows it to navigate complex layouts and confined spaces effectively. Low cost AMR1 stands out for its advanced capabilities compared to other alternatives.
Despite these impressive features, cybersecurity remains an under-prioritized aspect of AMR design. Manufacturers often do not focus on security as a selling point, leaving these robots vulnerable to cyberattacks. To understand the attack surface of a robotic system, it is essential to conduct a threat modeling exercise to identify and mitigate cybersecurity risks.

Cybersecurity has become essential for maintaining the safety and integrity of industrial applications, especially in complex, interconnected environments like the logistics industry. The growing connectivity and complexity of these systems significantly expand the attack surface, exposing Autonomous Mobile Robots (AMRs) to various cyber threats. These threats can compromise operational availability, lead to safety issues, and cause economic and reputational damage.
This report analyzes cybersecurity threats for the low cost AMR1 using the IEC 62443-4-2 standard, adapted for logistics. It identifies entry points, attack surfaces, and trust boundaries, providing insights into security risks and countermeasures. The standard's security categories help assess and mitigate potential threats in AMR applications.
The names and details in this case study have been anonymized for confidentiality. This content is solely intended to highlight the general cybersecurity status of AMRs. Alias Robotics does not endorse, encourage, or promote unauthorized tampering with robotic systems, which may result in severe injury, significant property damage, and legal consequences.
Overview of the onboard architecture
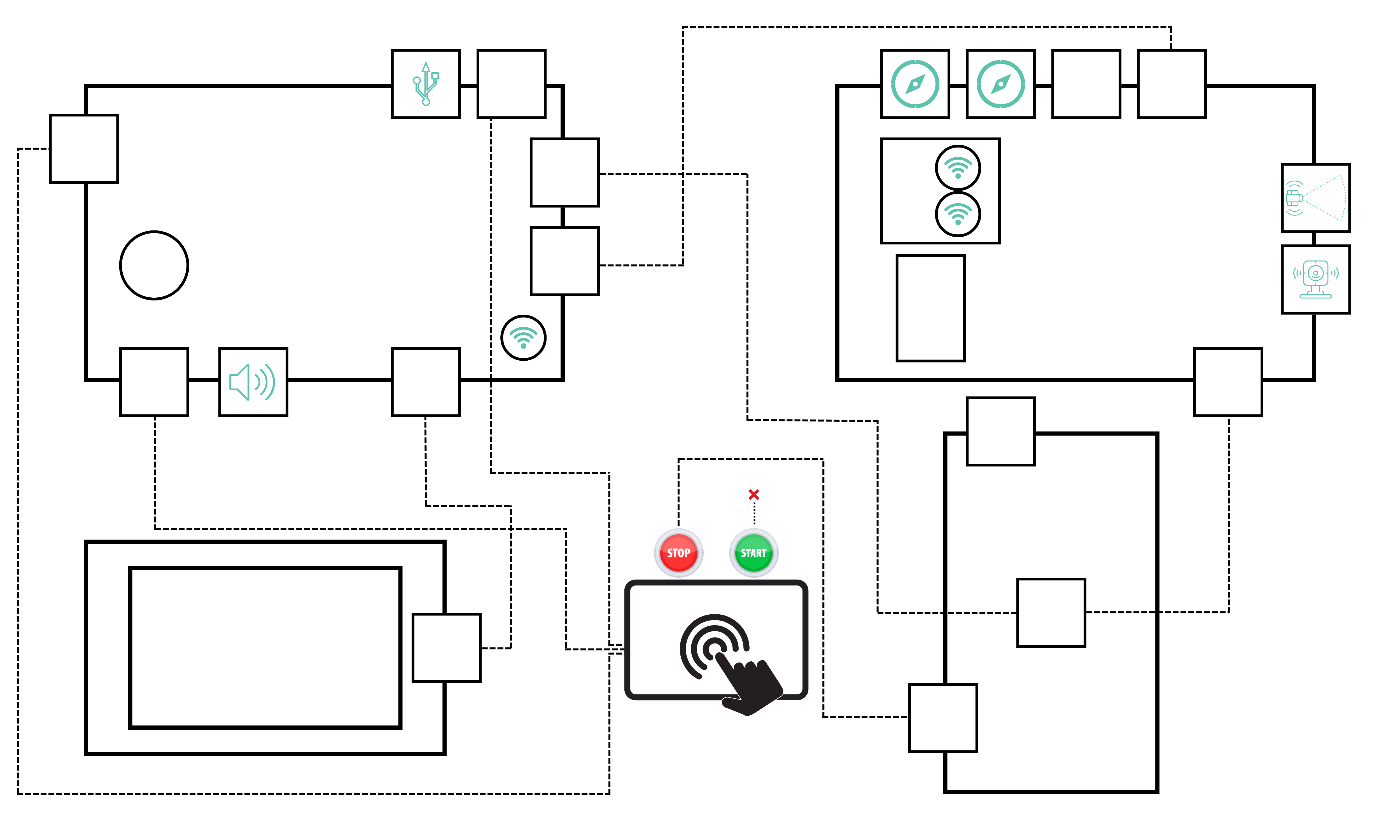
The architecture data flow diagram outlines how different components interact and exchange information within the system. It highlights critical assets and their connections, providing insight into potential vulnerabilities.
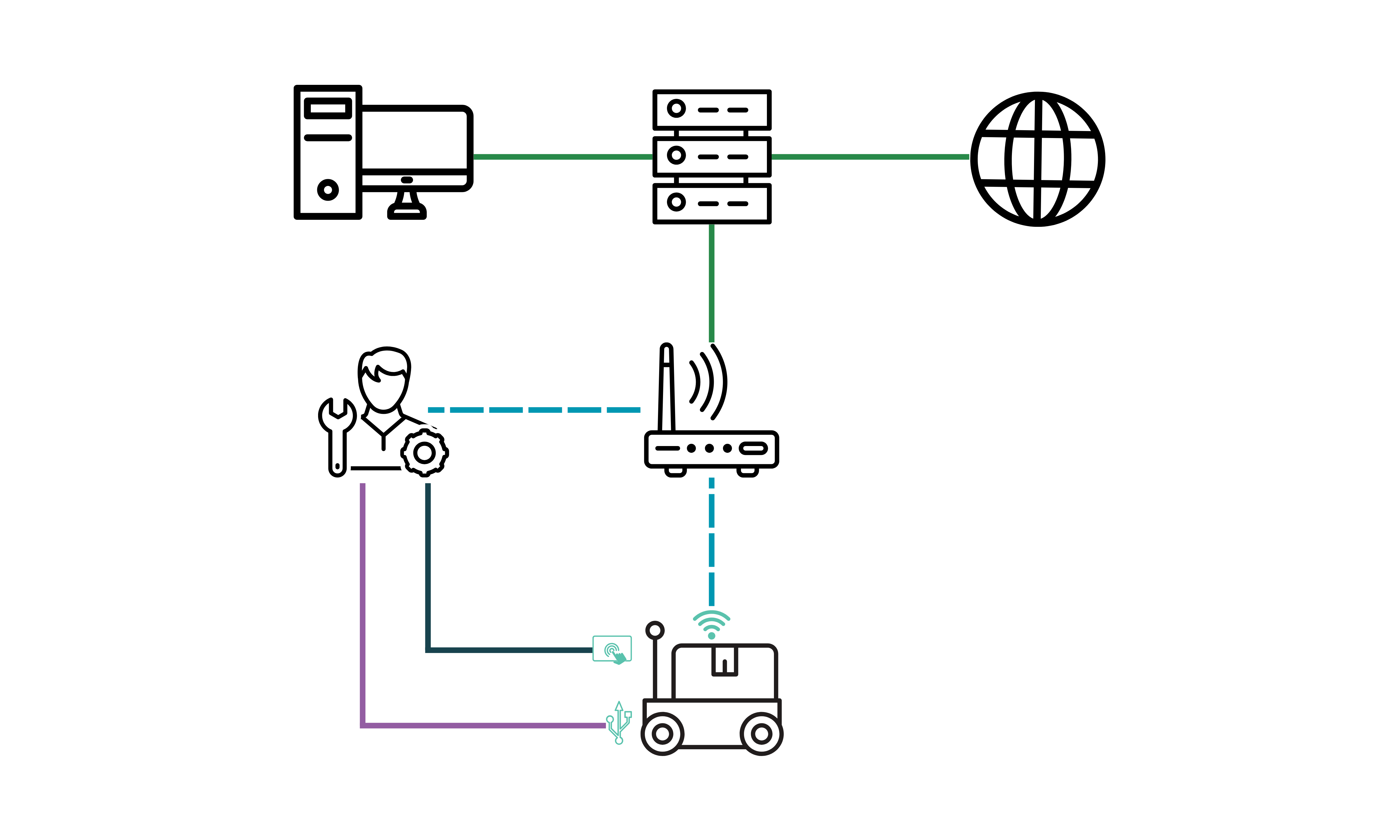
A trust boundary marks areas where multiple entities with different privileges interact. Systems with numerous external interfaces have more complex trust boundaries and larger attack surfaces. The following are the trust boundaries identified in this study:
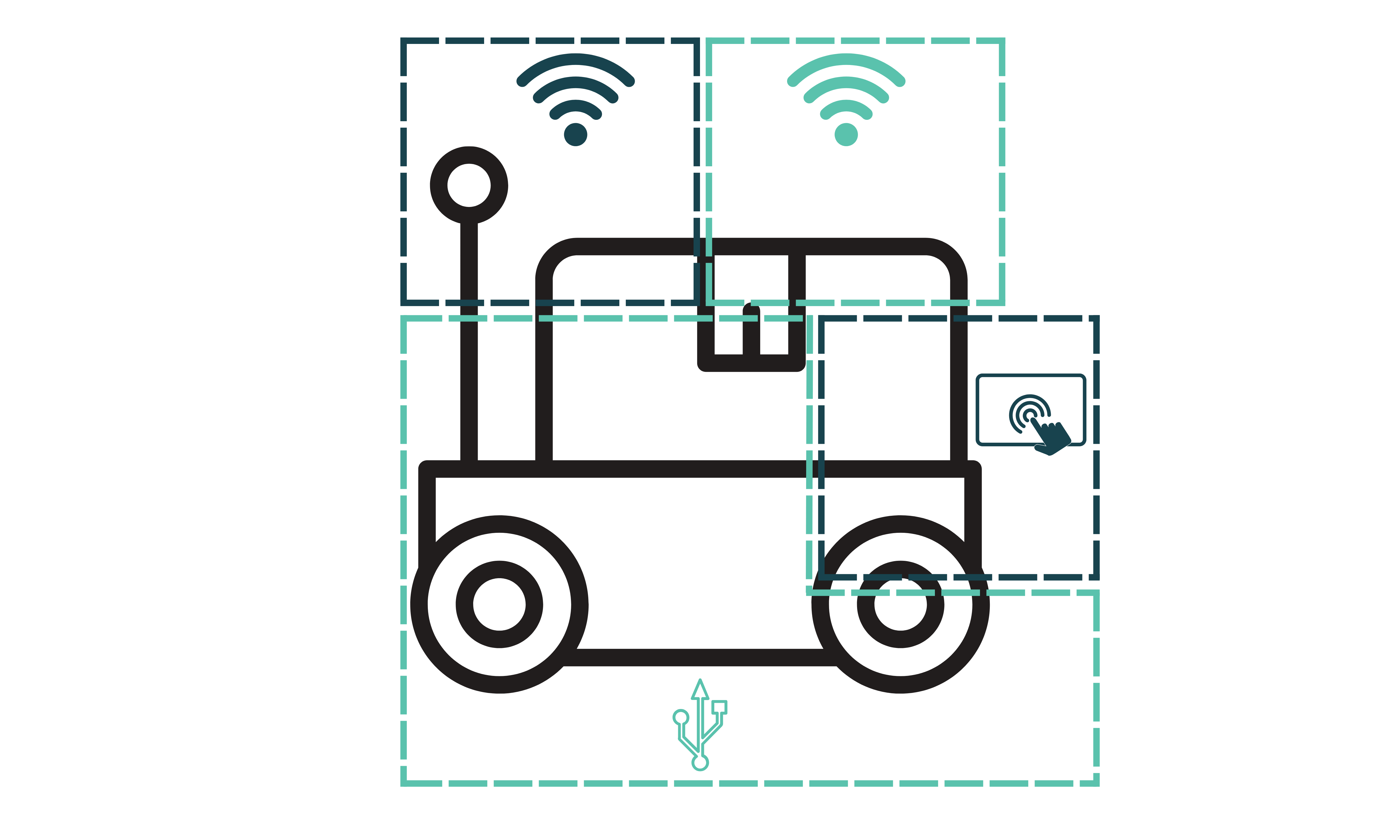
Identified entry points where a malicious actor could initiate an attack:
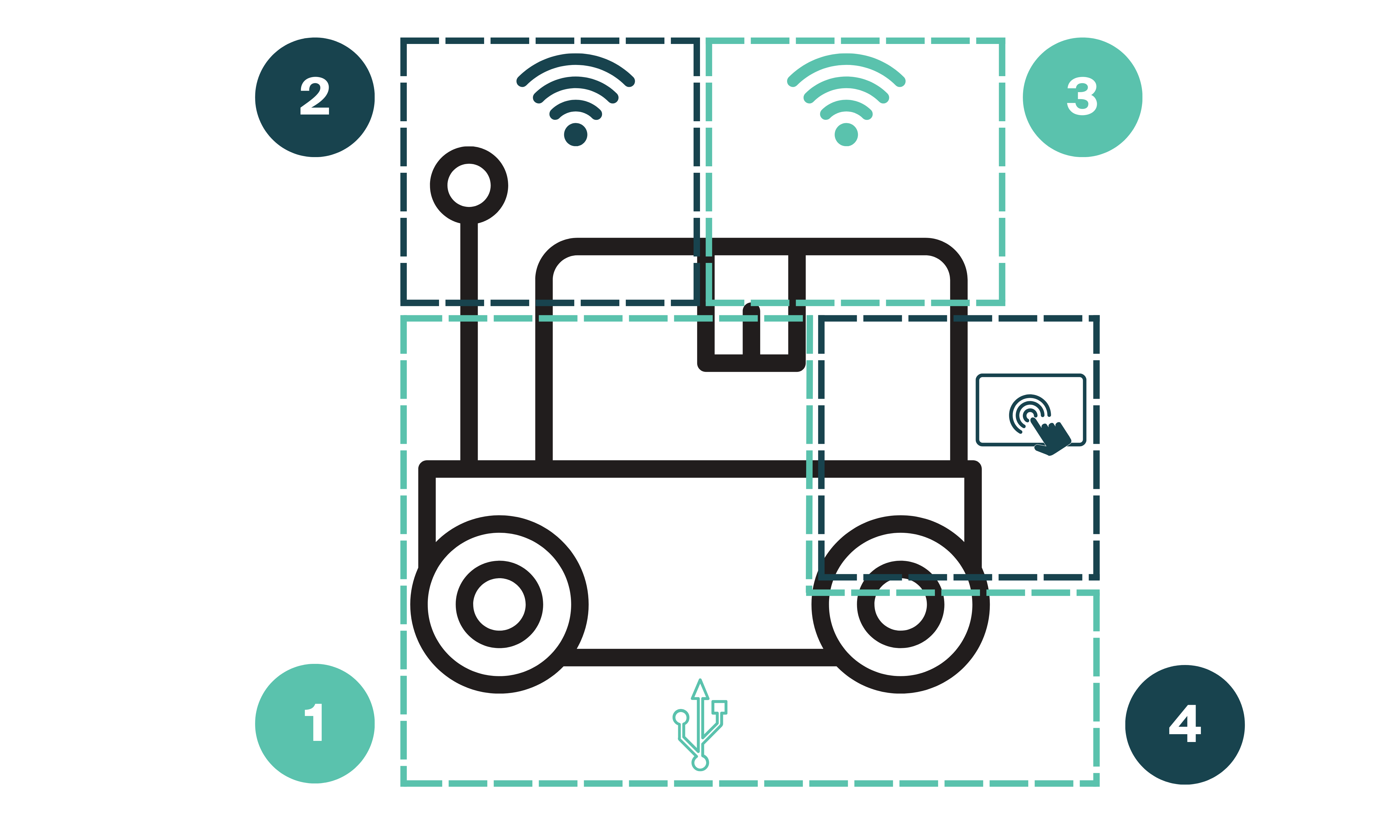
Alias Robotics identified several possible attach pathways affecting PREMIUM AMR1:
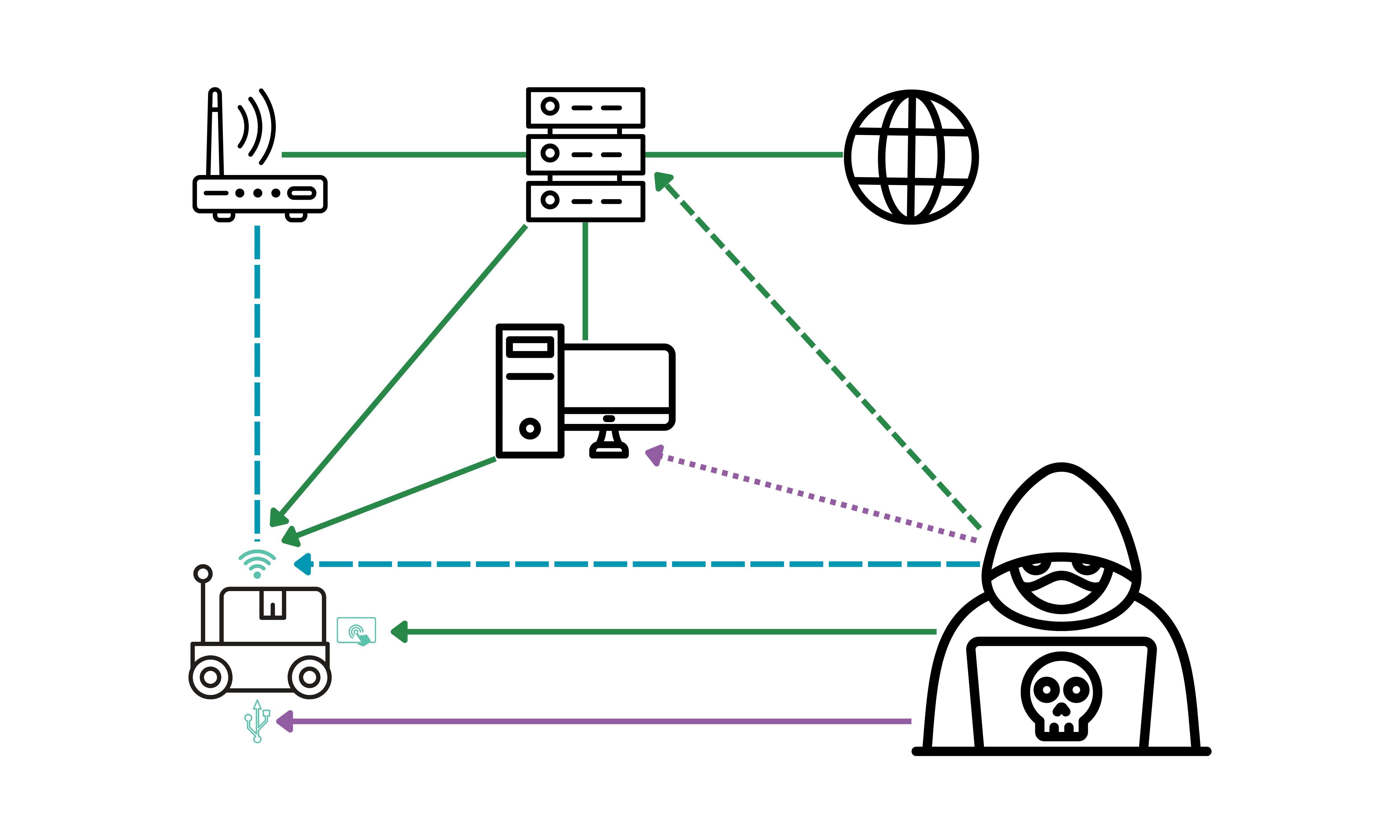
Low cost AMR1 is a highly capable industrial-grade robot with an expanded attack surface, making it a potential target for cybercriminals. Conducting a threat modeling exercise is essential to comply with industrial cybersecurity standards (IEC 62443 Part 4) and mitigate risks effectively.
The next step involves cybersecurity testing of the identified threat landscape to ensure comprehensive protection. Cybersecurity is an iterative process that must be revisited periodically as threats evolve.
Alias Robotics is a leading provider of robot security solutions. Contact us to learn how we can help secure your robotic systems.
Co-Funded by the EIC Accelerator Project – GA 101161136
