



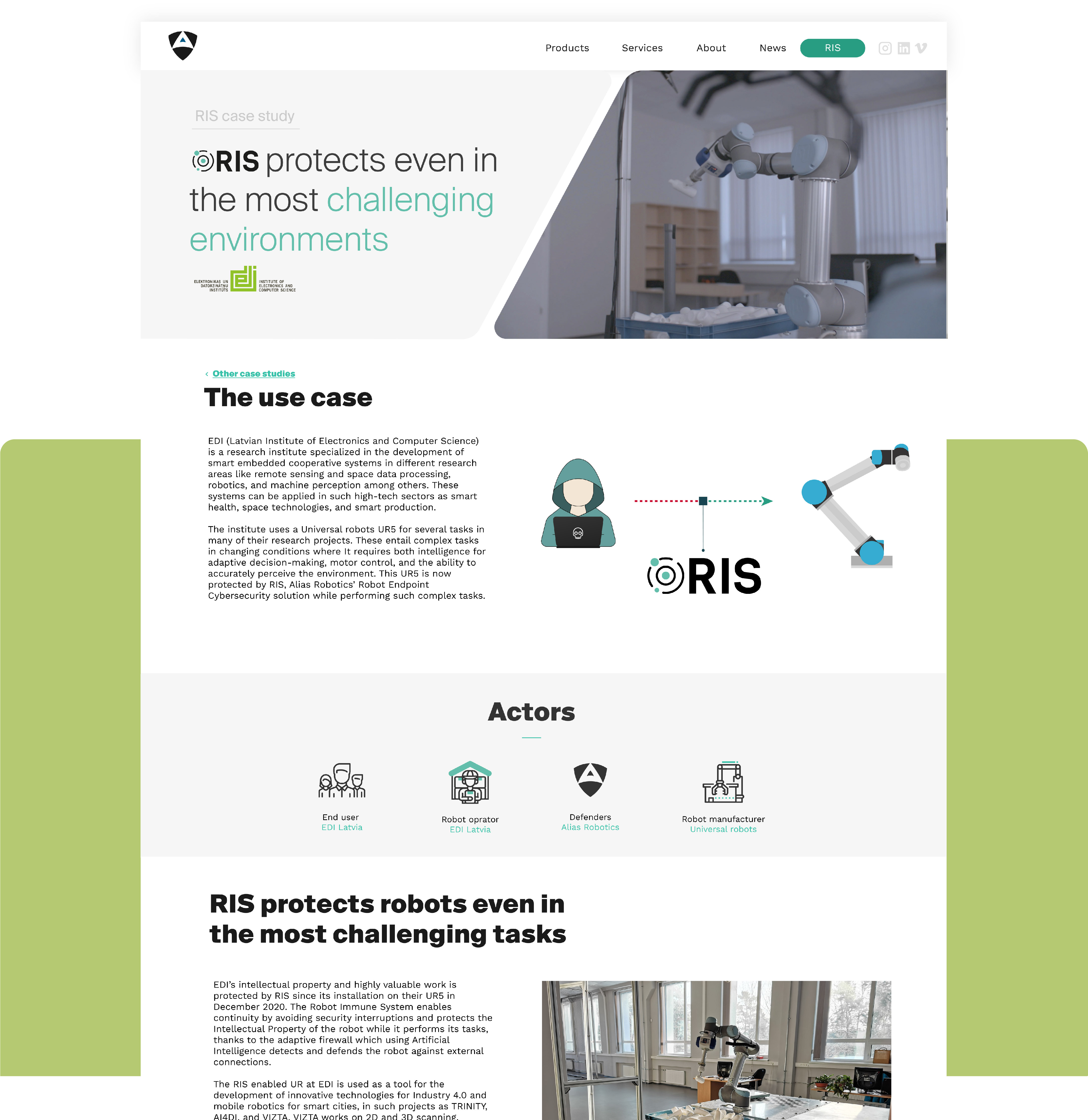
Robots are often deployed in challenging environments where they are subject to a wide variety of attack vectors. From early 2021, RIS protects robots at EDI Latvia ensuring their Intellectual Property remains secure at all times.
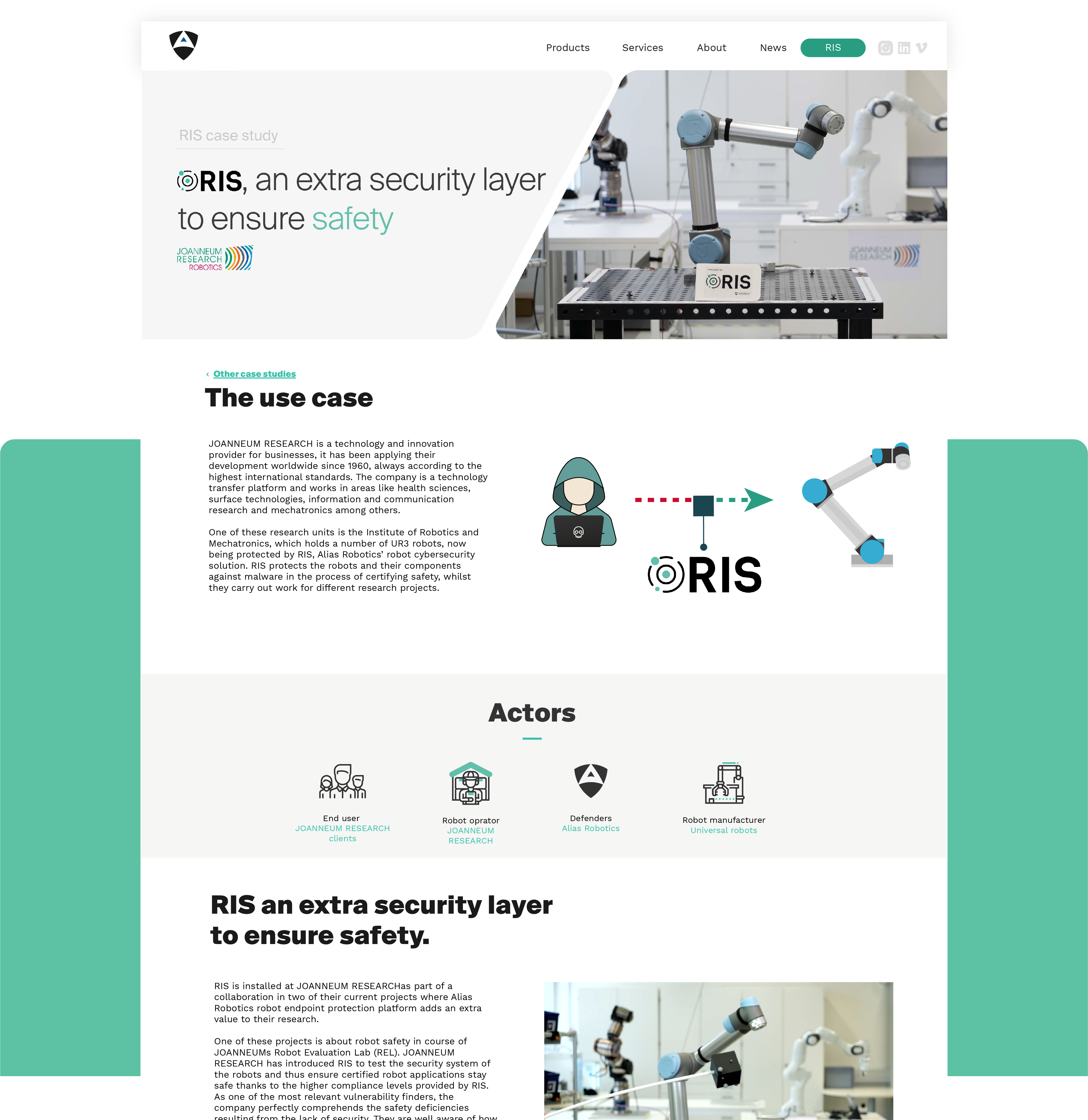
From early 2021, RIS protects robots at Joanneum Research and avoids third party attacks against robotic AI services ensuring data integrity and accuracy during Reinforcement Learning research, deployment and production.
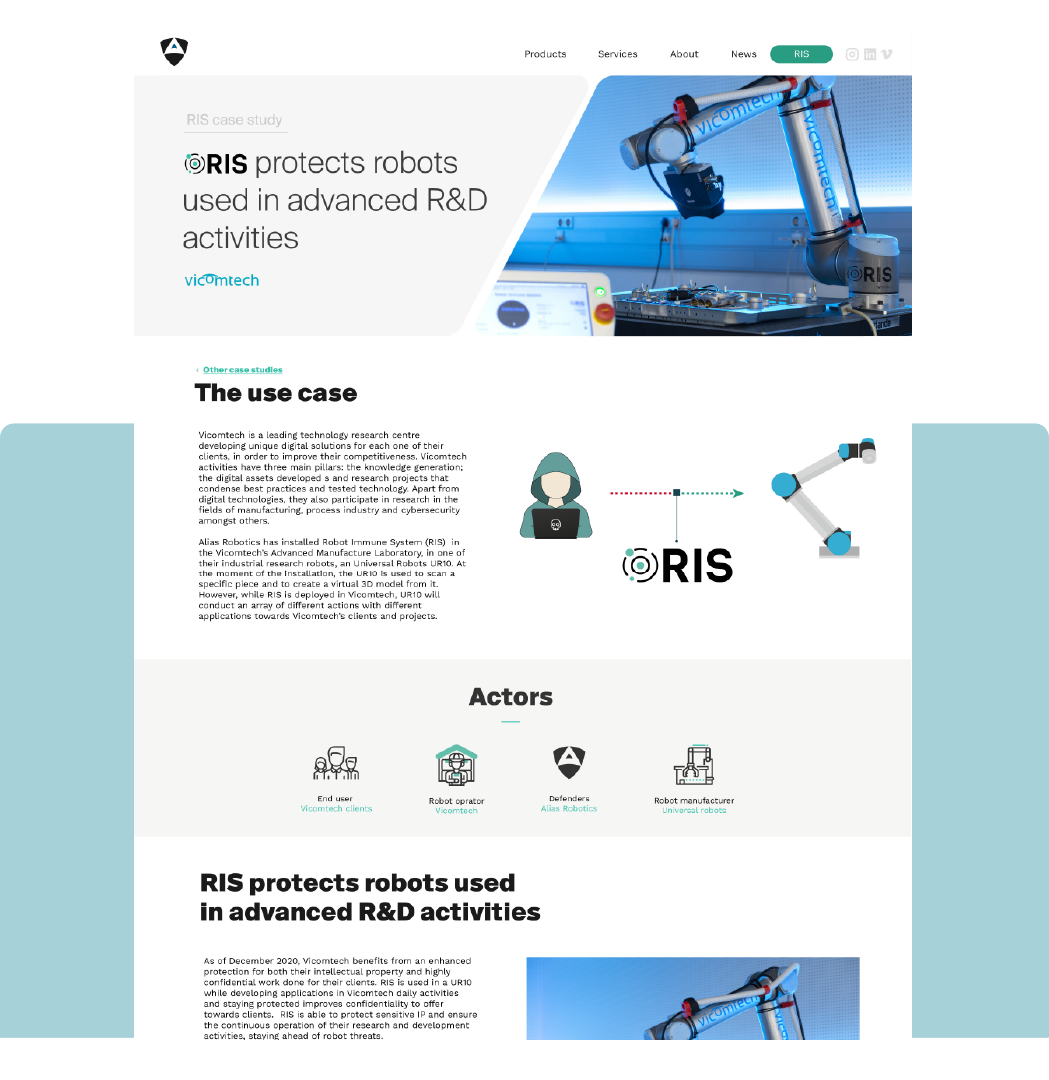
From December 2020 on, RIS is protecting the collaborative robots of Vicomtech's research solutions from cyberattacks, building an additional layer of security into their operations. RIS is deployed in the UR10 series cobots, securing them from cyber-attacks.
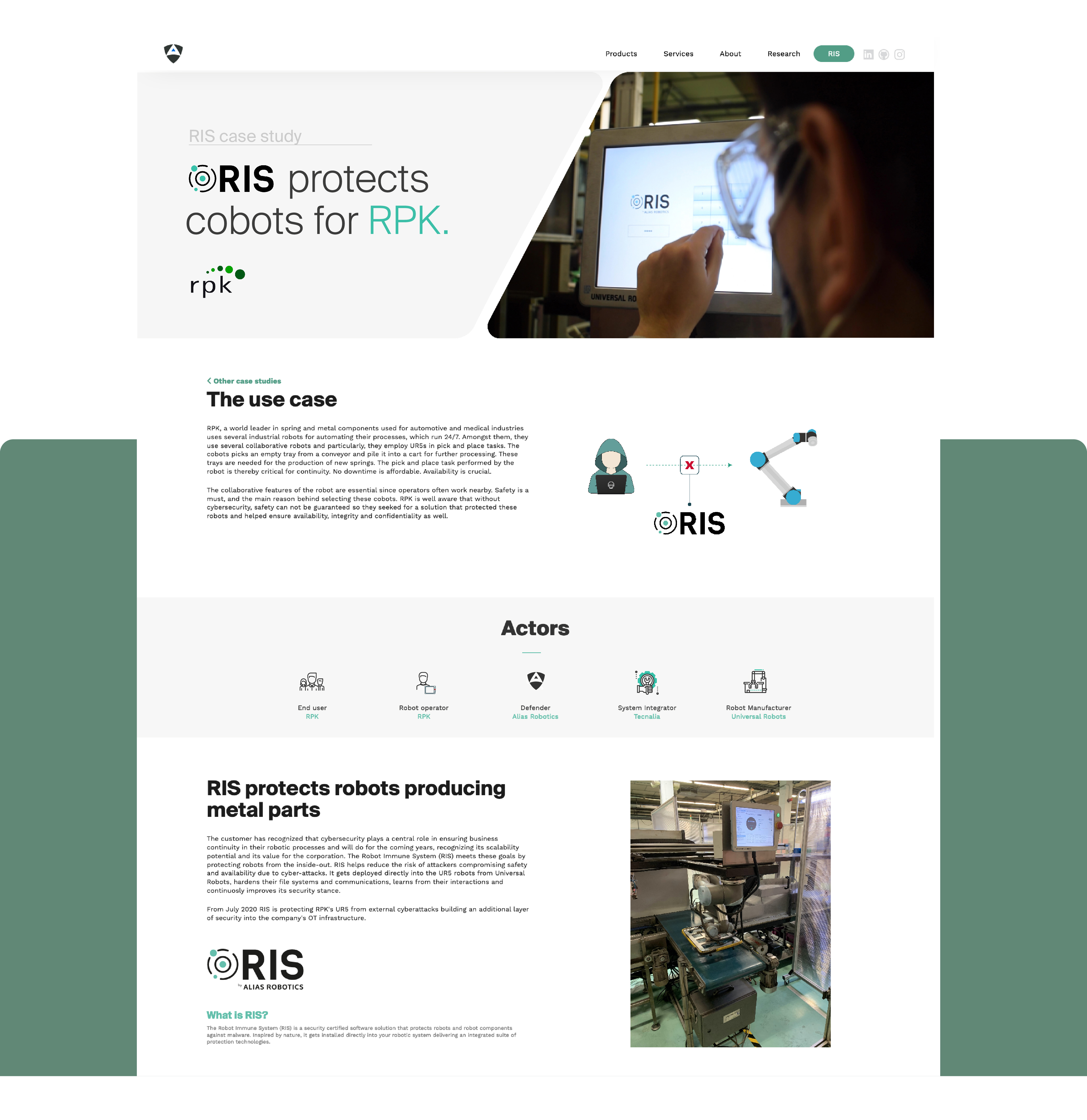
From July 2020, RIS is protecting RPK's collaborative robots from external cyberattacks, building an additional layer of security into the company's OT infrastructure. Through RIS, RPK's robots can now maintain safety requirements and fulfill their tasks securely.
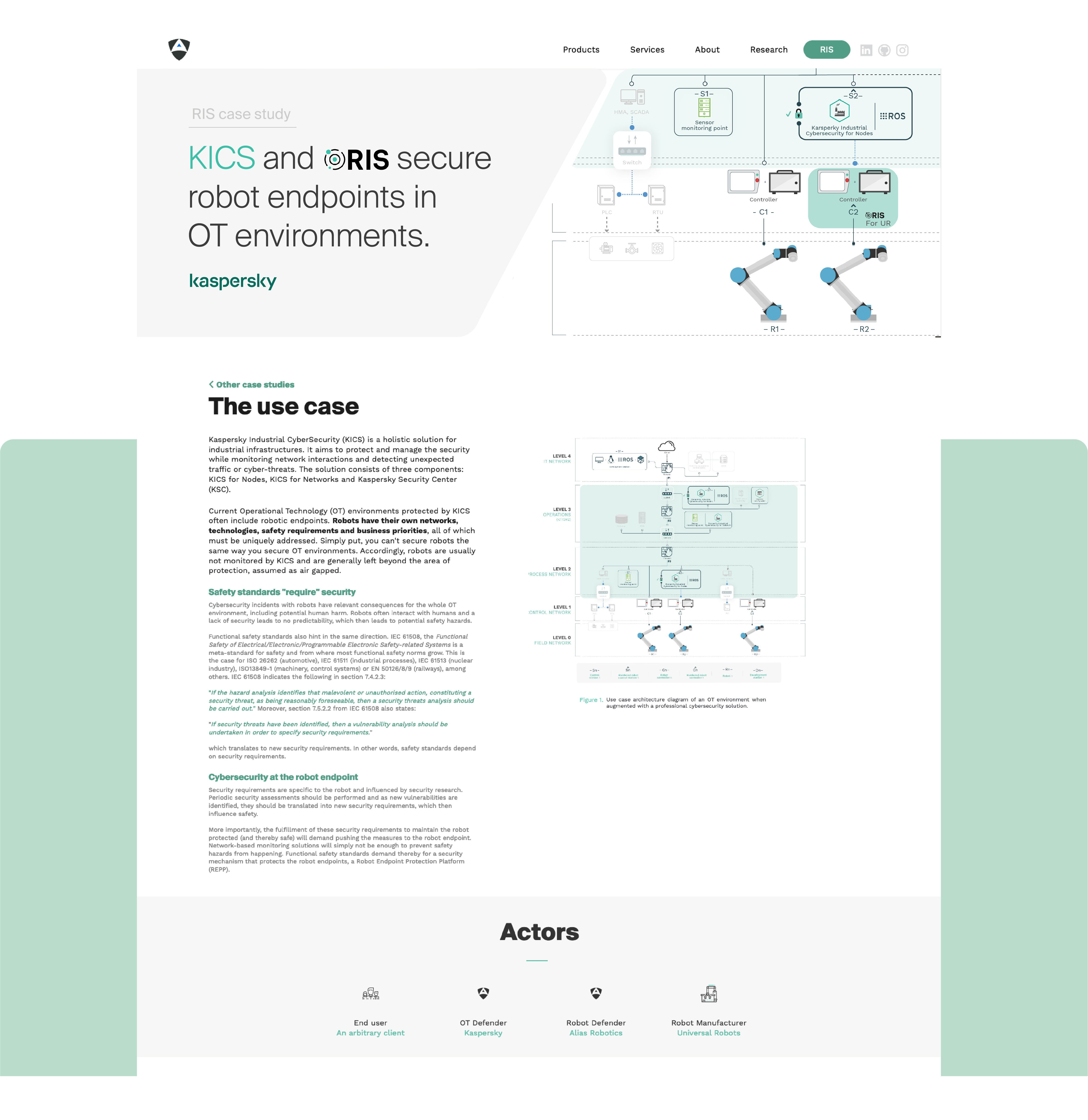
Through a cooperation between Kaspersky and Alias Robotics, we demonstrated technology that helps companies address the challenge of securing OT environments with robots while maintaining their safety requirements.
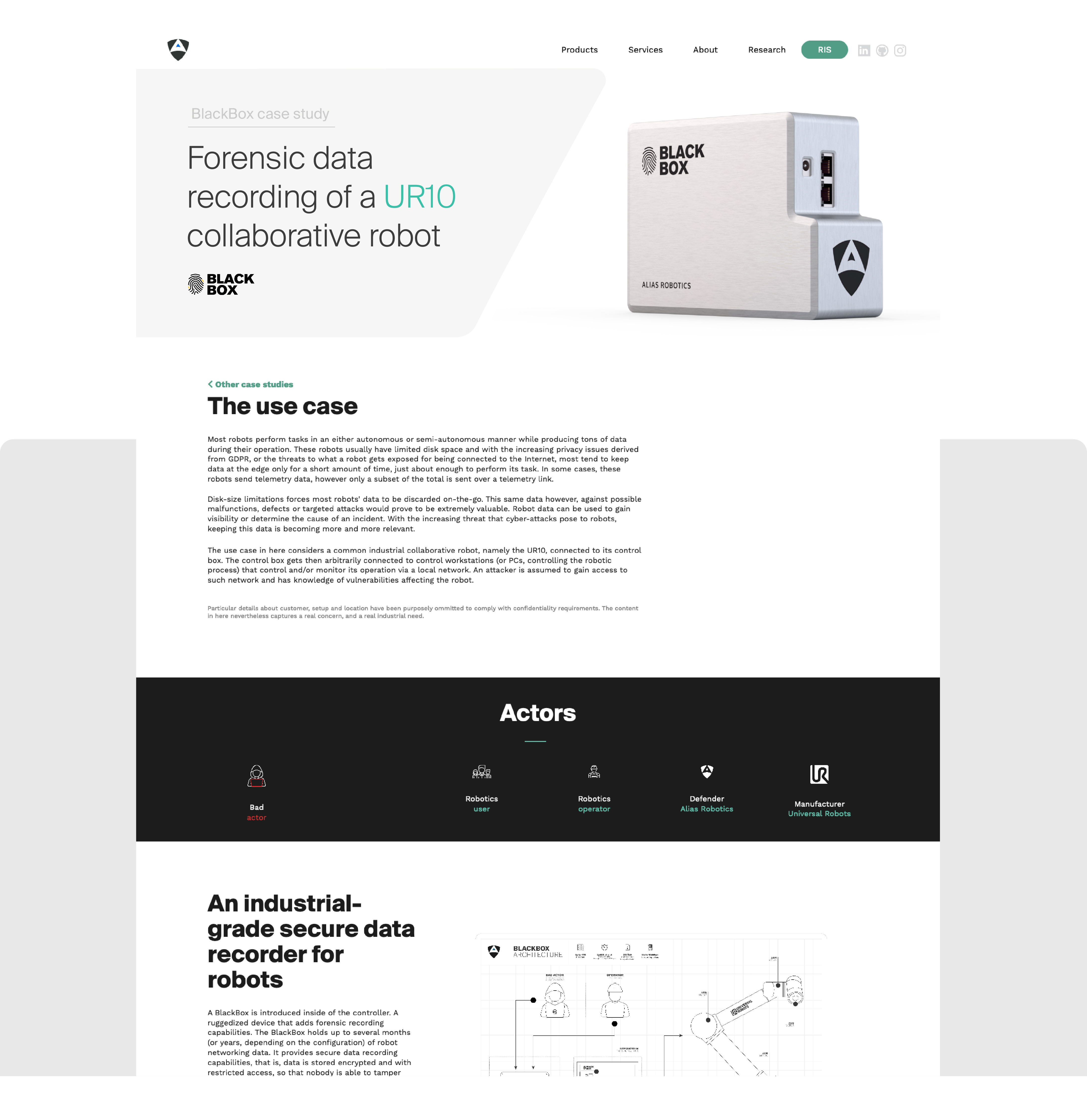
Disk-size limitations forces most robots' data to be discarded on-the-go however this same data is critical against possible malfunctions, defects or attacks. This case study presents the BlackBox forensic recording capabilities for robots.
Can ROS be used securely for industrial use cases? The present study analyzes this question experimentally by performing a targeted offensive security exercise in a synthetic industrial use case involving ROS-Industrial and ROS packages.

After months of failed interactions with MIR and while trying to help secure their robots, Alias decided to empower end-users of Mobile Industrial Robots’ with information and disclosed preliminary results. This case study illustrates the information made available and the consequences of the insecurity.
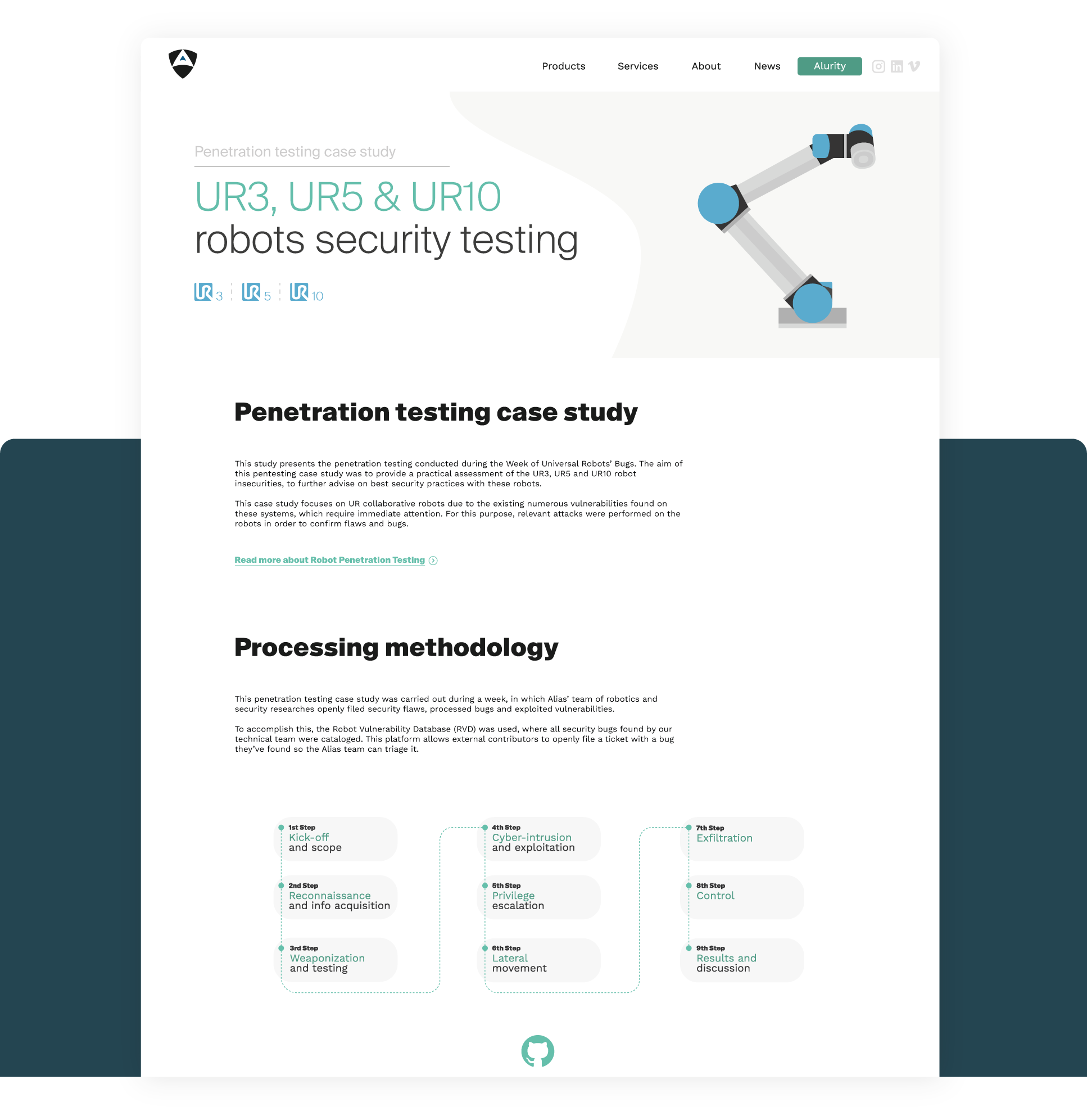
This attack case study presents the penetration testing exercise conducted during the Week of Universal Robots’ Bugs. Our team challenged the security of these robots and developed exploits for identified vulnerabilities, across different firmware versions.
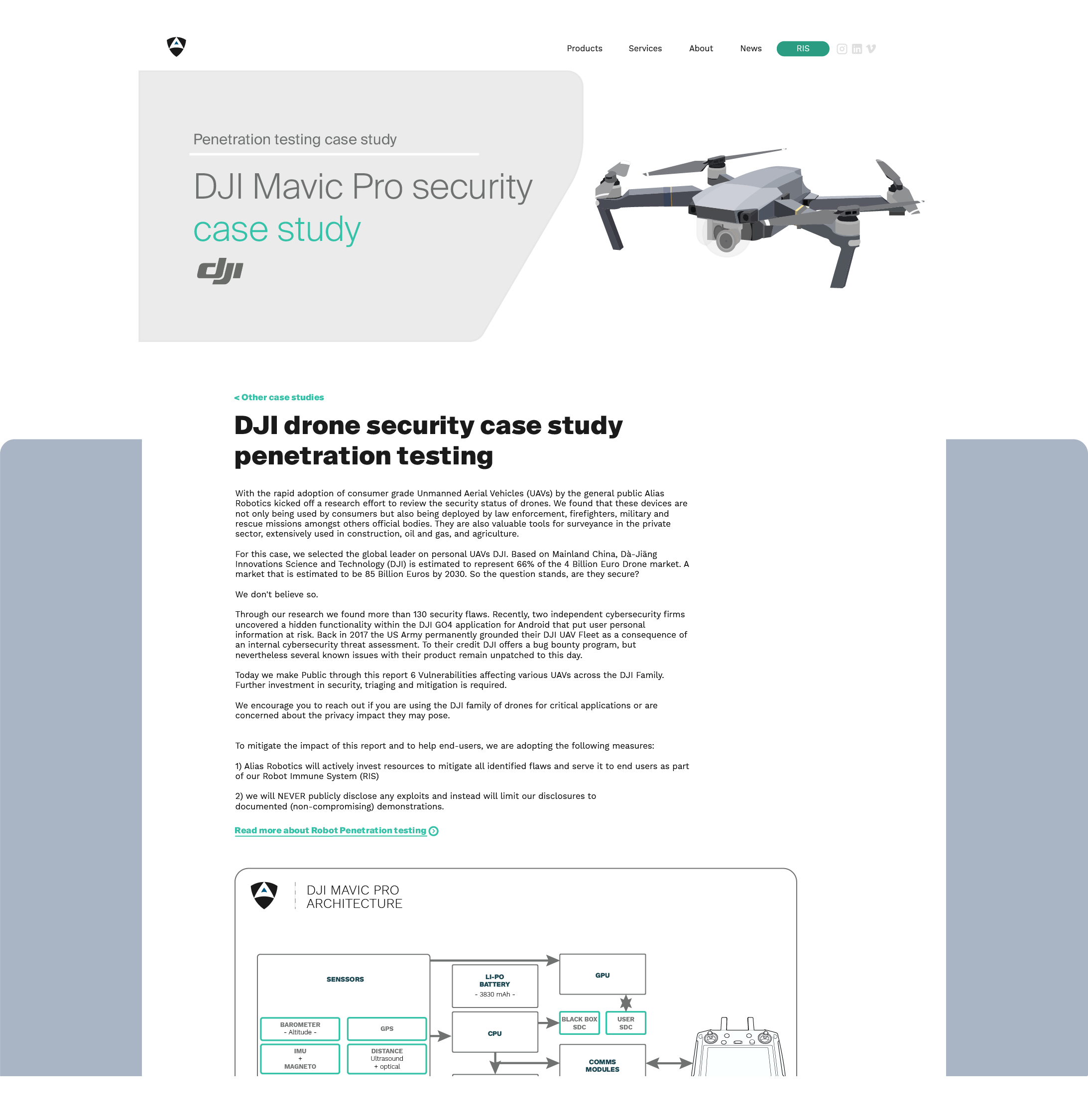
We pentest one of the most popular aerial robots, the DJI Mavic Pro drone and find more than 130 security flaws. Our results indicate that DJI's Bug Bounty program doesn't seem to operate any further and discloses 6 of the triaged flaws assessing their severity.
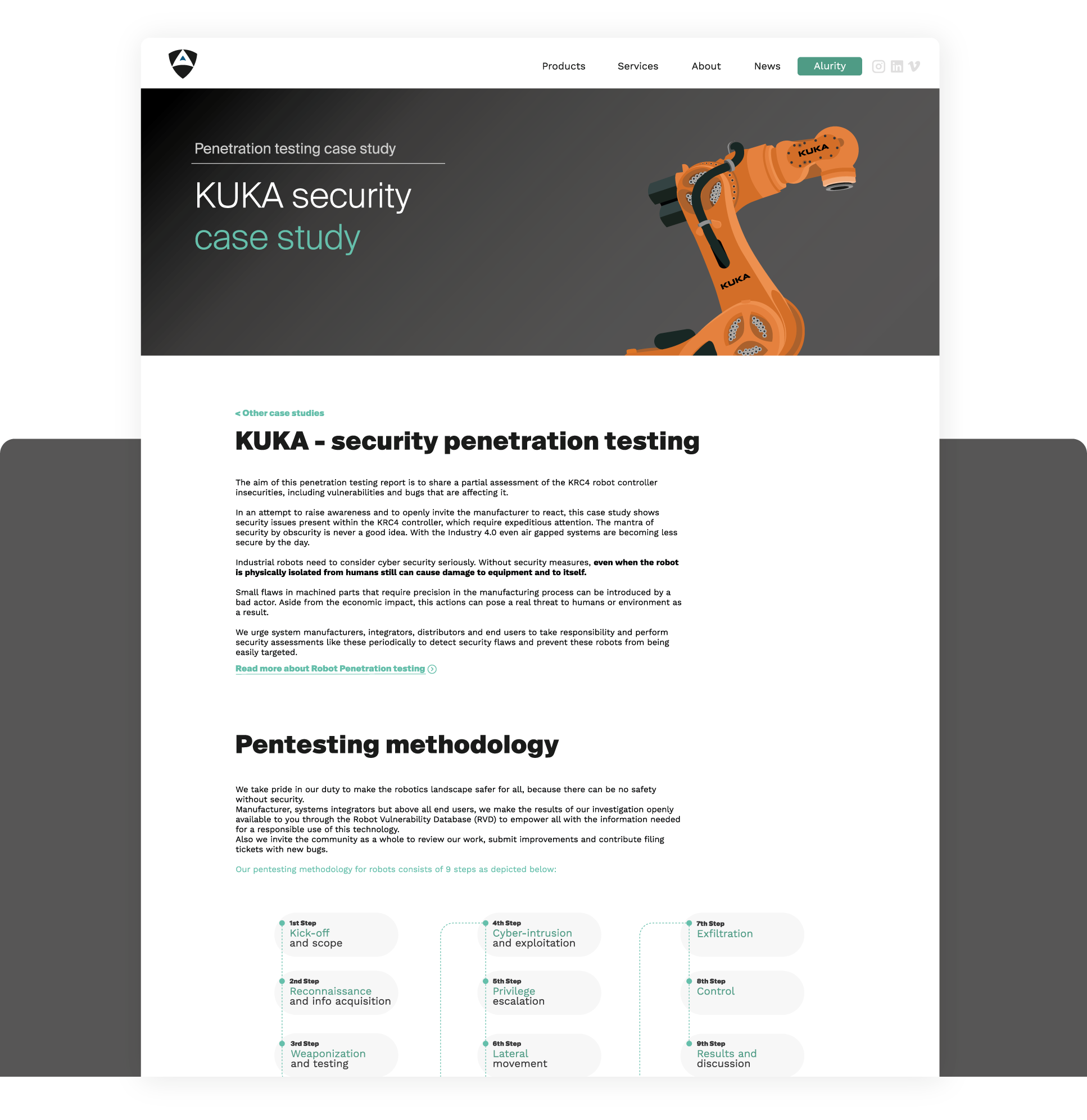
In cooperation with KUKA, the german Federal Cyber Security Authority (BSI) or the Spanish National Cybersecurity Institute (INCIBE) among others, we pentest KUKA's robots and responsibly disclose results hinting that further work is required to protect against hazards.
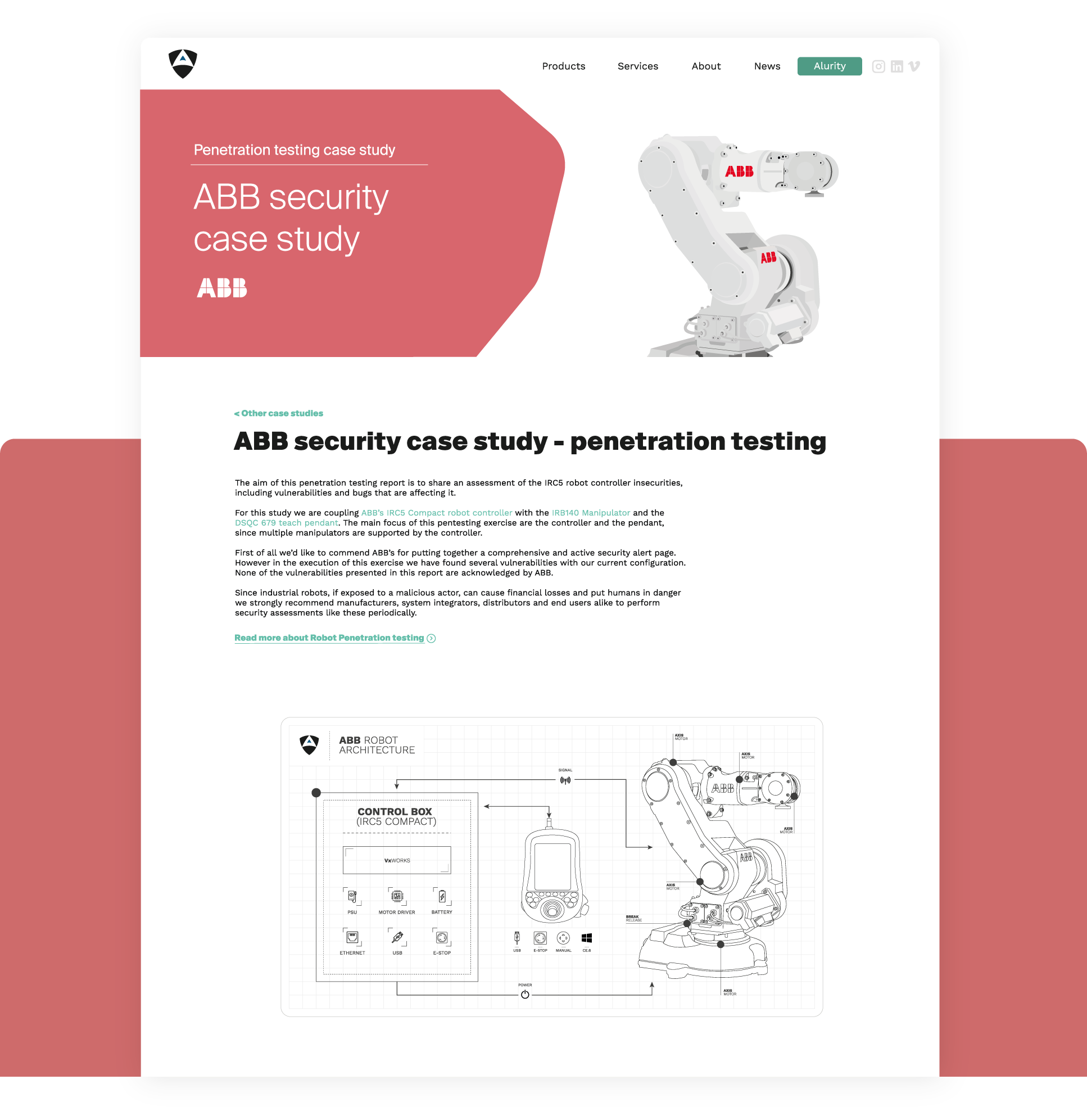
In cooperation with ABB, we tackled several security flaws identified in real deployed robots. We learned that while ABB cares about cyber security, many "older" ABB systems are flawed by both new (0-days) and old vulnerabilities leading to security EoL products.
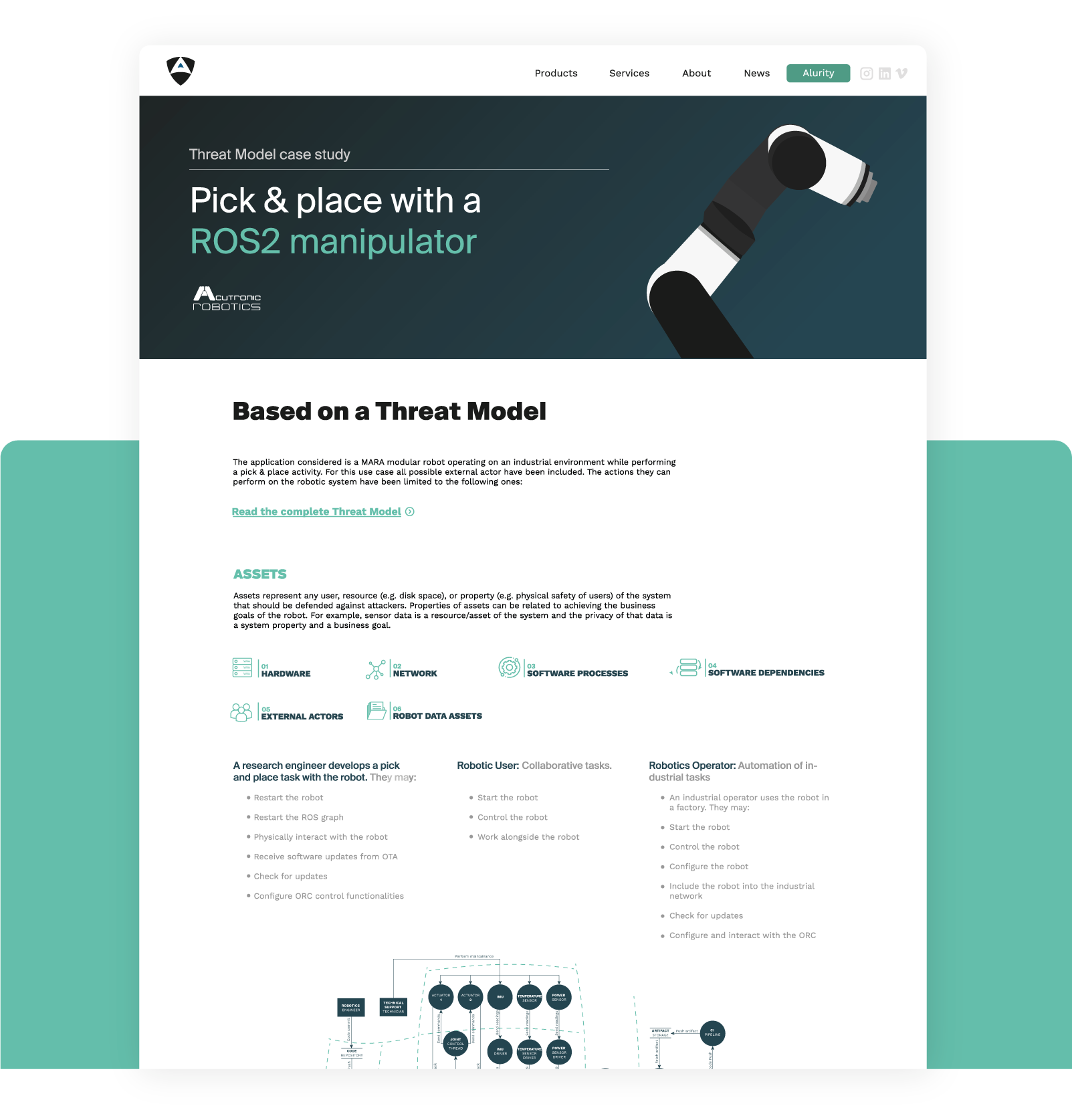
This cyber security case study shows a threat model performed in a fully modular ROS 2 articulated robotic arm. The application considered is MARA, a modular robot operating on an industrial environment while performing a pick & place activity.
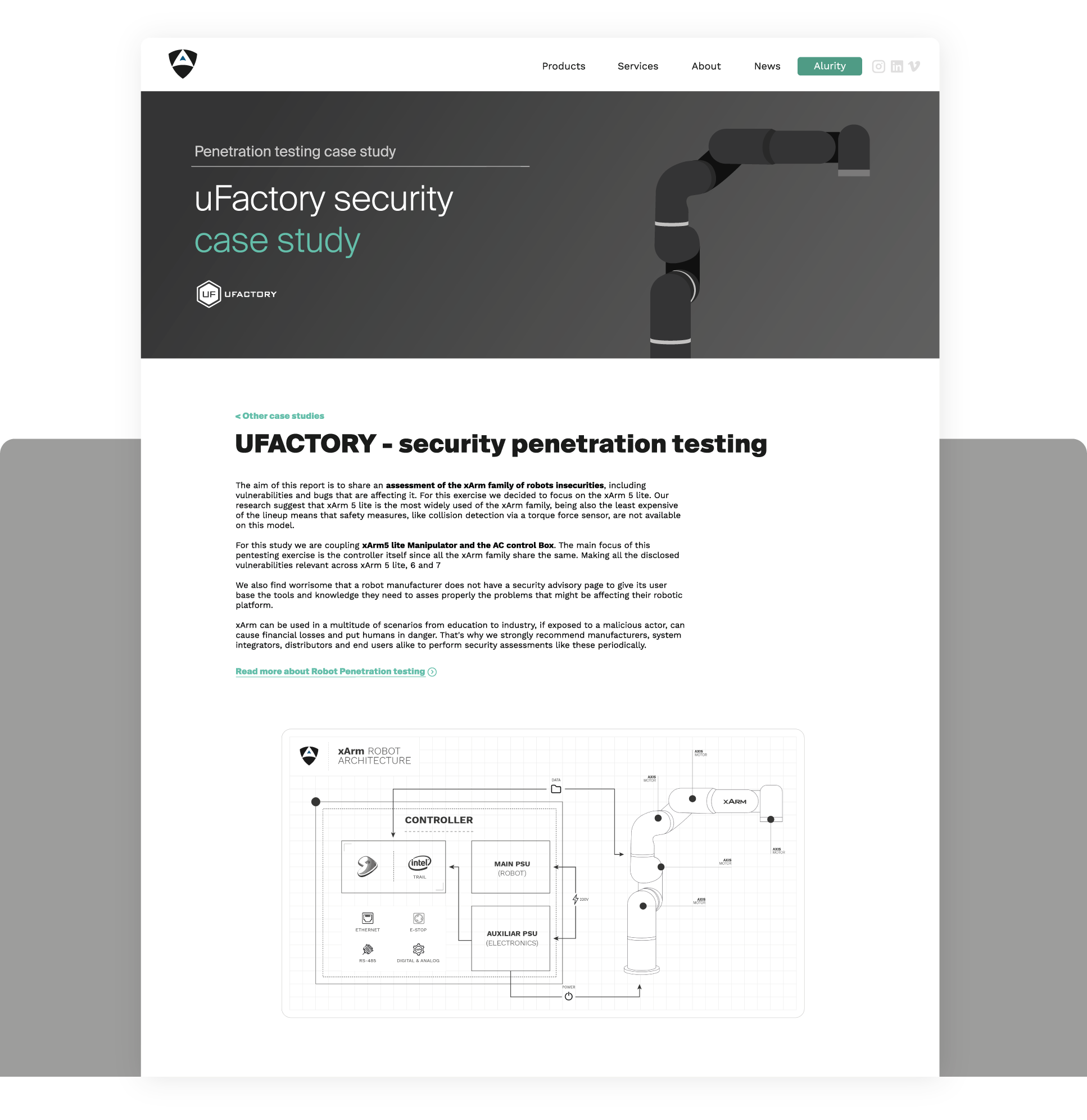
This cyber security case study shows how our team performed a short pentesting activity on a popular and rapidly growing low cost service robot, the UFactory's xArm. We study the xArm family of robots and report on the most representative security flaws.
This study case presents the result of research and a posterior penetration testing exercise conducted on Softbank Robotics humanoid social robots. Building on top of past work, our team studied the security of these robots, and demonstrated the current insecurities.

This cyber security case study presents a brief penetration testing report alongside a novel exploit demonstration affecting the Tello Drone by Ryze and DJI.
Get in touch with our team and we'll do our best to get back to you.
Let's talk